Cybersecurity & Infrastructure Security Agency (CISA) updated its Known Exploited Vulnerabilities Catalog with two vulnerabilities in Cleo Harmony, VLTrader, and LexiCom. Tracked as CVE-2024-50623 & CVE-2024-55956, successful exploitation of the vulnerability may lead to remote code execution. CISA urged users to patch the vulnerabilities before January 3, 2025 (CVE-2024-50623) and January 7, 2025 (CVE-2024-55956).
Cleo first addressed the CVE-2024-50623 on December 10, 2024, with Cleo version 5.8.0.21; however, Huntress identified that the patch was incomplete. Huntress exploited the vulnerability on version 5.8.0.21 and released proof of concept. The fully patched systems running 5.8.0.21 were exploitable. After that, Cleo released version 5.8.0.24 to address the CVE-2024-50623 and CVE-2024-55956.
A quick search revealed more than 3,555,000 targets on Fofa at the time of writing.
Cleo Harmony is a platform that helps businesses transfer data to applications and systems. It is designed for large enterprises and offers file transfer capabilities, system monitoring, scalability, and more features.
Cleo VLTrader software is used to transfer files via secure protocols. This technology resolves ad hoc communication issues, including large files or attachments containing sensitive information.
Cleo LexiCom is a desktop-based file transfer client that helps organizations manage their B2B supply chain integrations.
Exploitation Details
Huntress security researcher observed that the software Harmony, VLTrader, and LexiCom are installed in the root of the filesystem. The installation folders are in the C:\Program Files (x86) directory.
Further analysis of the path: C:\LexiCom\logs\LexiCom.xml revealed that autorun\healthchecktemplate.txt could act as the first point of exploiting the vulnerability. The files in the autorun folder are immediately read, interpreted, evaluated, and deleted after processing. The healthchecktemplate.txt autorun invokes the Import functionality of the Cleo software. The Import process reads in from a local file temp\LexiCom6836057879780436035.tmp on disk. This .tmp file is a .ZIP file containing a subdirectory host with an inner main.xml file.
This main.xml file stages a new autorun to invoke a PowerShell command and gain code execution. The PowerShell command contacts an external IP address to retrieve new JAR files. These JAR files contain webshell-like functionality for persistence on the endpoint that helps in post-exploitation.
Qualys Threat Research Unit reproduced the vulnerability in our labs.
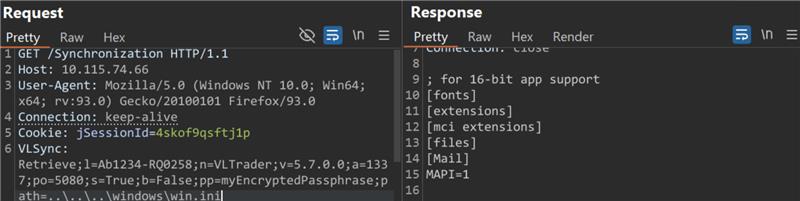
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
- All versions of Cleo Harmony before 5.8.0.24
- All versions of Cleo VLTrader before 5.8.0.24
- All versions of Cleo LexiCom before 5.8.0.24
Mitigation
Customers must upgrade to Cleo version 5.8.0.24 or later to patch the vulnerabilities.
Please refer to the Cleo Product Security Advisories (CVE-2024-50623 and CVE-2024-55956) for more information.
Qualys Detection
Qualys customers can scan their devices with QID 732081 to detect vulnerable assets and QIDs 152529 and 152530 to detect vulnerable web applications.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://support.cleo.com/hc/en-us/articles/28408134019735-Cleo-Product-Security-Update-CVE-2024-55956
https://support.cleo.com/hc/en-us/articles/27140294267799-Cleo-Product-Security-Advisory-CVE-2024-50623
https://www.huntress.com/blog/threat-advisory-oh-no-cleo-cleo-software-actively-being-exploited-in-the-wild