Happy New Year! As the calendar turns to January 2025, Microsoft’s first Patch Tuesday of 2025 has arrived. From zero-days to critical vulnerabilities, here’s what deserves your attention. Here’s a breakdown of what’s been patched.
Microsoft Patch’s Tuesday, January 2025 edition addressed 159 vulnerabilities, including 10 critical and 149 important severity vulnerabilities. In this month’s updates, Microsoft has addressed eight zero-day vulnerabilities, three of which have been actively exploited in attacks.
Microsoft has not addressed any vulnerability in Microsoft Edge (Chromium-based) in this month’s updates.
Microsoft Patch Tuesday, January edition includes updates for vulnerabilities in .NET, .NET and Visual Studio, Microsoft Windows Search Component, Windows Installer, Windows Kerberos, Windows Kernel Memory, Windows Remote Desktop Services, Windows Secure Boot, and more.
Microsoft has fixed several flaws in multiple software, including Spoofing, Denial of Service (DoS), Elevation of Privilege (EoP), Security Feature Bypass, Information Disclosure, and Remote Code Execution (RCE).
The January 2025 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 5 | Important: 5 |
| Denial of Service Vulnerability | 20 | Important: 20 |
| Elevation of Privilege Vulnerability | 40 | Critical: 1 Important: 39 |
| Information Disclosure Vulnerability | 22 | Important: 22 |
| Remote Code Execution Vulnerability | 58 | Critical: 9 Important: 49 |
| Security Feature Bypass | 14 | Important: 14 |
Zero-day Vulnerabilities Patched in January Patch Tuesday Edition
CVE-2025-21333, CVE-2025-21334, & CVE-2025-21335: Windows Hyper-V NT Kernel Integration VSP Elevation of Privilege Vulnerability
Windows Hyper-V NT Kernel Integration VSP refers to the Virtualization Service Provider component within the Hyper-V virtualization platform on Windows. The tool acts as a bridge between the Hyper-V hypervisor and the Windows NT kernel, allowing seamless communication and management of virtual machines running on the host system.
Successful exploitation of the vulnerability could allow an attacker to SYTEM privileges.
CISA added the CVE-2025-21333, CVE-2025-21334, & CVE-2025-21335 to the Known Exploited Vulnerabilities Catalog, acknowledging its active exploitation. CISA urged users to patch the vulnerability before February 4, 2025.
CVE-2025-21366, CVE-2025-21395, & CVE-2025-21186: Microsoft Access Remote Code Execution Vulnerability
Microsoft Access is a database management system (DBMS) that helps users store, organize, and analyze data. Microsoft Access stores data in its format, or it can import or link to data from other applications.
Microsoft addressed the vulnerabilities by blocking access to the following extensions:
- accdb
- accde
- accdw
- accdt
- accda
- accdr
- accdu
CVE-2025-21275: Windows App Package Installer Elevation of Privilege Vulnerability
A Windows App Package Installer, often called App Installer, is a built-in component of the Windows operating system that allows users to install applications easily.
An attacker could gain SYSTEM privileges upon successful exploitation of the vulnerability.
CVE-2025-21308: Windows Themes Spoofing Vulnerability
Windows themes are a combination of colors, sounds, and pictures that you can use to personalize your Windows PC.
Successful exploitation of the vulnerability requires an attacker to convince the user to load a malicious file onto a vulnerable system.
Critical Severity Vulnerabilities Patched in January Patch Tuesday Edition
CVE-2025-21294: Microsoft Digest Authentication Remote Code Execution Vulnerability
Microsoft Digest Authentication is a security mechanism that uses a challenge-response protocol to verify user credentials without sending the actual password in plain text over the network.
An attacker must win a race condition to exploit the vulnerability. An attacker could exploit this vulnerability by connecting to a system that requires digest authentication. This will trigger the race condition to create a use-after-free scenario, leading to arbitrary code execution.
CVE-2025-21295: SPNEGO Extended Negotiation (NEGOEX) Security Mechanism Remote Code Execution Vulnerability
SPNEGO Extended Negotiation (NEGOEX) is a security mechanism that extends the Simple and Protected GSSAPI Negotiation Mechanism (SPNEGO) capabilities. The mechanism allows clients and servers to negotiate a standard authentication protocol based on additional metadata like trust configurations.
An attacker must manipulate system operations in a specific manner to exploit the vulnerability. Upon successful exploitation, an attacker could achieve remote code execution without user interaction.
CVE-2025-21296: BranchCache Remote Code Execution Vulnerability
BranchCache is a Windows feature that optimizes wide area network (WAN) bandwidth by caching content on local computers in branch offices.
An attacker must win a race condition to exploit the vulnerability.
CVE-2025-21297 & CVE-2025-21309: Windows Remote Desktop Services Remote Code Execution Vulnerability
Windows Remote Desktop Services (RDS) is a Microsoft feature that allows users to access and control a remote computer’s desktop and applications over a network connection.
An attacker must win a race condition to exploit the vulnerabilities. An attacker could exploit these vulnerabilities by connecting to a system with the Remote Desktop Gateway role. Then, it would trigger the race condition to create a use-after-free scenario, ultimately leading to arbitrary code execution.
CVE-2025-21298: Windows OLE Remote Code Execution Vulnerability
Object Linking and Embedding (OLE) is a Microsoft Windows standard that allows users to create and edit documents that contain objects from multiple applications.
An attacker may exploit the vulnerability in an email attack scenario by sending a specially crafted email to the victim. The victim must open a specially crafted email with an affected Microsoft Outlook software version for successful exploitation. Upon successful exploitation, an attacker can achieve remote code execution on the victim’s machine.
CVE-2025-21307: Windows Reliable Multicast Transport Driver (RMCAST) Remote Code Execution Vulnerability
The Windows Reliable Multicast Transport Driver (RMCAST) is a component within the Windows operating system that enables reliable multicast data transmission.
An unauthenticated attacker could exploit the vulnerability by sending specially crafted packets to a Windows Pragmatic General Multicast (PGM) open socket on the server without any interaction from the user.
CVE-2025-21311: Windows NTLM V1 Elevation of Privilege Vulnerability
Windows NTLM V1 (NT LAN Manager Version 1) is a Microsoft authentication protocol used for network logins on Windows systems.
Successful exploration of the vulnerability could allow an attacker to escalate privileges.
CVE-2025-21354 & CVE-2025-21362: Microsoft Excel Remote Code Execution Vulnerability
Microsoft Excel is a spreadsheet program that helps users organize and analyze data. It’s available on Windows, macOS, Android, iOS, and iPadOS.
Successful exploitation of the vulnerability could allow an attacker to achieve remote code execution of vulnerable targets.
Other Microsoft Vulnerability Highlights
- CVE-2025-21210 is an information disclosure vulnerability in Windows BitLocker. Successful exploitation of the vulnerability could allow an attacker to disclose unencrypted hibernation images in cleartext.
- CVE-2025-21268, CVE-2025-21219, CVE-2025-21189, CVE-2025-21328, & CVE-2025-21329 are security feature bypass vulnerabilities in MapUrlToZone. Upon successful exploitation, an attacker could bypass the MapURLToZone method to view some sensitive information.
- CVE-2025-21269 is a security feature bypass vulnerability in Windows HTML Platforms. Successful exploitation of the vulnerability could allow an attacker to view some sensitive information.
- CVE-2025-21292 is an elevation of privilege vulnerability in Windows Search Service. Successful exploitation of the vulnerability could allow an attacker to gain SYSTEM privileges.
- CVE-2025-21299 is a security feature bypass vulnerability in Windows Kerberos. Successful exploitation of the vulnerability could allow an attacker to bypass Windows Defender Credential Guard Feature to leak Kerberos Credential.
- CVE-2025-21314 is a spoofing vulnerability in Windows SmartScreen. To successfully exploit the vulnerability, an attacker must send the victim a malicious file that the victim would have to execute.
- CVE-2025-21315 is an elevation of privilege vulnerability in the Microsoft Brokering File System. Upon successful exploitation, an attacker could potentially gain the ability to crash the system by exploiting the use-after-free vulnerability.
- CVE-2025-21364 is a security feature bypass vulnerability in Microsoft Excel. Successful exploitation of the vulnerability may allow an attacker to bypass Office macro policies used to block untrusted or malicious files.
- CVE-2025-21365 is a remote code execution vulnerability in Microsoft Office. Successful exploitation of the vulnerability may allow an attacker to achieve remote code execution.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, .NET, .NET Framework, Visual Studio; Visual Studio, Microsoft Office Access, Power Automate, Windows MapUrlToZone, Active Directory Federation Services, Windows Recovery Environment Agent, Windows Connected Devices Platform Service, Windows Virtual Trusted Platform Module, Windows Boot Loader, Windows BitLocker, Windows Boot Manager, Windows Mark of the Web (MOTW), Windows Message Queuing, Windows Telephony Service, Line Printer Daemon Service (LPD), Windows Digital Media, IP Helper, Windows PrintWorkflowUserSvc, Windows WLAN Auto Config Service, Windows Cloud Files Mini Filter Driver, Windows COM, Windows Event Tracing, Windows Direct Show, Active Directory Domain Services, Microsoft Digest Authentication, Windows SPNEGO Extended Negotiation, BranchCache, Windows OLE, Windows UPnP Device Host, Windows Geolocation Service, Windows DWM Core Library, Reliable Multicast Transport Driver (RMCAST), Windows Themes, Windows NTLM, Windows Smart Card, Windows Security Account Manager, Windows SmartScreen, Microsoft Brokering File System, Internet Explorer, Windows Hyper-V NT Kernel Integration VSP, Windows Cryptographic Services, Windows Win32K – GRFX, Windows Hello, Windows Web Threat Defense User Service, Microsoft Office SharePoint, Microsoft Office Visio, Microsoft Office, Microsoft Office Excel, Microsoft Office Outlook, Microsoft AutoUpdate (MAU), Microsoft Office Outlook for Mac, Microsoft Office Word, Windows Virtualization-Based Security (VBS) Enclave, Windows Client-Side Caching (CSC) Service, Azure Marketplace SaaS Resources, Microsoft Graphics Component, Microsoft Purview, Microsoft Office OneNote, and Microsoft Azure Gateway Manager.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
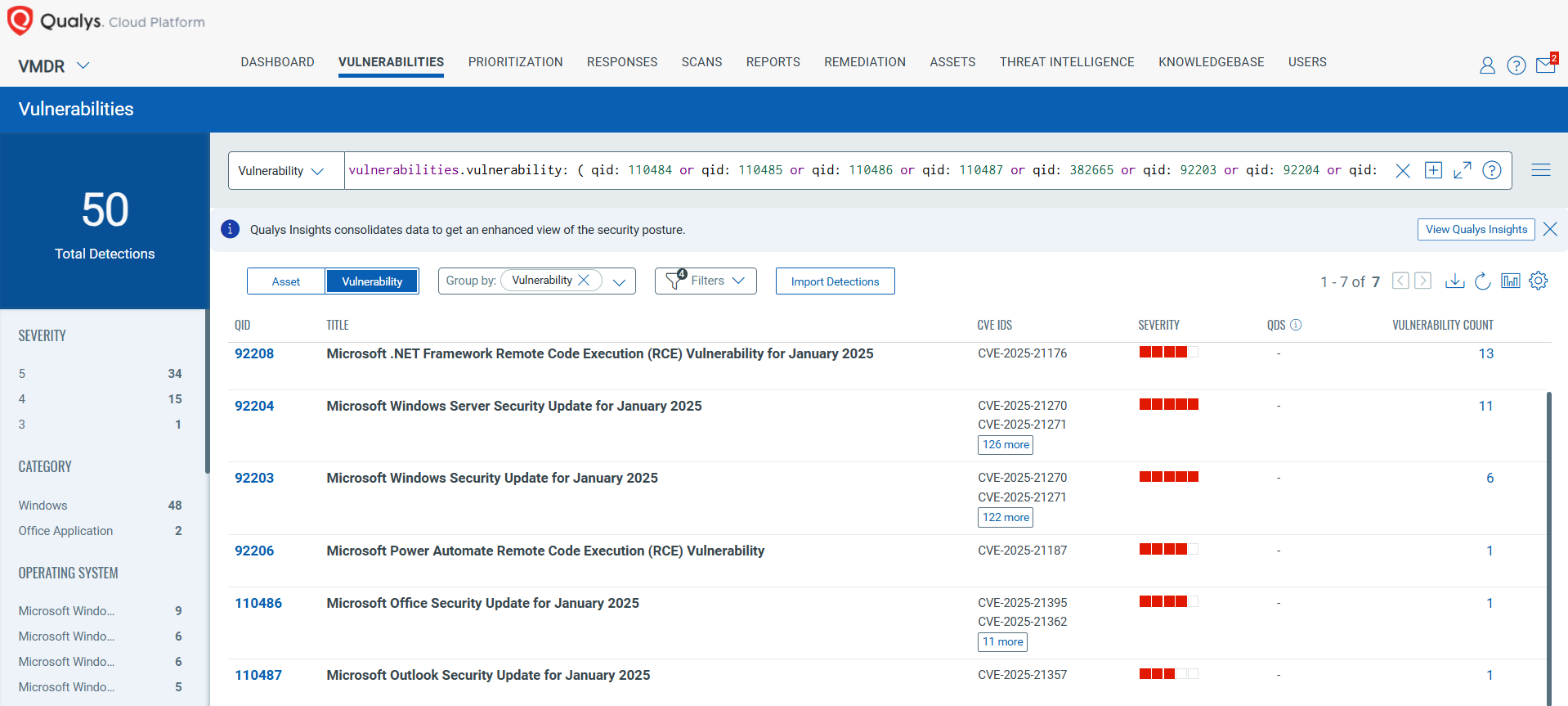
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid: 110484 or qid: 110485 or qid: 110486 or qid: 110487 or qid: 382665 or qid: 92203 or qid: 92204 or qid: 92205 or qid: 92206 or qid: 92207 or qid: 92208 or qid: 92209 or qid: 92210 or qid: 92211 )
Rapid Response with Patch Management (PM)
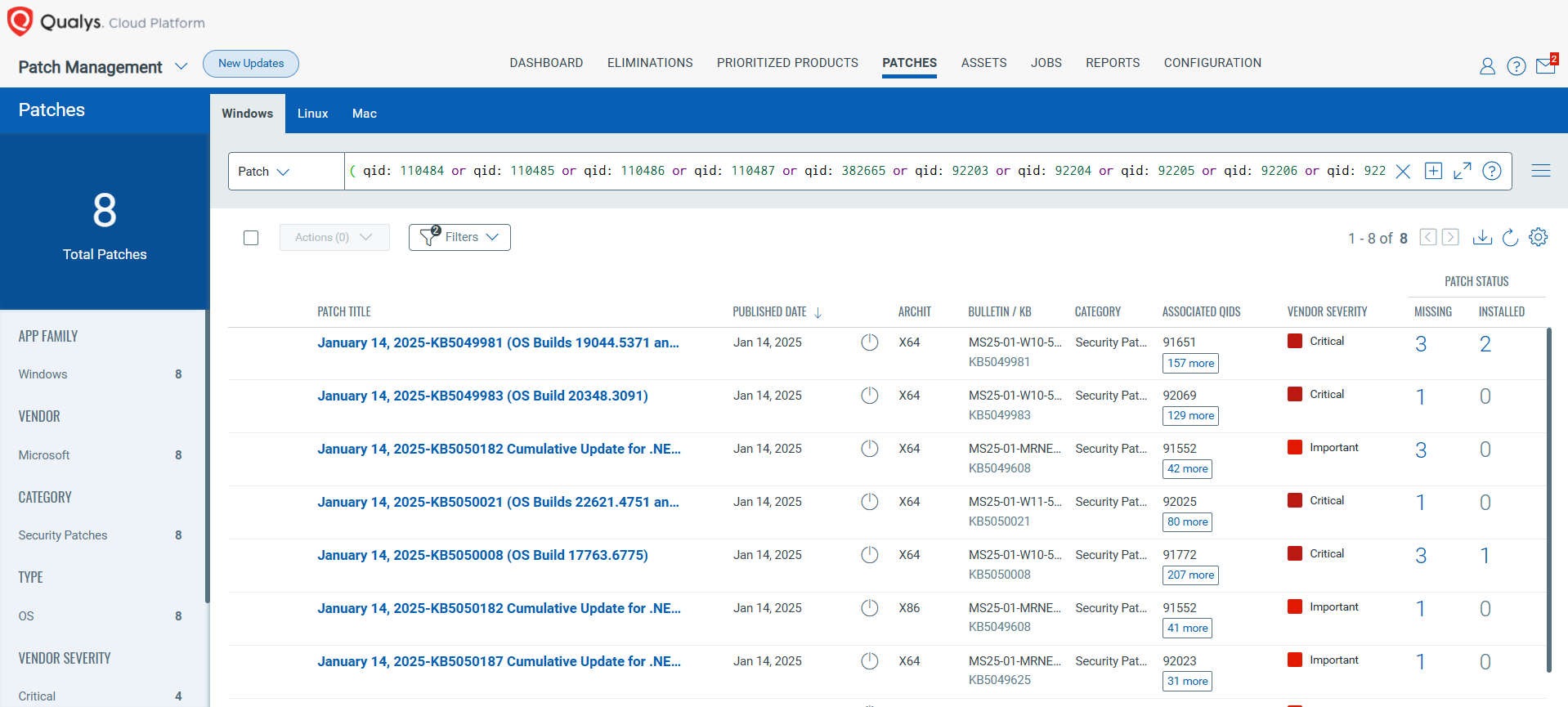
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid: 110484 or qid: 110485 or qid: 110486 or qid: 110487 or qid: 382665 or qid: 92203 or qid: 92204 or qid: 92205 or qid: 92206 or qid: 92207 or qid: 92208 or qid: 92209 or qid: 92210 or qid: 92211 )
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
With Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/Patch) cannot be done now. These security controls are not recommended by industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best-practice existing in a default state that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
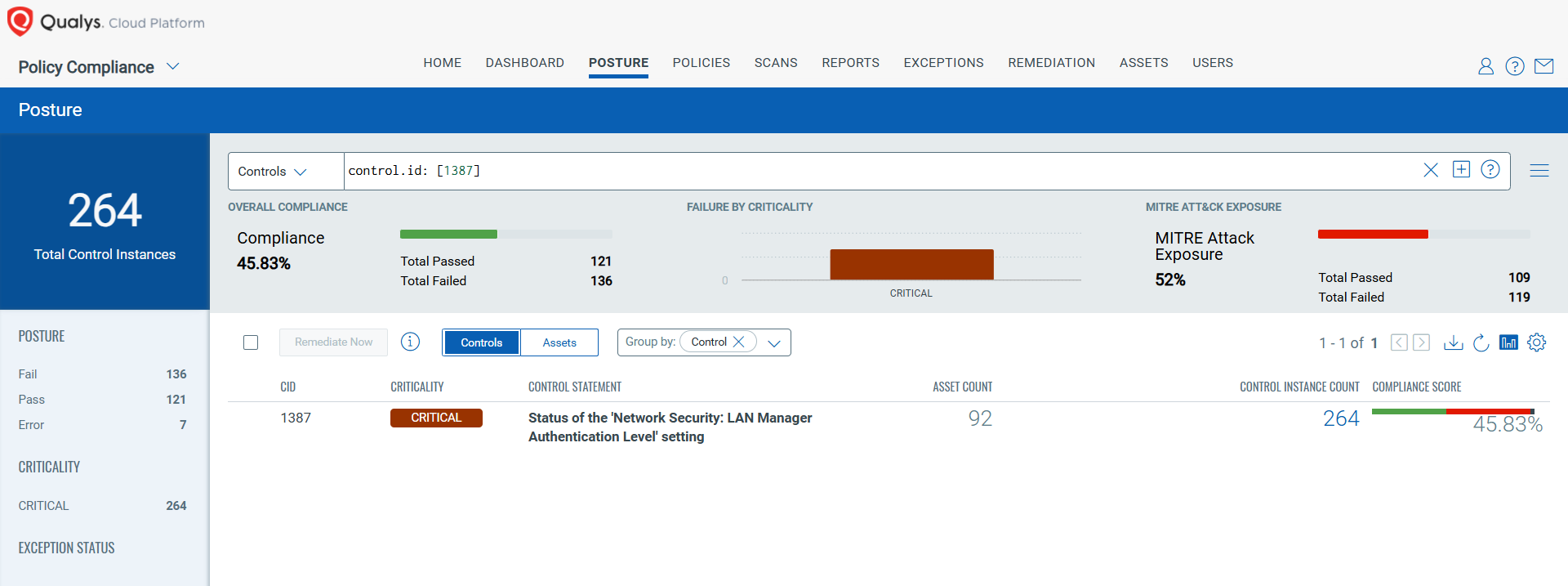
CVE-2025-21311: Windows NTLM V1 Elevation of Privilege Vulnerability
This vulnerability has a CVSS: 3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 1387 Status of the ‘Network Security: LAN Manager Authentication Level’ setting
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [1387]
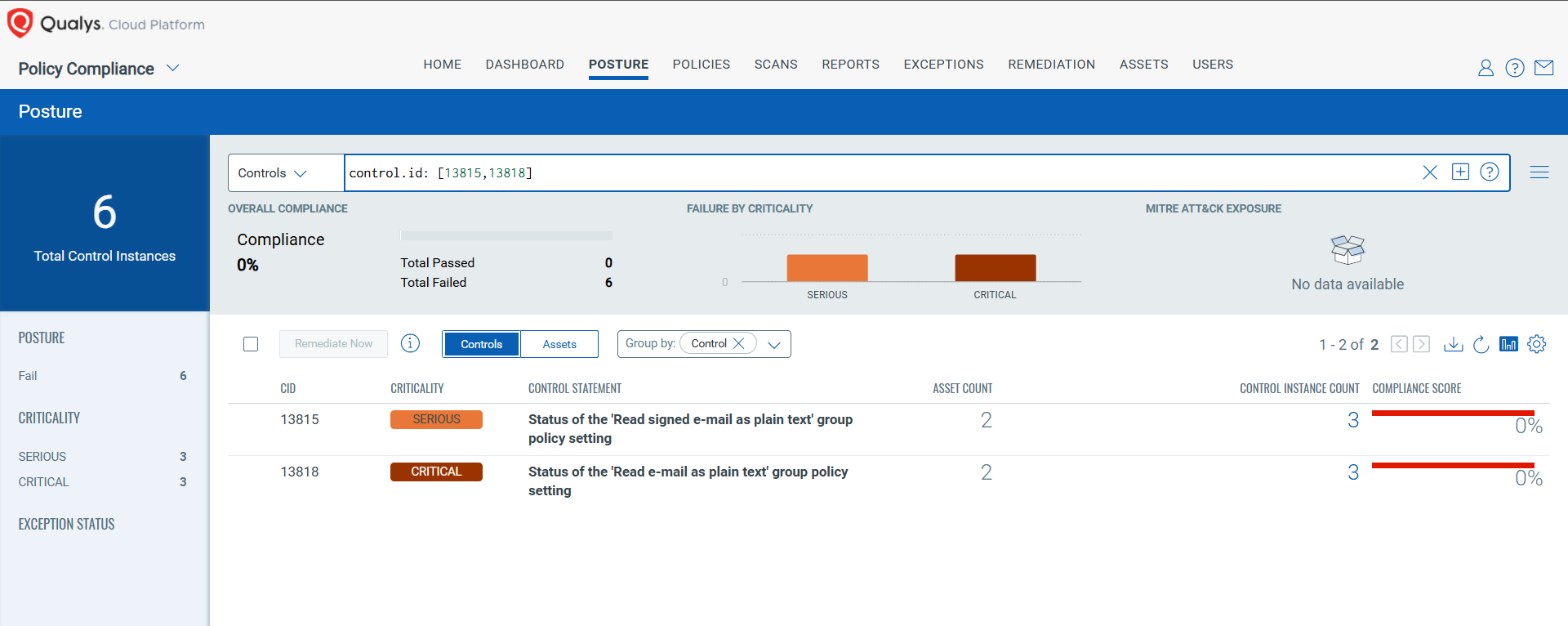
CVE-2025-21298: Windows OLE Remote Code Execution Vulnerability
This vulnerability has a CVSS: 3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 13815 Status of the ‘Read signed e-mail as plain text’ group policy setting
- 13818 Status of the ‘Read e-mail as plain text’ group policy setting
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [13815,13818]
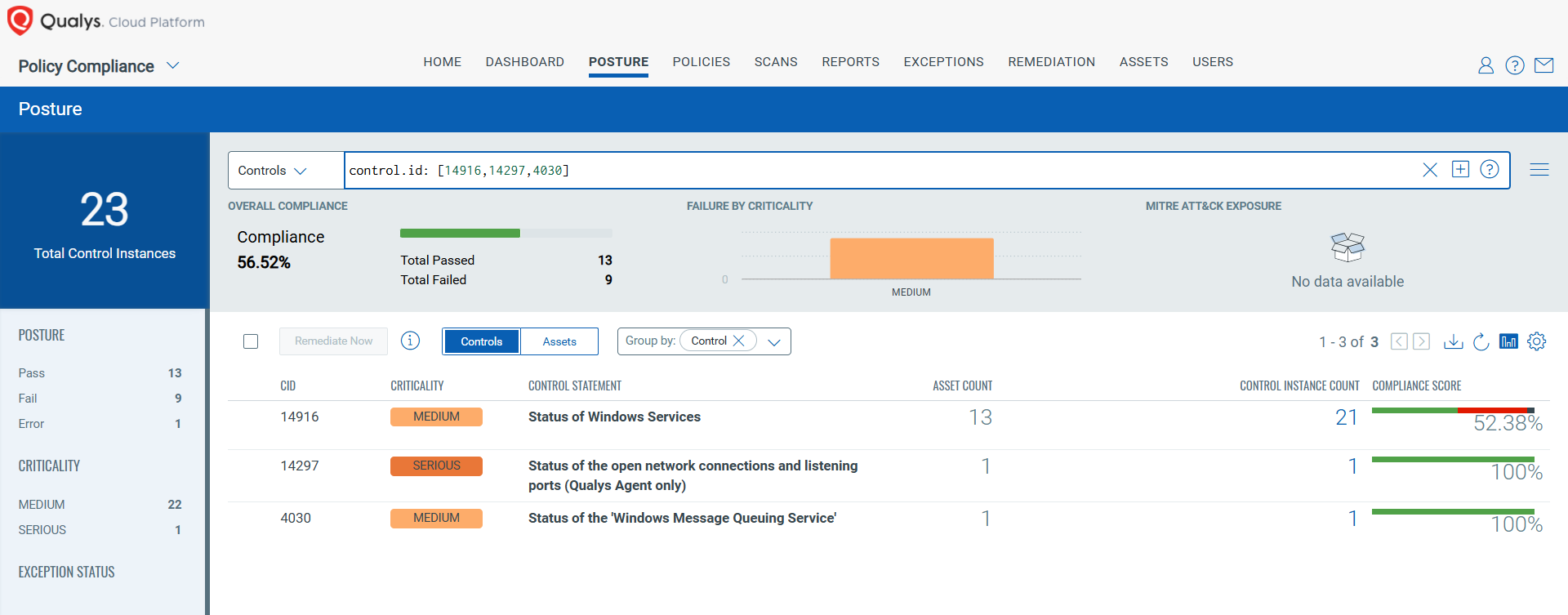
CVE-2025-21307: Windows Reliable Multicast Transport Driver (RMCAST) Remote Code Execution Vulnerability
This vulnerability has a CVSS: 3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 14916 Status of Windows Services
- 14297 Status of the open network connections and listening ports (Qualys Agent only)
- 4030 Status of the ‘Windows Message Queuing Service’
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [14916,14297,4030]
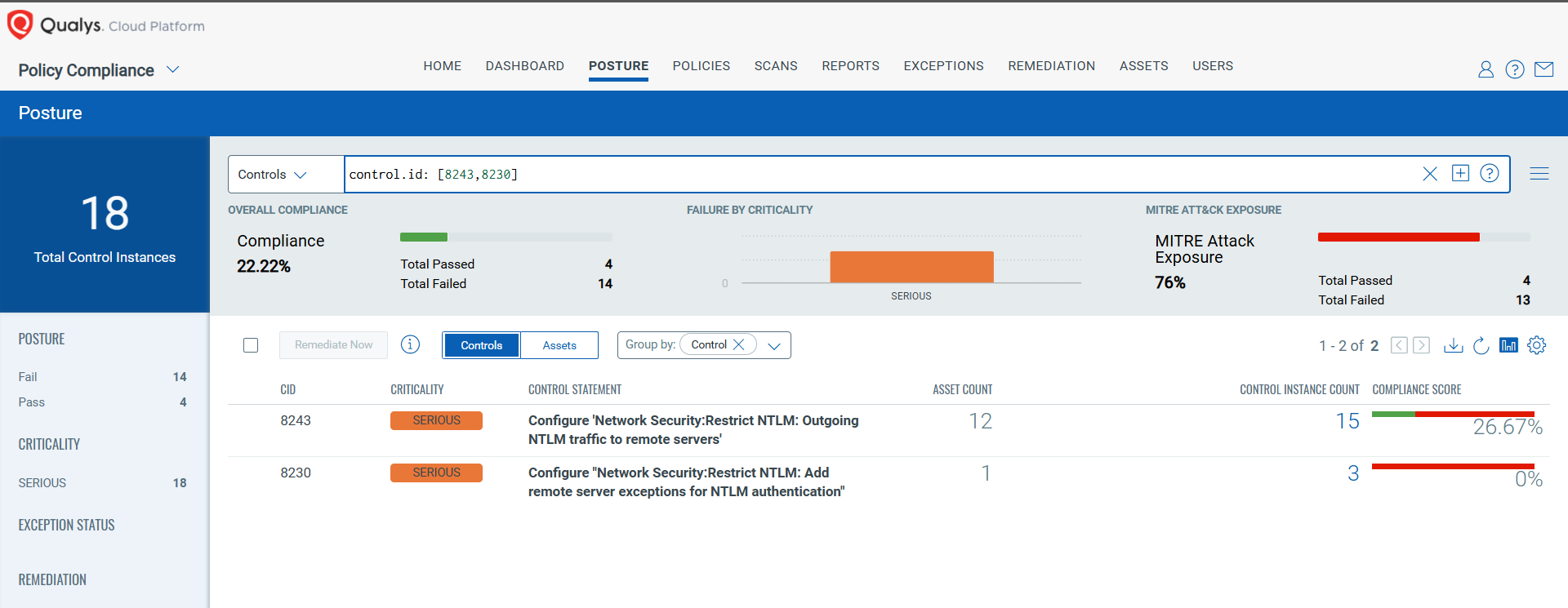
CVE-2025-21308: Windows Themes Spoofing Vulnerability
This vulnerability has a CVSS: 3.1 6.5 / 5.7
Policy Compliance Control IDs (CIDs):
- 8243 Configure ‘Network Security:Restrict NTLM: Outgoing NTLM traffic to remote servers’
- 8230 Configure ‘Network Security:Restrict NTLM: Add remote server exceptions for NTLM authentication’
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [8243,8230]
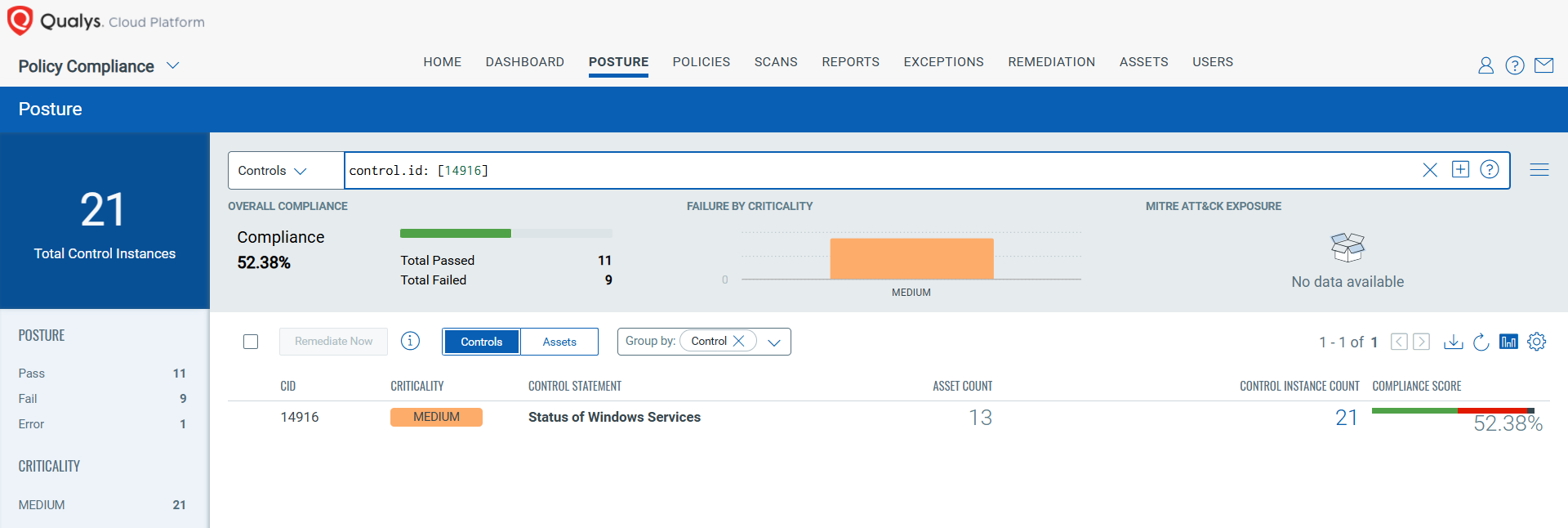
CVE-2025-21224: Windows Line Printer Daemon (LPD) Service Remote Code Execution Vulnerability
This vulnerability has a CVSS: 3.1 8.1 / 7.1
Policy Compliance Control IDs (CIDs):
- 14916 Status of Windows Services
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [14916]
Visit the January 2025 Security Updates page to access the full description of each vulnerability and the systems it affects.
Qualys customers can scan their network with QIDs 110484, 110485, 110486, 110487, 382665, 92203, 92204, 92205, 92206, 92207, 92208, 92209, 92210, and 92211 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide
https://msrc.microsoft.com/update-guide/releaseNote/2025-Jan
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-21333
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-21334
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-21335
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21366
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21395
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21186
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21275
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21308
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21294
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21295
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21296
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21297
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21309
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21298
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21307
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21311
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21354
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2025-21362