Security researchers at Bishop Fox released a PoC for a vulnerability impacting SonicWall SonicOS. Tracked as CVE-2024-53704, the vulnerability has a critical severity rating with a CVSS score of 9.8. Successful exploitation of the vulnerability may allow a remote attacker to bypass authentication and retrieve the session cookie for a logged-in user, leading to session hijacking.
CISA added the CVE-2024-53704 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before March 11, 2025.
A quick search revealed more than 11,000 targets on Shodan at the time of writing.
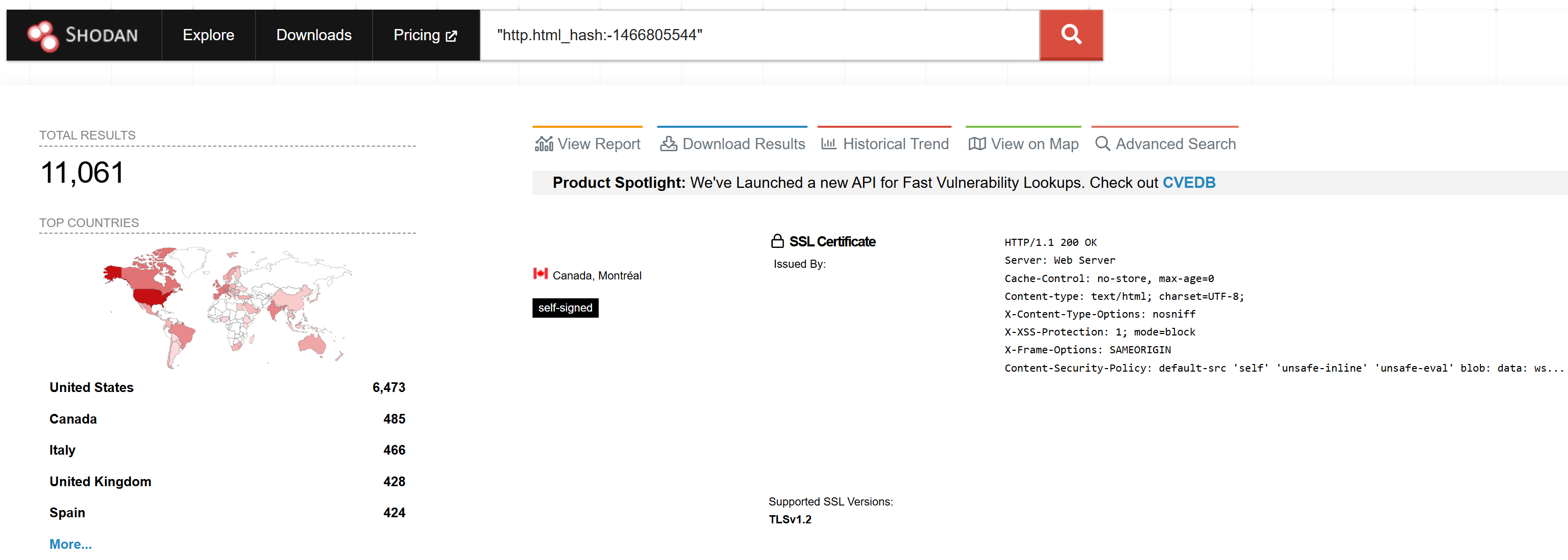
SonicOS runs on SonicWall network security appliances (firewalls) and provides a web management interface for configuring features, policies, security services, and more.
Vulnerability Timeline
SonicaWall first released an initial advisory on January 7, 2025, to address multiple vulnerabilities, including CVE-2024-53704. On January 31, 2025, SonicWall confirmed the publicly available PoC of the CVE-2024-53704.
Vulnerability Details
The authentication bypass vulnerability in processing Base64-encoded session cookies originates from an incorrect implementation of an authentication algorithm. No authentication is required to exploit the vulnerability.
An attacker with control of an active SSL VPN session can read the user’s Virtual Office bookmarks, obtain a client configuration profile for NetExtender, open a VPN tunnel, access private networks available to the hijacked account, and log out the session (terminating the user’s connection as well).
Qualys Threat Research Unit reproduced the vulnerability in our labs.
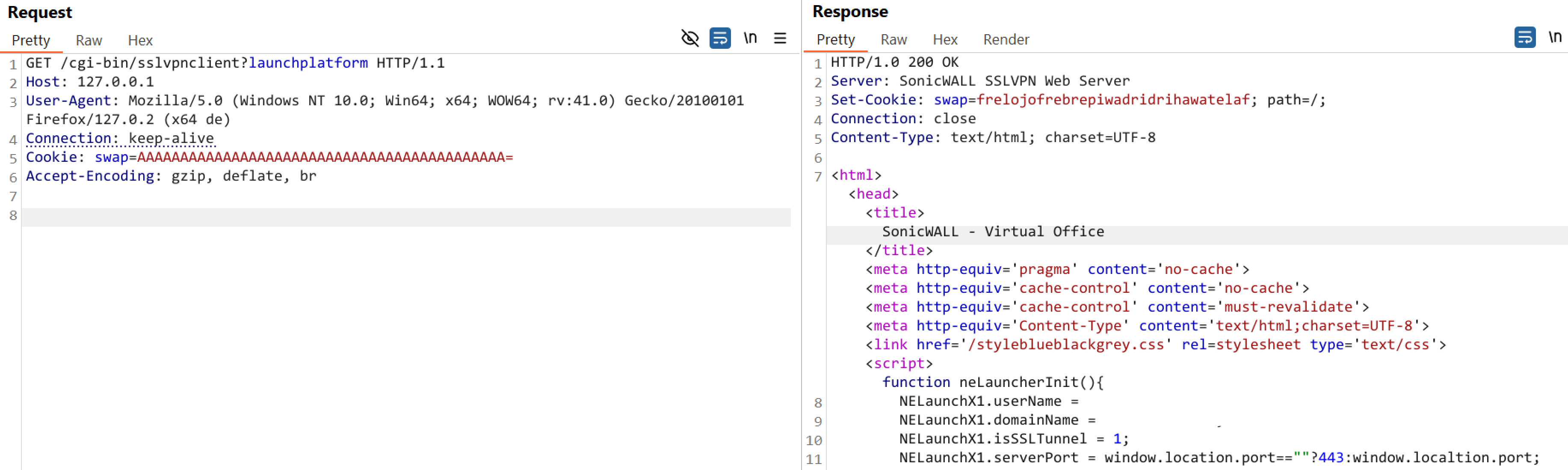
Image Source: Qualys Threat Research Unit
Affected Versions
- SonicWall SonicOS 7.1.x (7.1.1-7058 and older versions)
- SonicWall SonicOS and version 7.1.2-7019
- SonicWall SonicOS version 8.0.0-8035
Mitigation
- SonicOS version 7.0.1-5165 and later
- SonicOS version 7.1.3-7015 and later
- SonicOS version 8.0.0-8037 and higher
For more information, please refer to the SonicWall Security Advisory (SNWLID-2025-0003).
Workaround
SonicWall suggests limiting trusted sources or disabling SSLVPN access to the Internet.
SonicWall also recommends restricting firewall management to trusted sources or disabling firewall SSH management from Internet access.
Qualys Detection
Qualys customers can scan their devices with QIDs 732163 and 732253 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2025-0003
https://bishopfox.com/blog/sonicwall-cve-2024-53704-ssl-vpn-session-hijacking
When attempting to make a request to https://:4433/cgi-bin/sslvpnclient?launchplatform, I receive an empty response. How should I proceed to determine if the firewall is not vulnerable, and what steps should I take to test it?
If I receive an empty response when connecting to /cgi-bin/sslvpnclient?launchplatform, does this mean the firewall is not vulnerable? Could you provide more guidance on how to test this vulnerability during a penetration test (PT)?