The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warns about the active exploitation of five vulnerabilities impacting software from Cisco, Hitachi Vantara, Microsoft Windows, and Progress WhatsUp Gold. CISA added the vulnerabilities to its Known Exploited Vulnerabilities Catalog, urging users to patch the flaw before March 24, 2025.
CVE-2023-20118: Cisco Small Business Routers Remote Command Execution Vulnerability
The vulnerability originates from improper user input validation within incoming HTTP packets. An attacker could exploit this vulnerability by sending a crafted HTTP request to the web-based management interface. An attacker could gain root-level privileges and access unauthorized data upon successful exploitation. An attacker must have valid administrative credentials on the affected device to exploit this vulnerability.
CVE-2018-8639: Win32k Elevation of Privilege Vulnerability
The elevation of privilege vulnerability in Windows originates from improper object handling in memory by the Win32k component. Upon successful exploitation of the vulnerability, an attacker could run arbitrary code in kernel mode.
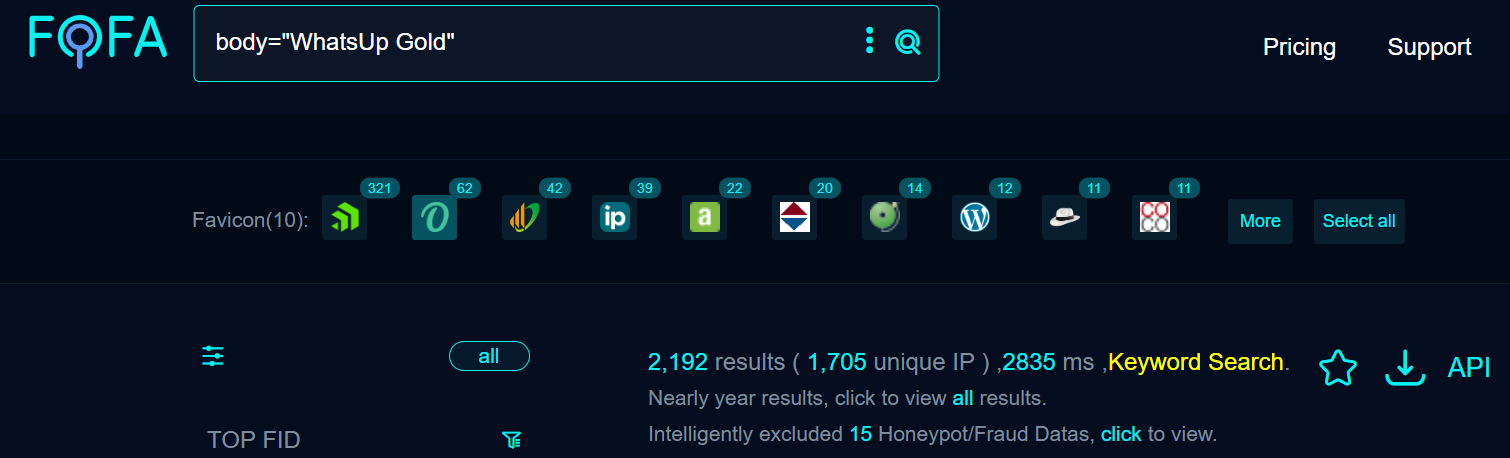
CVE-2024-4885: WhatsUp Gold Remote Code Execution Vulnerability
The unauthenticated Remote Code Execution vulnerability in the WhatsUp.ExportUtilities.Export.GetFileWithoutZip may allow an attacker to execute commands with iisapppool\\nmconsole privileges.
A quick search revealed more than 2100 targets on Fofa at the time of writing.
CVE-2022-43939: Pentaho BA Server Authorization Bypass Vulnerability
The authorization bypass vulnerability in the Hitachi Vantara Pentaho BA Server originates from the use of non-canonical URL paths for authorization decisions.
CVE-2022-43769: Pentaho BA Server Special Element Injection Vulnerability
The special element injection vulnerability in the Hitachi Vantara Pentaho BA Server may allow an attacker to inject Spring templates into properties files, leading to arbitrary command execution.
PoC for CVE-2022-43939 and CVE-2022-43769
The Qualys Threat Research Unit (TRU) verified the vulnerabilities in the Hitachi Pentaho Business Analytics Server by sending an HTTP GET request to the /pentaho/api/ldap/config/ldapTreeNodeChildren/require.js endpoint. The request triggered a reverse connection to an attacker’s address, validating the security flaw.

Image Source: Qualys Threat Research Unit (TRU)
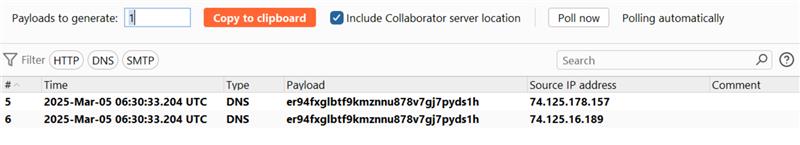
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
CVE-2023-2011
- RV016 Multi-WAN VPN Routers
- RV042 Dual WAN VPN Routers
- RV042G Dual Gigabit WAN VPN Routers
- RV082 Dual WAN VPN Routers
- RV320 Dual Gigabit WAN VPN Routers
- RV325 Dual Gigabit WAN VPN Routers
CVE-2024-4885
The vulnerability impacts WhatsUp Gold versions before 2023.1.3.
CVE-2022-43939
The vulnerability affects Hitachi Vantara Pentaho Business Analytics Server versions before 9.4.0.1 and 9.3.0.2.
CVE-2022-43769
The vulnerability affects the Pentaho BA Server before 9.4.0.1 and 9.3.0.2, including 8.3.x.
Mitigation
CVE-2023-2011
Cisco Small Business RV016, RV042, RV042G, RV082, RV320 and RV325 Routers have entered the end-of-life process.
CVE-2024-4885
Customers must upgrade to WhatsUp Gold version 2023.1.3 to patch the vulnerability.
CVE-2022-43939 and CVE-2022-43769
Customers must upgrade to 9.4 with Service Pack 9.4.0.1. For version 9.3, Hitachi recommends updating to Service Pack 9.3.0.2 to patch the vulnerabilities.
Qualys Detection
Qualys customers can scan their devices with QIDs 730764, 380292, 91488, and 732303 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2018-8639
https://community.progress.com/s/article/WhatsUp-Gold-Security-Bulletin-June-2024
https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sbr042-multi-vuln-ej76Pke5
https://support.pentaho.com/hc/en-us/articles/14455394120333–Resolved-Pentaho-BA-Server-Use-of-Non-Canonical-URL-Paths-for-Authorization-Decisions-Versions-before-9-4-0-1-and-9-3-0-2-including-8-3-x-Impacted-CVE-2022-43939
https://support.pentaho.com/hc/en-us/articles/14455561548301–Resolved-Pentaho-BA-Server-Failure-to-Sanitize-Special-Elements-into-a-Different-Plane-Special-Element-Injection-Versions-before-9-4-0-1-and-9-3-0-2-including-8-3-x-Impacted-CVE-2022-43769