https://vimeo.com/164494876
Exploit kit authors often update the capabilities of their exploit kits by adding support for new vulnerabilities so that they can compromise and install malware or ransomware on even more machines. As part of the ThreatPROTECT research team, I analyze exploit kits to keep track of the latest vulnerabilities being incorporated into them. Back in February, I analyzed the Silverlight remote vulnerability (CVE-2016-0034), and as expected, it is currently incorporated in many exploit kits. We added the ‘ActiveAttack’ and ‘ExploitKit’ bit in ThreatPROTECT.
In this blog I give a detailed analysis on how to find exploit payloads from exploit kits and how to correlate or come to the conclusion that a new capability (in our case CVE-2016-0034) has been added to the exploit kit. I will also show how anti-virus support ramps up for the payload over time.
Package Capture and Payload Extraction
In this case, I got the source package capture from Malware-Traffic-Analysis, which is a great place to find malware traffic captures, and loaded the package capture into Wireshark. Here, we can see that RIG Exploit Kit is sending Silverlight payloads to the client as shown in the screen capture below.
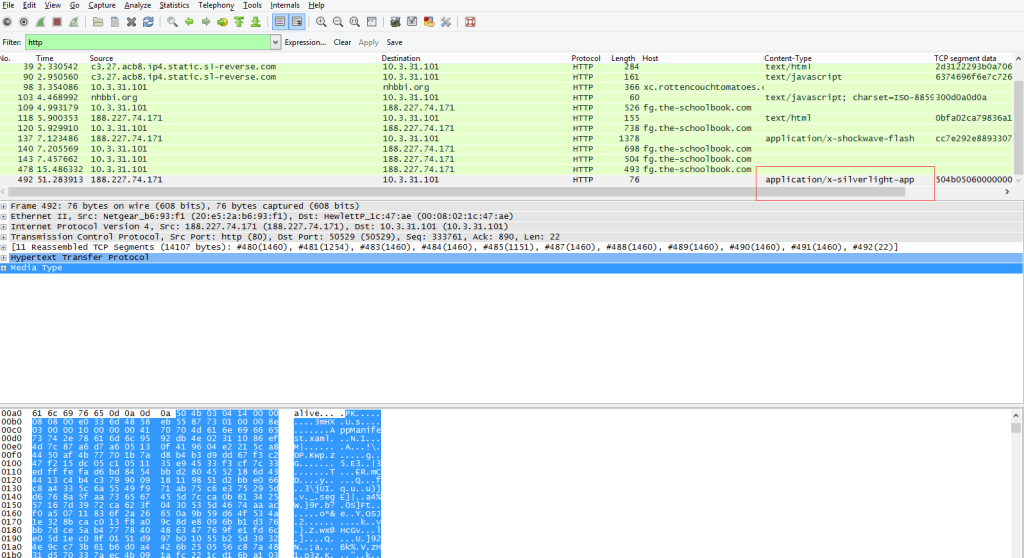
I extract the payload out and save it as XXX.xap. Then load this xap file with a tool called dotpeek as seen the screen capture below.
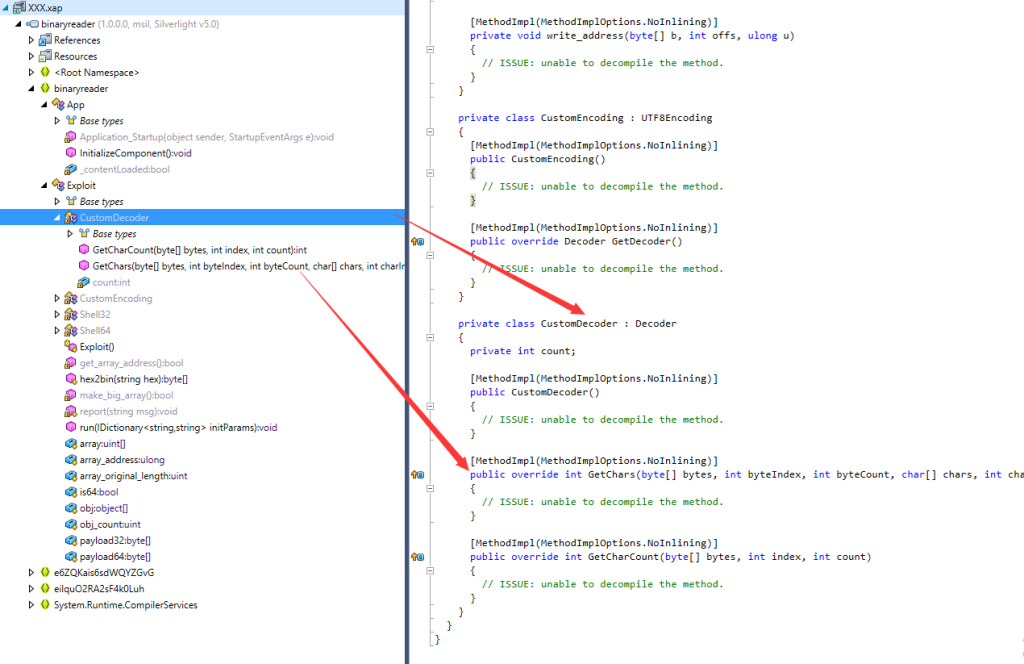
We can see that this payload contains a “custom decoder” and “GetChars” function. For those who don’t know about CVE-2016-0034, this vulnerability is about arbitrary memory writing in a customized decoder in Silverlight. To exploit this CVE requires a customized decoder (screen capture above) and a “GetChars” function which return negative values.
New Zero Day or CVE-2016-0034?
Now its time to decide if Rig is using a new zero day or an existing vulnerability. The reverse engineering tool didn’t give me the decompiled code of “GetChars” in this payload, so I did it manually.
Load the XXX.xap into IDA, and it jumps to “GetChars” function. The function first increased the value of instance variable “count” by one. So the execution flow will be different next time this function is called. Jump to loc_1120 the count is 0 (initially the value is 0).
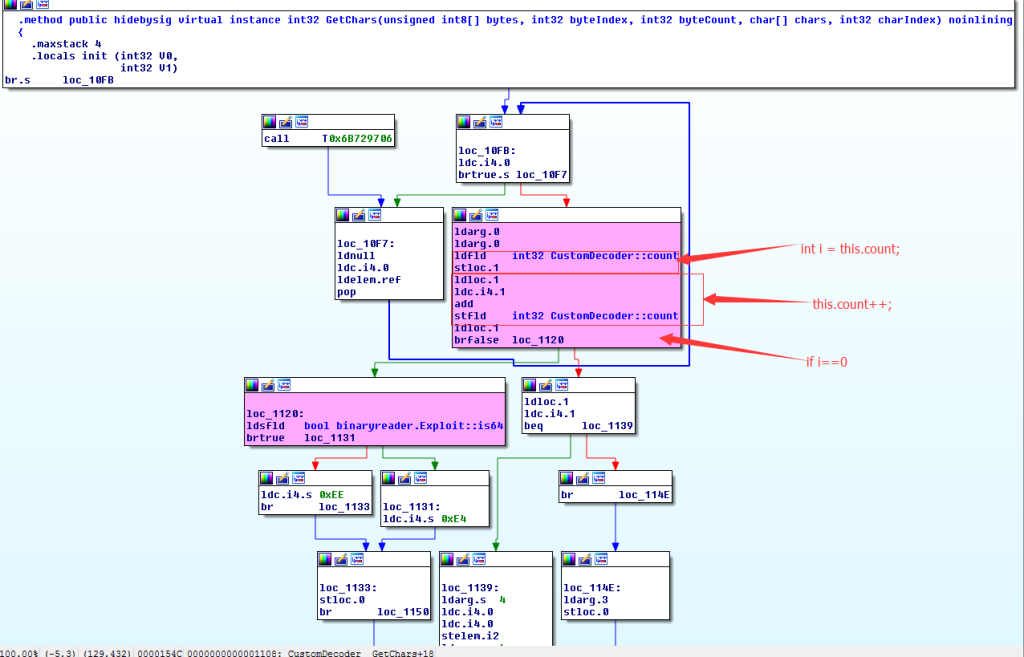
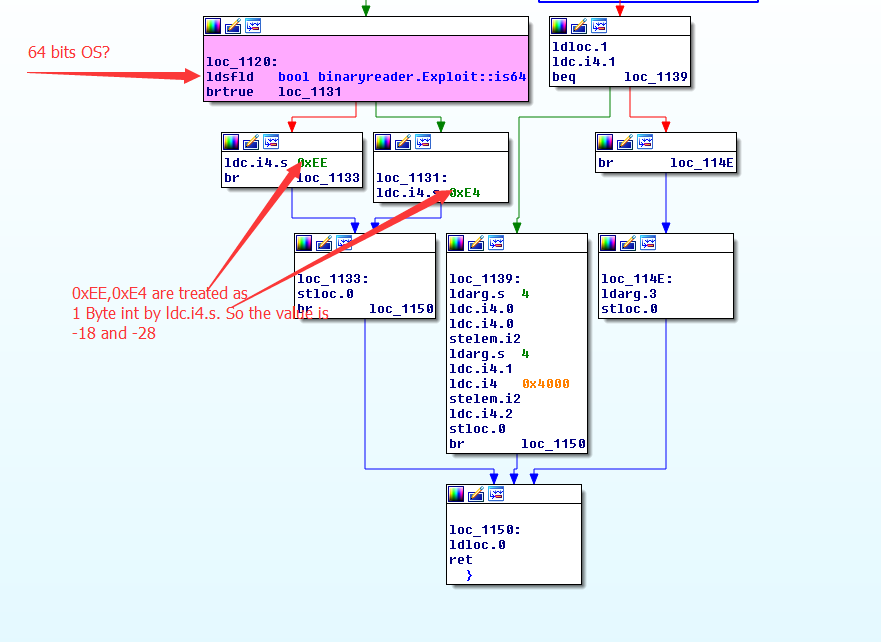
The loc_1120 checks on a 64 bit machines returns -28 and on a 32 bit system returns -18 respectively. So now the “GetChars” returns negative values in a customized decoder. Which confirms that RIG Exploit Kit is actively exploiting CVE-2016-0034.
Antivirus Detection for the payload
When I loaded the payload in virus total, on 3/31/2016, only two antivirus vendors out of 56 were able to detect this malware payload.
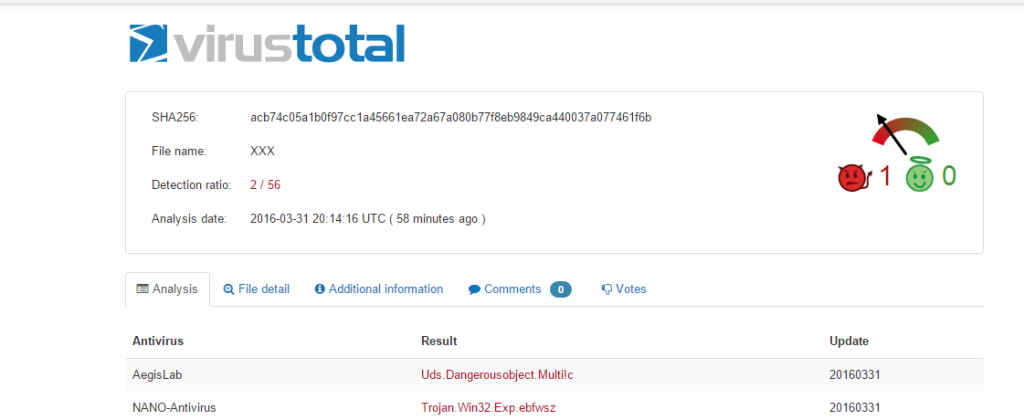
But the next day, the number increased to 9.
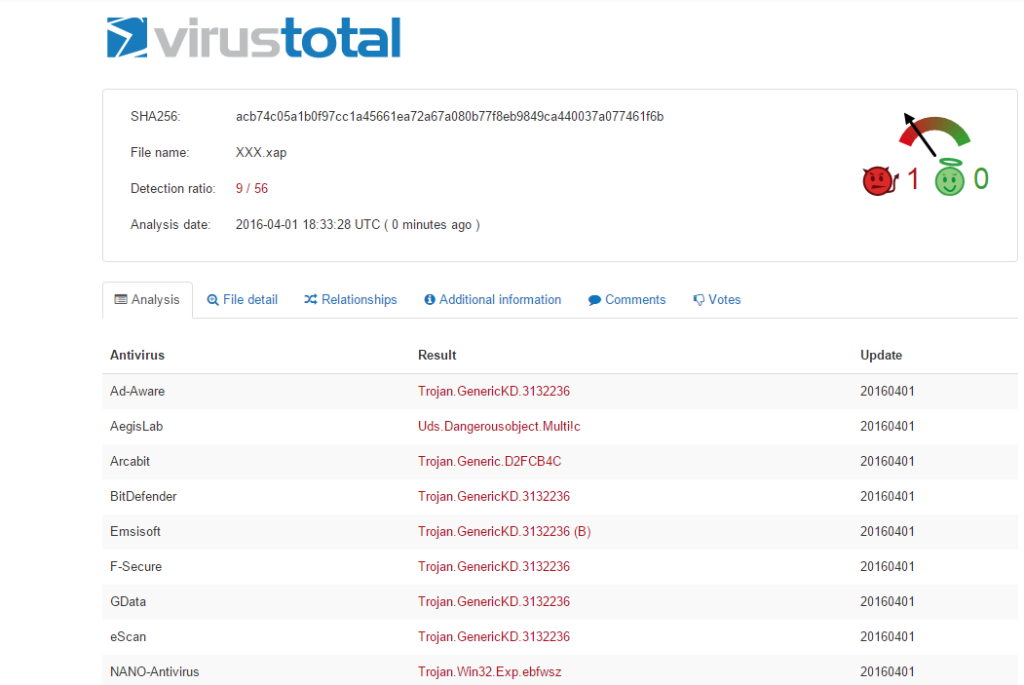
As of today:
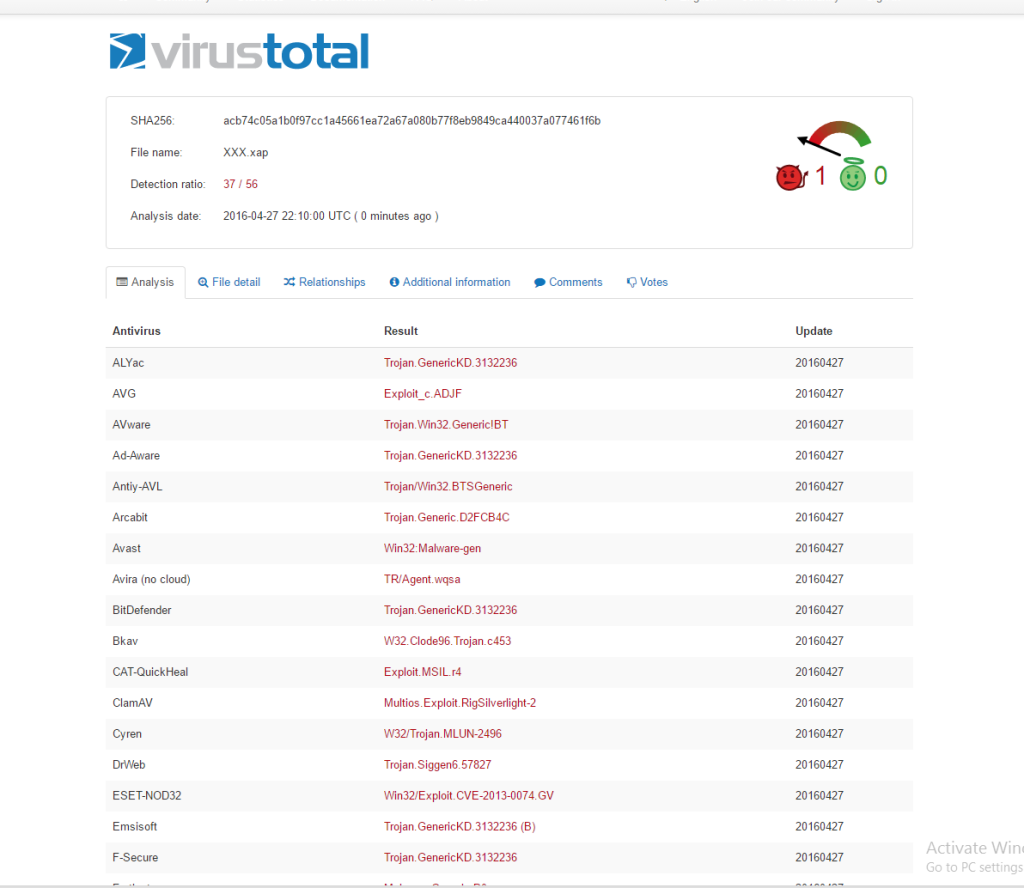
Conclusion
As new exploits get incorporated into exploit kits it is very crucial to know in a timely fashion which vulnerabilities are weaponized so that organizations can focus their remediation efforts. Its also crucial to know that it takes some time for anti-virus products to react, and therefore proactive knowledge of these threats can be an effective tool in your arsenal.