Microsoft Office is an office suite of applications, servers, and services developed by Microsoft for Windows and Mac OS platforms. The suite most notably consists of applications such as Microsoft Word, Microsoft Excel, Microsoft PowerPoint, Microsoft Access, Microsoft Publisher, Microsoft Project, Microsoft Visio, Microsoft Outlook among others. In addition to features such as word processing, database management, desktop publishing, spell checking, and OLE data integration, this suite also supports the Visual Basic for Applications scripting language.
Visual Basic for Applications is an implementation of Microsoft’s event-driven programming language Visual Basic 6. It enables building user-defined functions (UDFs), task automation and access to the Windows API and other low-level functionality through dynamic-link libraries (DLLs). With VBA, you can also control other applications using the inter-process communication – OLE Automation. Utilizing this event-driven programming language, you can create a series of commands and instructions to accomplish a task automatically via macro’s.
Though this functionality was meant for legitimate purposes, malware’s have been leveraging this feature illegitimately to carry out malicious tasks for a long time. The most famous example being the Melissa virus from 1999. However, there are settings that you can use to prevent such attacks from repeating themselves again. For example, you can use the VBA Macro notification settings to control how Microsoft Office applications behave when they encounter a macro.
In the latest version of Microsoft Word 2016, you can access these settings by visiting Word Options > Trust Center > Trust Center Settings > Macro Settings. Here, you will be presented with a dialogue similar to:
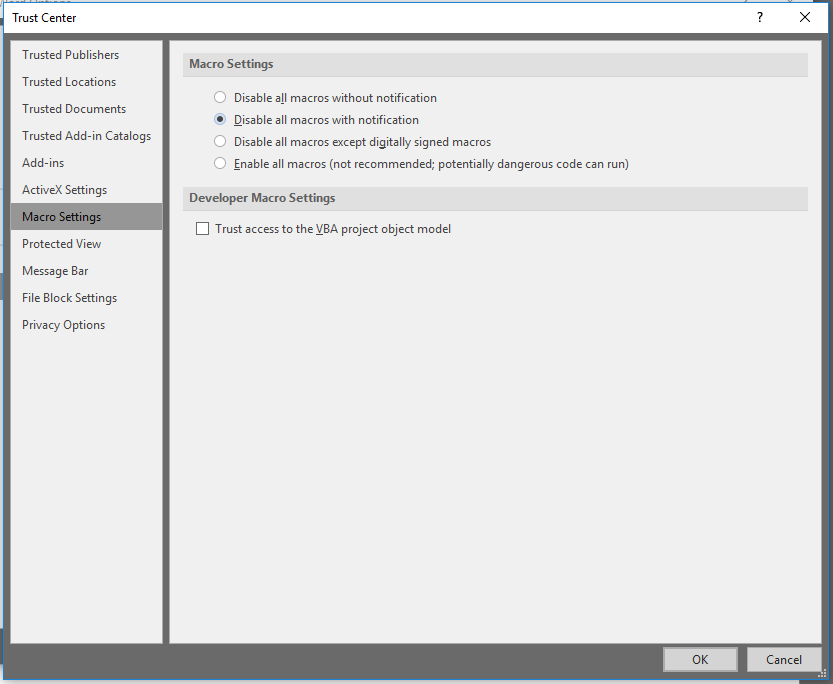
You can configure these settings on your local computer by accessing the following registry key:
HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Word\Security Value Name: VBAWarnings Value Type: REG_DWORD
The possible values are:
- Value 2 – Disable all with notification: The application displays the Trust Bar for all macros, whether signed or unsigned. This option enforces the default configuration in Office.
- Value 3 – Disable all except digitally signed macros: The application displays the Trust Bar for digitally signed macros, allowing users to enable them or leave them disabled. Any unsigned macros are disabled, and users are not notified.
- Value 4 – Disable all without notification: The application disables all macros, whether signed or unsigned, and does not notify users.
- Value 1 – Enable all macros (not recommended): All macros are enabled, whether signed or unsigned. This option can significantly reduce security by allowing dangerous code to run undetected.
If configured via group policy, these settings are stored under the following registry hive:
HKEY_CURRENT_USER\Software\Policies\Microsoft\Office\16.0\Word\Security
Furthermore, as we all know, if these settings are also found under the HKEY_LOCAL_MACHINE hive, they take precedence over HKEY_CURRENT_USER.
It is imperative that customers have either 2,3,4 as the values as this will effectively disable execution of Macro’s. It has been observed that this setting enables the spread of malwares and ransomwares in a network. To prevent this from happening the following QIDs will warn customers if the value is set to 1 in either HKEY_LOCAL_MACHINE or HKEY_CURRENT_USER:
| QID | Title Name |
| 45282 | Untrusted Microsoft Visio Macro Execution Enabled |
| 45281 | Untrusted Microsoft Project Macro Execution Enabled |
| 45280 | Untrusted Microsoft Publisher Macro Execution Enabled |
| 370418 | Untrusted Microsoft Access Macro Execution Enabled |
| 370417 | Untrusted Microsoft PowerPoint Macro Execution Enabled |
| 370416 | Untrusted Microsoft Excel Macro Execution Enabled |
| 370415 | Untrusted Microsoft Word Macro Execution Enabled |
References:
- https://support.office.com/en-us/article/Enable-or-disable-macros-in-Office-documents-7b4fdd2e-174f-47e2-9611-9efe4f860b12
- https://support.office.com/en-us/article/Enable-or-disable-macros-in-Office-files-12b036fd-d140-4e74-b45e-16fed1a7e5c6