Various vulnerabilities have been discovered in dnsmasq, an open source framework for managing DNS, DHCP, Router Advertisement, network boot etc. These issues were discovered in versions prior to 2.78 . The vulnerabilities were disclosed to CERT/CC by Google Security Team. These vulnerabilities can be exploited remotely via DNS and DHCP protocol.
| CVE | Protocol | Description |
| CVE-2017-14491 | DNS | 2 byte heap based overflow |
| CVE-2017-14492 | DHCP | Heap based overflow |
| CVE-2017-14493 | DHCP | Stack based overflow |
| CVE-2017-14494 | DHCP | Information leak |
| CVE-2017-14495 | DNS | DoS due to Out-Of-Memory |
| CVE-2017-14496 | DNS | DoS due to Integer underflow |
| CVE-2017-13704 | DNS | DoS due to DNS queries larger that 512 bytes |
Currently CERT/CC is tracking the issue on ticket 973527.
Vulnerability:
The vulnerabilities range from buffer overflows to DoS due to memory exhaustion, integer under-flows and Information leak. As per the dnsmasq changelogs these bugs are addressed in version 2.78. The Google Security Team has released PoC for each of the vulnerabilities disclosed by them except for CVE-2017-13704.
CVE-2017-14491: A crafted domain name request triggers a heap overflow in the DNS component. This overflow can result in a crash or allow the attacker to gain control of the target.
CVE-2017-14492: A crafted RA request in IPv6 can cause a heap overflow and result in a crash or target take over. Attacker must be on the local network to exploit this vulnerability.
CVE-2017-14493: A crafted request in DHCPv6 can cause a stack overflow leading to crash or target take over.
CVE-2017-14494: A custom DHCPv6 packet can cause dnsmasq to respond with information beyond the packet buffer, this leads to information leak. This leaked information can aid in bypassing ASLR.
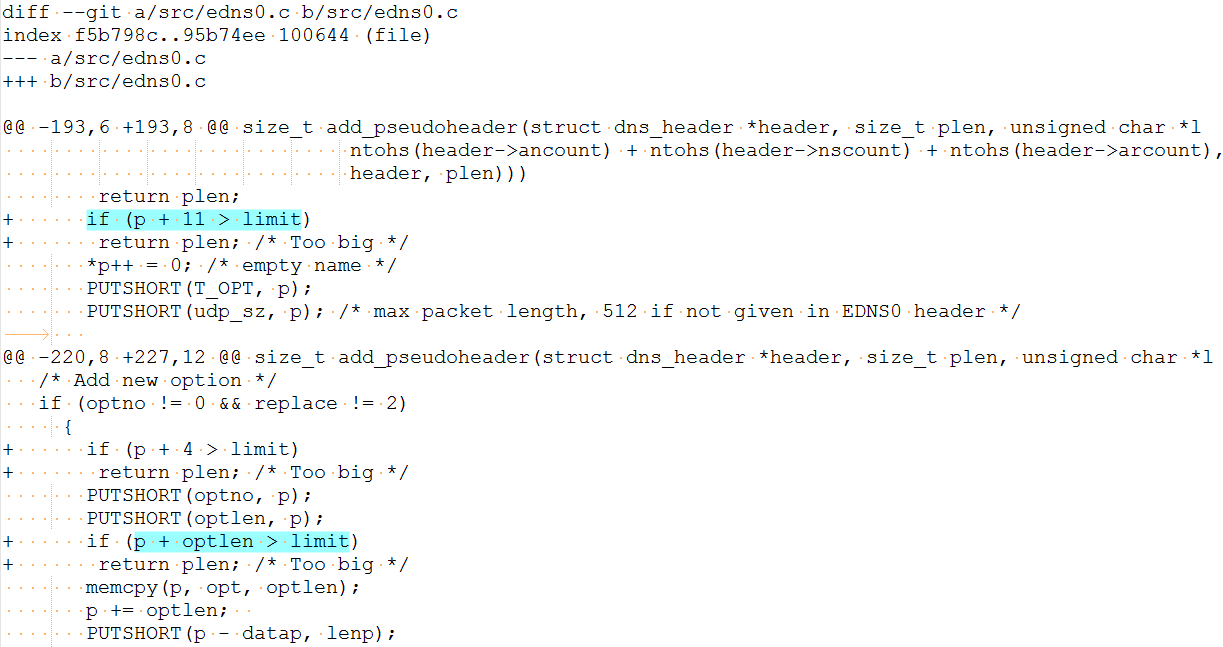
CVE-2017-14495: Crafted DNS queries can trigger memory allocation(s) in the add_pseudoheader function. The function fails to free the allocated memory, this leads to DoS due to out-of-memory condition.
CVE-2017-14496: DoS can occur when function add_pseudoheader tries to allocate memory using memcpy with a negative size as an argument. This can be trigger via malicious DNS queries.
CVE-2017-13704: A UDP DNS query which exceeds 512 bytes can crash the target resulting in DoS.
Fixes:
CVE-2017-14492: A bounds was included in function icmp6_packet() in radv.c to limit the size of presentation domain name to 1025 bytes.
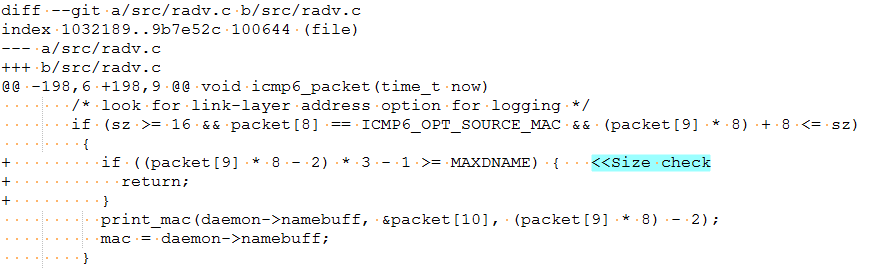
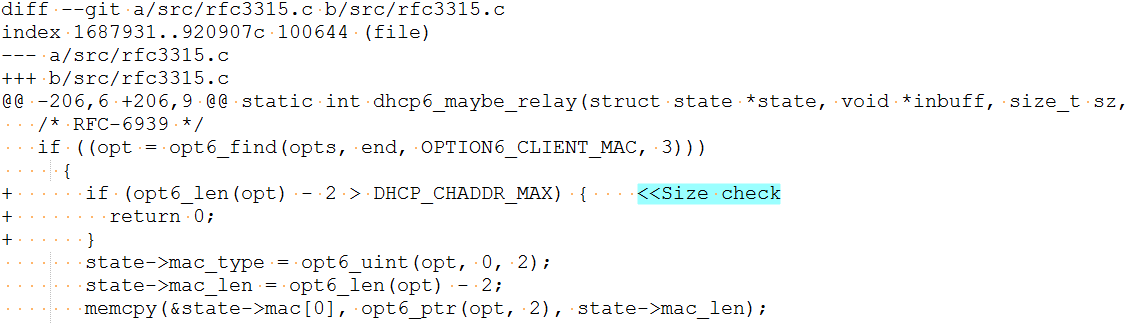
CVE-2017-14493: A check is included in function dhcp6_maybe_relay to make sure the client hardware address (CHADDR) in the received DHCP packet is limited to 16 bytes.
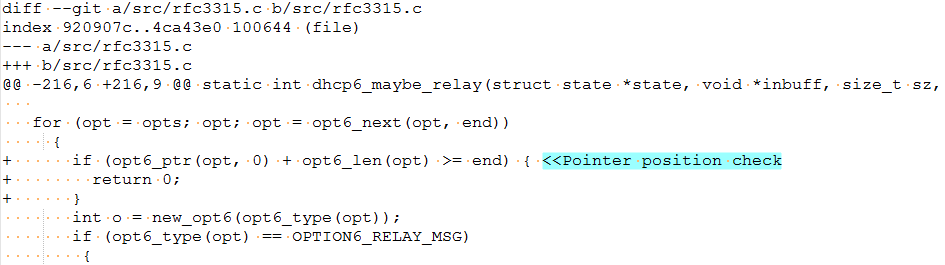
CVE-2017-14494: The variable end points to the actual length of the options field in the packet. The if condition checks if the current position is within the bounds of the options field.
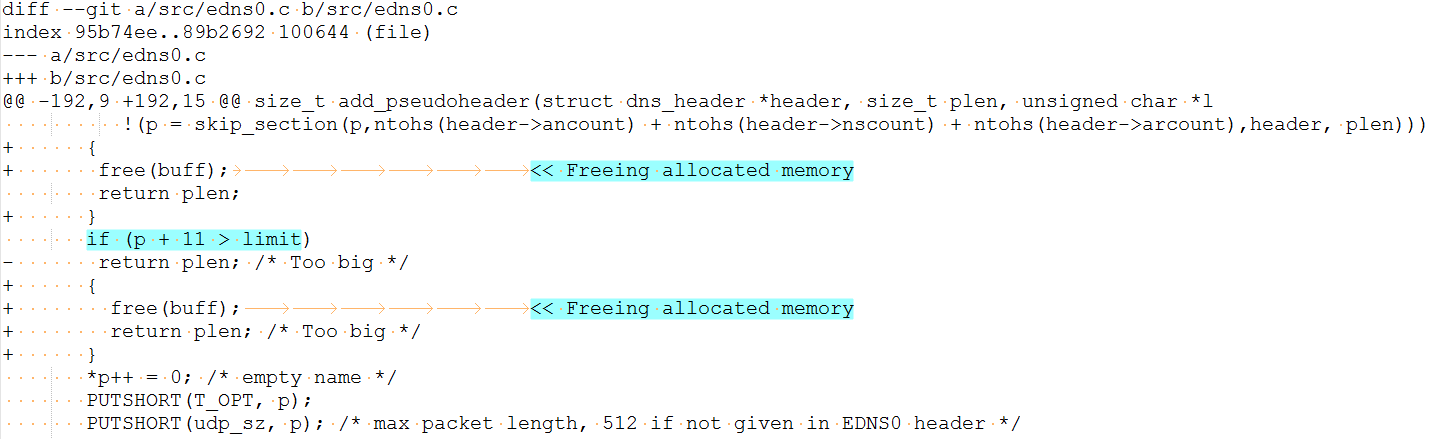
CVE-2017-14495: Freeing allocated memory in function add_pseudoheader().
CVE-2017-14496: Multiple checks are included to make sure that optlen is non negative integer.
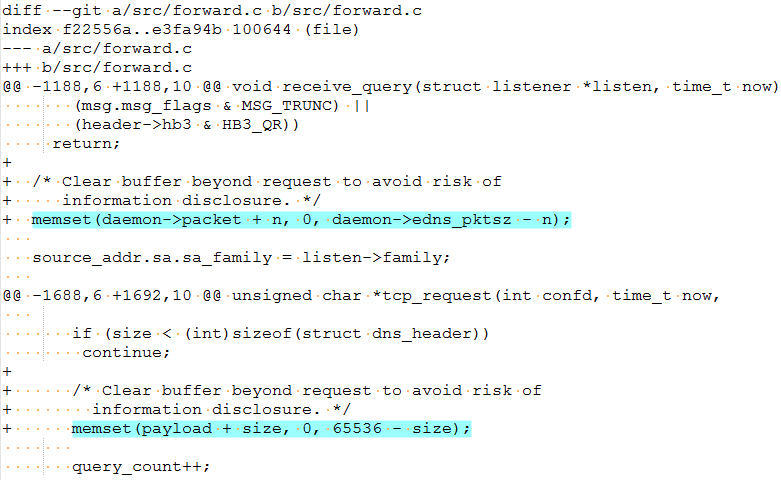
CVE-2017-13704: The address locations after the packet buffer is set to zero to avoid information disclosure.
Mitigation:
We request organizations to scan their networks with the QIDs listed below to detect vulnerable targets.
| CVE(s) | QID | Description |
| CVE-2017-14491 | 390008 | Oracle VM Server for x86 Security Update for dnsmasq (OVMSA-2017-0160) |
| 256313 | CentOS Security Update for dnsmasq (CESA-2017:2838) | |
| 157571 | Oracle Enterprise Linux Security Update for dnsmasq (ELSA-2017-2840) | |
| 236522 | Red Hat Update for dnsmasq (RHSA-2017:2840) | |
| 236521 | Red Hat Update for dnsmasq (RHSA-2017:2839) | |
| 236520 | Red Hat Update for dnsmasq (RHSA-2017:2838) | |
| 157567 | Oracle Enterprise Linux Security Update for dnsmasq (ELSA-2017-2838) | |
| CVE-2017-14491, CVE-2017-14492, CVE-2017-14493, CVE-2017-14494 |
236519 | Red Hat Update for dnsmasq (RHSA-2017:2837) |
| CVE-2017-14491, CVE-2017-14492, CVE-2017-14493, CVE-2017-14494, CVE-2017-14495, CVE-2017-14496 |
170408 | OpenSUSE Security Update for dnsmasq (openSUSE-SU-2017:2633-1) |
| 370602 | OpenBSD DNSMasq Multiple Vulnerabilities | |
| 370600 | FreeBSD DNSMasq Multiple Vulnerabilities | |
| 256314 | CentOS Security Update for dnsmasq (CESA-2017:2836) | |
| 351105 | Amazon Linux Security Advisory for dnsmasq: ALAS-2017-907 | |
| 196922 | Ubuntu Security Notification for Dnsmasq Vulnerabilities (USN-3430-1) | |
| 236518 | Red Hat Update for dnsmasq (RHSA-2017:2836) | |
| 170388 | SUSE Enterprise Linux Security Update for dnsmasq (SUSE-SU-2017:2619-1) | |
| 170387 | SUSE Enterprise Linux Security Update for dnsmasq (SUSE-SU-2017:2618-1) | |
| 176169 | Debian Security Update for dnsmasq (DSA 3989-1) | |
| 157566 | Oracle Enterprise Linux Security Update for dnsmasq (ELSA-2017-2836) | |
| CVE-2017-14491, CVE-2017-14492, CVE-2017-14493, CVE-2017-14494, CVE-2017-14495, CVE-2017-14496, CVE-2017-13704 |
15098 | DNSmasq DNS And DHCP Multiple Remote Vulnerabilities |
References:Please continue to Follow ThreatProtect for information regarding these vulnerabilities.
Behind the Masq: Yet more DNS, and DHCP, vulnerabilities
dnsmasq CHANGELOG
dnsmasq PoC