On November’s Patch Tuesday, Microsoft patched an elevation of privilege vulnerability (CVE-2016-7255) in MS16-135. It was reported that this vulnerability is being actively exploited by Pawn Storm, APT28, Fancy Bear. This blog is about what is this vulnerability and how does Microsoft fix it.
Window, Child Window and CVE-2016-7255
Window plays an important part in Microsoft’s Operating Systems. In Windows kernel, Microsoft implements the window by a “tagWND” structure. As you can see below:
typedef struct tagWND {
THRDESKHEAD head;
struct tagWND *spwndNext;
struct tagWND *spwndParent;
struct tagWND *spwndChild;
struct tagWND *spwndOwner;
…
struct tagMENU *spmenuSys;
struct tagMENU *spmenu;
……
} WND;
Each Window internally has the pointer to its parent Window and child Window and also has menu pointer which points to a tagMENU structure. This structure is behind the hood when users click menus on some Window. When a menu of a windows is selected, Windows kernel will set the flag for the ‘spmenu’ structure with value “MFUNDERLINE” which is 0x4. And When the menu is deselected. Windows will also clear the flag. So
Set MFUNDERLINE:
Or spmenu’s flag, 0x4
Clear MFUNDERLINE:
And spmenu’s flag, not 4(0x FFFFFFFB)
Windows system allows one Window to have a child Windows by providing API calls “SetParent“. One restriction for child Window is that child Window doesn’t have menu bar and “spmenu”.
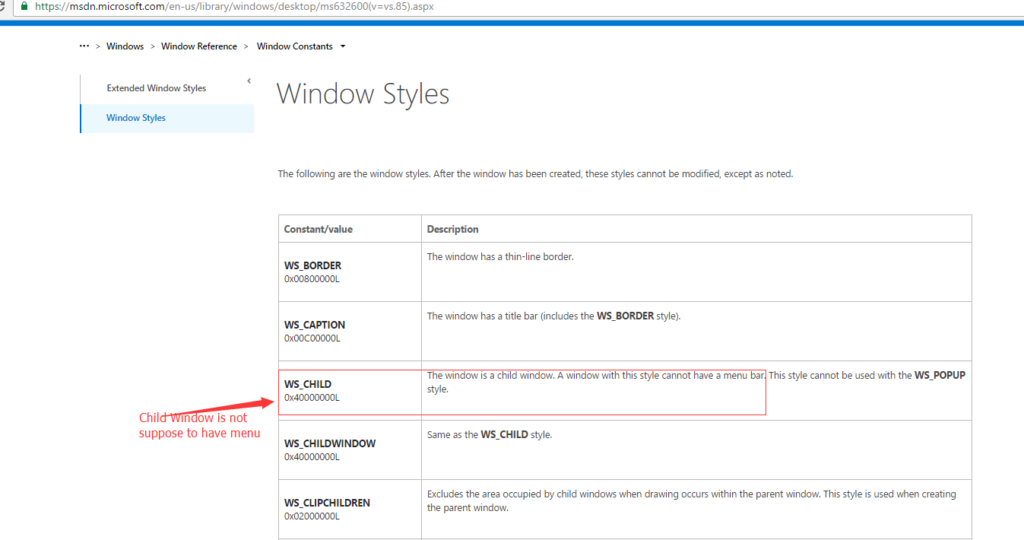
CVE-2016-7255 is in Windows function “xxxNextWindow” in “win32k.sys”. This function doesn’t check if current window is a child window or not, just set or clear the “MFUNDERLINE” flag.
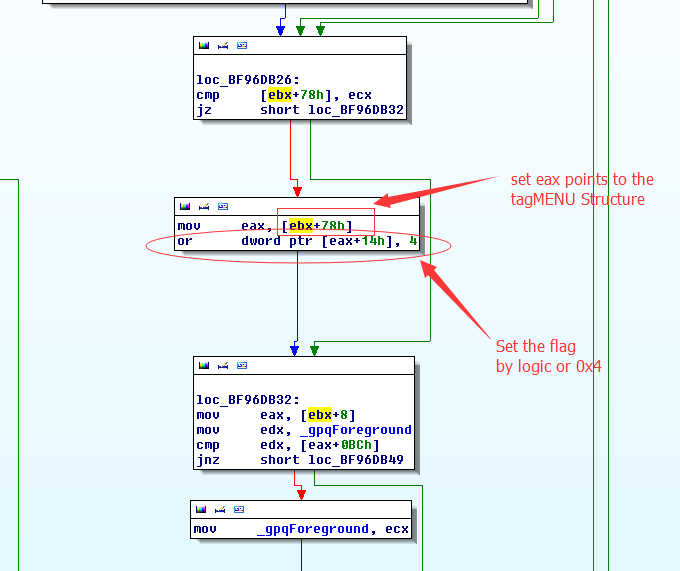
The address of child Window’s spmenu’s flag can be set by attackers via “SetWindowLongPtr“. So this gives the attacker the ability to set or clear any address with 0x1. Attackers can use this to different kernel structures like PEB or TEB to achieve elevation of privilege vulnerability.
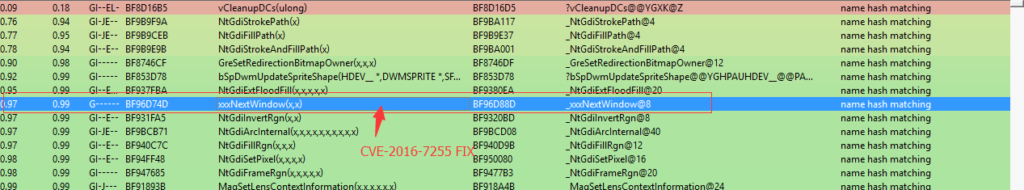
Microsoft Patch BinDIFF
MS16-135 contains multiple fixed in Windows kernel, Fix in “xxxNextWindow “is relatively small.
Microsoft‘s fix is to make sure before Set or clear the “MFUNDERLINE” flag, This window is not a child window.
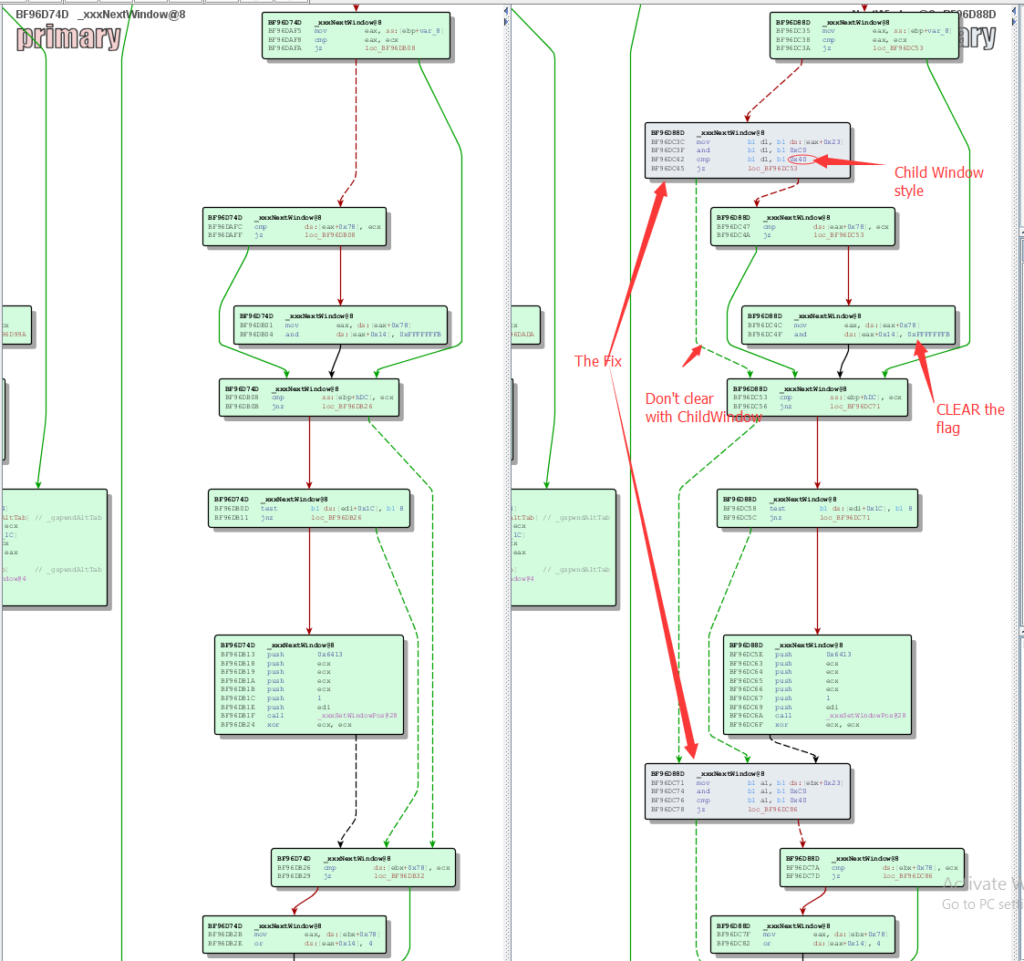
The fix should be like:
If (! CurrentlyWindows is ChildWindow )
These are SET and Clear operations, so this is a 2 lines fix for CVE-2016-7255. Apparently these 2 lines of codes are added and QAed very carefully before MS16-135 was finally released.
Conclusion
CVE-2016-7255 is an elevation of privilege vulnerability. This type of vulnerability is always a chain of a whole attacking process. It is already being used in APT attacks by reported Russian Hackers. Days ago, someone published the POC of the exploiting code. More attacks on this vulnerability are expected. We highly recommend that customers scan their environment for QID: 91294 to identify this uprising risk.
Reference:
https://github.com/tinysec/public/tree/master/CVE-2016-7255
http://read.pudn.com/downloads3/sourcecode/windows/248345/win2k/private/ntos/w32/ntuser/kernel/mndraw.c__.htm
https://technet.microsoft.com/en-us/library/security/ms16-135.aspx