Introduction:
Recently, IoT devices have been used to create large-scale botnet of devices that can execute crippling distributed denial-of-service (DDoS) attacks. Because many IoT devices are unsecured or weakly secured, which allows the bot to access hundreds of thousands of devices. The IoT devices affected in the latest incidents were primarily home routers, network-enabled cameras, and digital video recorders.
So we decided to analyse the firmware of Netgear DGN2200, DGND3700 & WNDR4500 routers. At the time of writing this blog, Shodan search reveals 3000+ active devices that are accessible over the internet, which are running vulnerable versions of firmware.
All tests were performed on the following models:
Netgear DGN2200 running firmware version DGN2200-V1.0.0.50_7.0.50
Netgear DGND3700 running firmware version DGND3700-V1.0.0.17_1.0.17
Netgear WNDR4500 running firmware version V1.0.1.40_1.0.68
Initial Analysis:
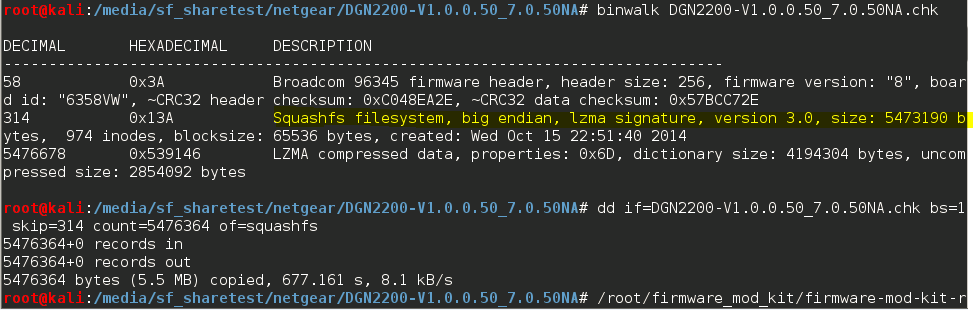
Binwalk output
As we can see in the Figure, the DGN2200 firmware is based on Linux and the file system is ‘Squashfs’ compressed with LZMA. We can use ‘dd’ utility to extract the ‘Squashfs’ file system from the image and use mod-firmware-kit to unpack the Squashfs, which will give us the extracted filesystems.
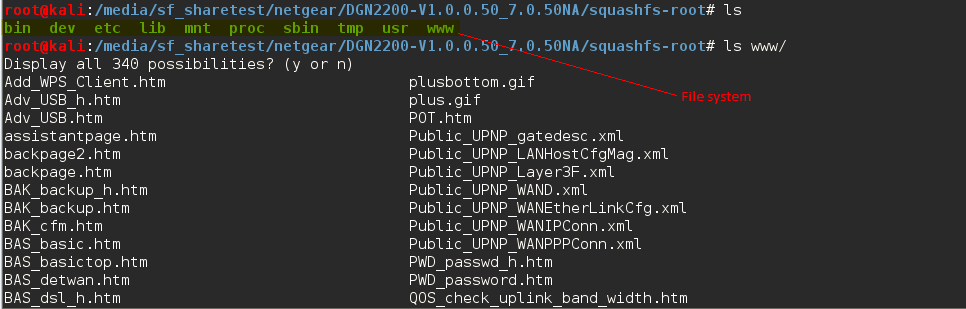
Extracted file system
Here we can see all the file system inside the firmware image. In order to access router’s web interface, user will need the login credentials. There was an unusual name of page that caught our eye “BSW_cxttongr.htm“. Same web page is also present in the firmware running on Netgear DGND3700.
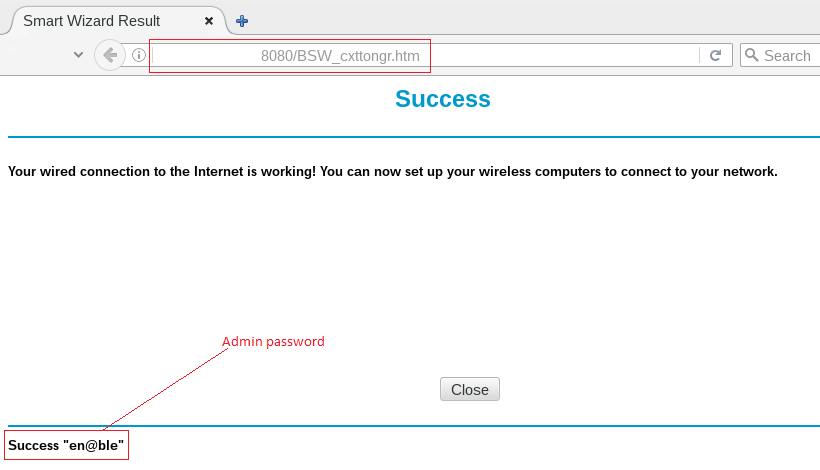
Admin’s password in clear text
So we tried to access “https://router-ip:8080/BSW_cxttongr.htm” page directly. It was a bit weird that we were not only able to access this page without any authentication but it also exposes admin’s password in clear text before it gets redirected to ‘bsw_vfysucc.cgi’. An attacker can use this password to gain administrator access of the targeted router’s web interface. The vulnerability has been assigned CVE-2016-5649.
We also extracted the firmware used for WNDR4500 in a similar manner. Netgear WNDR4500 is a dual band gigabit router, which broadcasts on two different frequencies: 2.4 GHz and 5 GHz. We found few web pages associated with the genie app. Genie app adds some capabilities over the Web GUI and can be accessed even when you are away from home. So when accessed https://[router-IP]:8443/genie_ping.htm or https://[router-IP]:8443/genie_ping2.htm or https://[router-IP]:8443/genie_ping3.htm
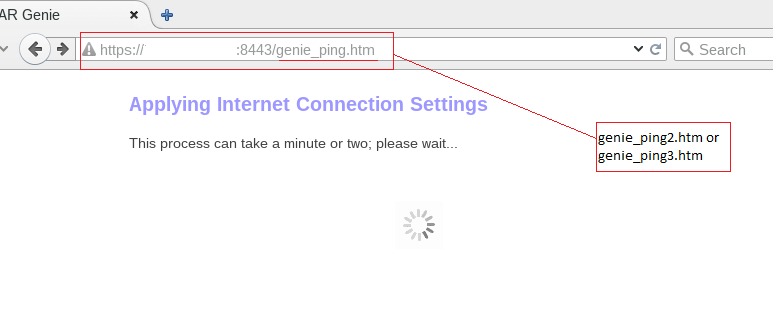
“genie_ping.htm” web page accessed without authentication
we were redirected to the ‘Congratulations2.htm’ page, which revealed some sensitive information such as 2.4GHz & 5GHz Wireless Network Name (SSID) and Network Key (Password) in clear text.
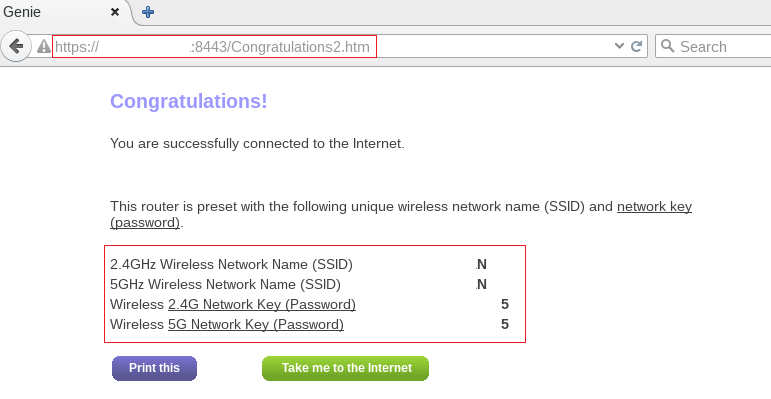
SSID & Network keys
An unauthenticated, remote attacker could exploit this vulnerability to obtain SSID & wireless key of the targeted router. Sometimes people may use same password for web interface also. This vulnerability has been assigned CVE-2016-5638.
Conclusion:
Attacks on routers and similar hardware are a lucrative business. If attackers can successfully exploit weaknesses, they can take full control of the device and manipulate it. Changing the DNS settings is one possible manipulation which would make it possible to divert all network traffic to a server which is controlled by the attackers and transform them into a botnet.
In accordance with Qualys responsible disclosure policy, we notified the vendor and they have released firmware version 1.0.0.52 for DGN2200 & 1.0.0.28 for DGND3700 to address this issue but WNDR4500v1 has reached the End of Life so they won’t be releasing any updates for this. We have released a QID 11749 to identify these assets remotely.