Introduction:
Google Project Zero recently disclosed an unpatched vulnerability that affects Microsoft Edge and Internet Explorer. This vulnerability is tracked as CVE-2017-0037. The disclosed PoC only demonstrates DoS attack on the target, but arbitrary code execution could also be possible. A PoC for the same is also available here.
Exploit:
The CVE-2017-0037 vulnerability, so-called ‘type confusion flaw’, in Layout::MultiColumnBoxBuilder::HandleColumnBreakOnColumnSpanningElement function in mshtml.dll. An attacker can exploit this vulnerability via a webpage containing a crafted Cascading Style Sheets (CSS) token sequence and crafted JavaScript code.
After loading the PoC in Internet Explorer, we observed following crash:
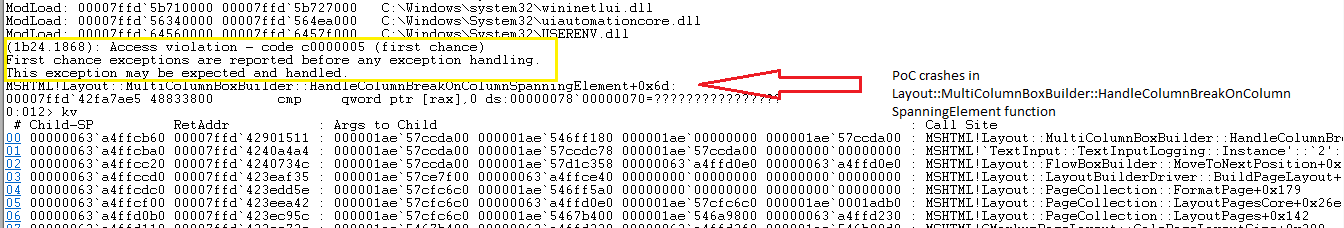
On 00007ffd`42fa7ae5, crash occurs because rax points to uninitialized memory (rax=0000007800000070). It may be possible for an attacker to change rax by modifying table properties such as border-spacing and the width of the ‘th’ element.
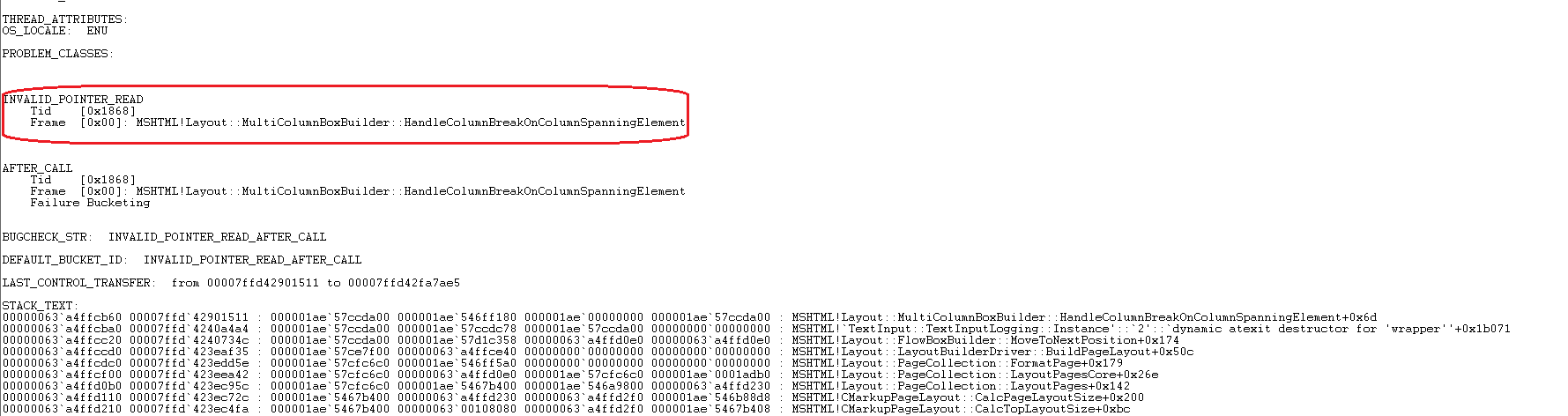
At the time of crash, we had following register values.
rax=0000007800000070 rbx=0000000000000064 rcx=000001ae54f07f18
rdx=0000000000000048 rsi=000001ae54f07f18 rdi=000001ae57d28000
rip=00007ffd42fa7ae5 rsp=00000063a4ffcb60 rbp=000001ae546ff0d0
r8=0000000000000000 r9=0000000000000000 r10=00000fffa851b048
r11=0000000100000514 r12=00007ffd436b65f0 r13=000001ae546b17a0
r14=000001ae57ccd500 r15=000001ae57ccd500
iopl=0 nv up ei pl nz na pe nc
cs=0033 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
MSHTML!Layout::MultiColumnBoxBuilder::HandleColumnBreakOnColumnSpanningElement+0x6d:
00007ffd`42fa7ae5 48833800 cmp qword ptr [rax],0 ds:00000078`00000070=????????????????
Conclusion:
At the time of writing, there were no updates provided by Microsoft to fix this vulnerability. We request our customers to scan their network with QID#91332 & QID#91333. For information about this vulnerability please follow up on ThreatProtect.