WordPress is a popular, open source, blogging tool and content management system based on PHP and MySQL. According to the latest BuiltWith statistics, a total of 18,619,652 live websites use WordPress! That figure is 5% of the total internet websites!
About three months ago with the advent of WordPress 4.7, support for REpresentational State Transfer (REST) API was released. This API provides anonymous, public as well as private data access to the website data using JSON (JavaScript Object Notation). This API is enabled by default on WordPress 4.7 and above versions. One of the easiest ways to detect this capability by looking for the following text in the Link header field of a WordPress website:
Link: <http://example.com/wp-json/>; rel="https://api.w.org/">
Graphically, this looks like:
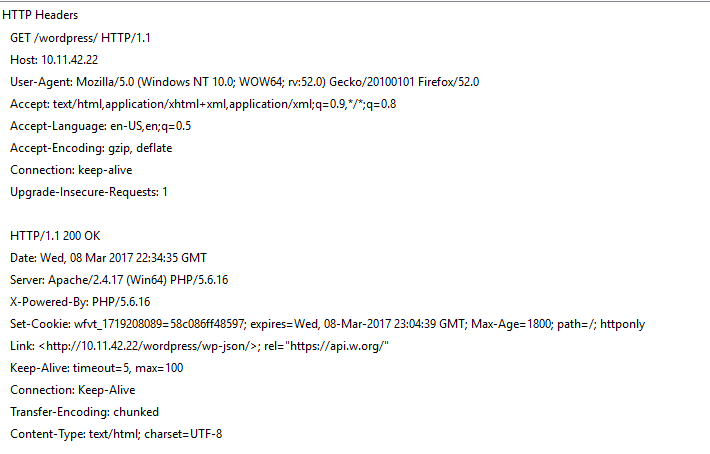
With this information over us, it is now easier to understand a user enumeration vulnerability that plagued WordPress 4.7 versions prior to 4.7.1.
This user enumeration vulnerability existed in the wp-includes/rest-api/endpoints/class-wp-rest-users-controller.php source file, which did not restrict access to sensitive user information. On a vulnerable machine, a simple request to the /wp-json/wp/v2/users/ URI would expose information about all users that have atleast one published post. This information includes a userid, username, gravatar hash and website URL. Vulnerable systems display the following behaviour:
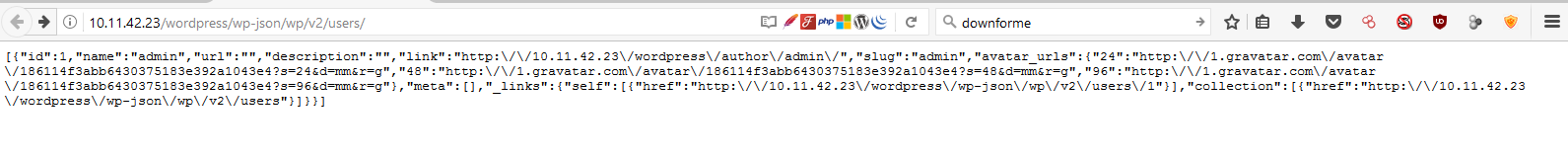
WordPress fixed this by ‘enforcing’ authorization via the “show_in_rest” directive. If this is enabled, user enumeration is no longer possible and we see a display similar to this:
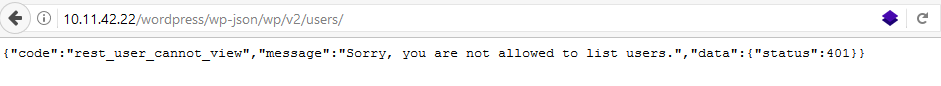
and we get a HTTP 401 Unauthorized response from the web server:
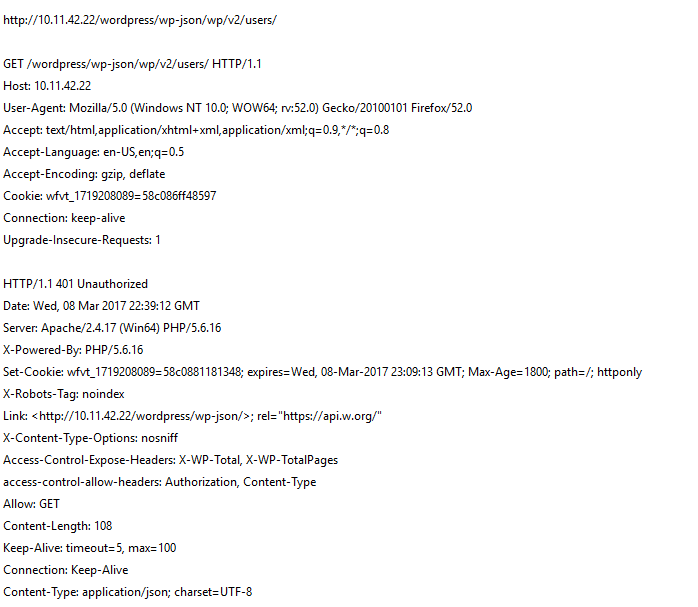
QualysGuard QID 11772 – WordPress REST API User Enumeration Vulnerability will alert you of any affected WordPress installations in your network.