The IP security camera industry has grown a lot over the past few years. From consumer-grade home IP security models to professional-grade models. Internet-connected video camera, or IP cameras, are widely used for security systems, offering the advantage that footage can be streamed anywhere remotely. However, anything connected to the Internet poses risks if not properly secured.
While working on other devices, I came across ACTi cameras. A quick search on shodan reveals 1500 plus online devices. So I decided to check if I could find any vulnerabilities in this device.
Affected Models:
ACTi D, B, I, and E series models running A1D-500-V6.11.31-AC firmware.
Vulnerability Details:
Weak Password Requirements – CVE-2017-3186
This appliance has a web based management console for admin and other users. Users can access this using IP address & port number.
Just to start with I opened a source code of the page and it appears that device uses non-random default credentials admin:123456
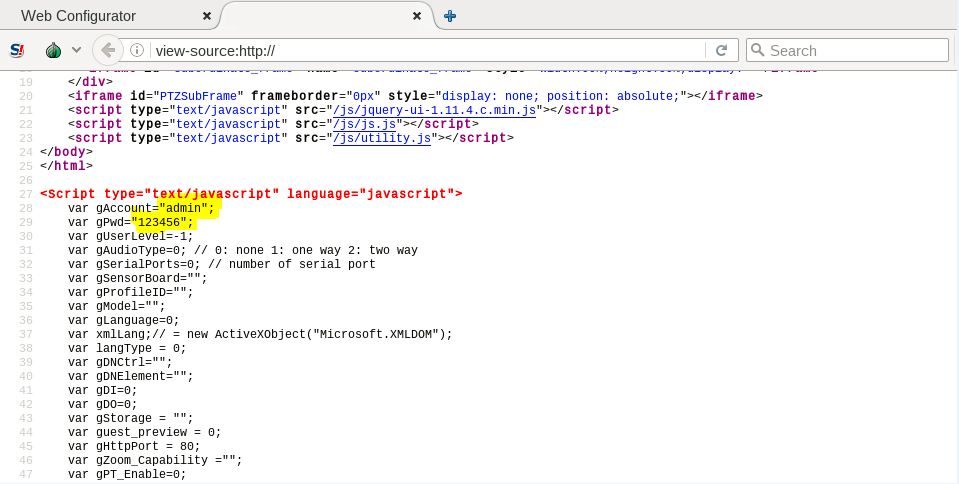
A remote attacker can take complete control of the device using default admin credentials. Vendor should force owners to change the default credentials as soon as the initial setup is completed.
Missing Authentication for Critical Function – CVE-2017-3184
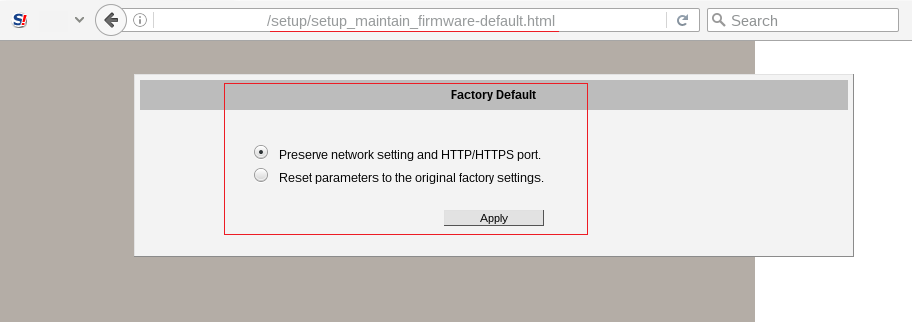
The web management console allows users to reset device to it’s factory setting. I thought of playing a bit around this to check if its access control mechanism is implemented properly. The device was failing to properly restrict access to the factory reset page so anyone can exploit this vulnerability by directly accessing the http://x.x.x.x/setup/setup_maintain_firmware-default.html page. This will allow an attacker to perform a factory reset on the device which may lead to a denial of service or reset device’s configuration to default settings.
Information Exposure Through Query Strings in GET Request CVE-2017-3185
While crawling the device, we observed that web application uses the GET method to process requests that contain sensitive information such as user account name and password.
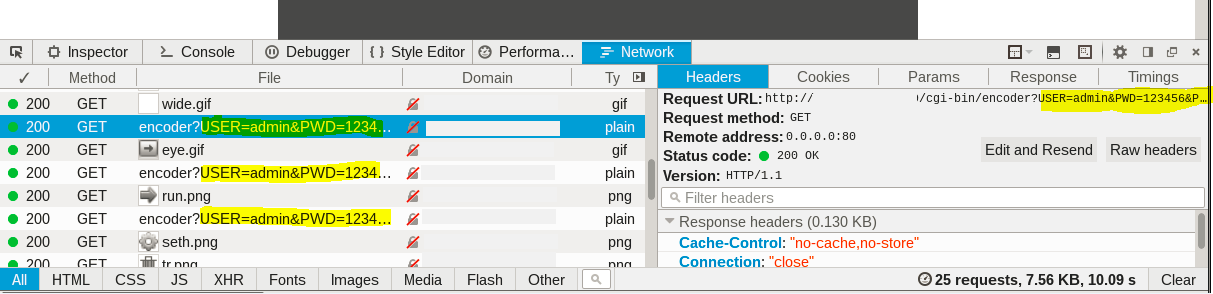
This information can be exposed through the browser’s history, referrers, web logs, and other sources.
Conclusion:
As per Qualys responsible disclosure policy, we notified the US-CERT and Vendor. US-CERT has released a vulnerability note VU#355151. The vendor has not confirmed the vulnerability and hasn’t released the patch yet. We have released the QID#11770 to detect these vulnerabilities remotely. As a best practice, we recommend users to change default passwords, update camera with the latest firmware and avoid exposing cameras to the Internet.