Four days ago, a potent proof-of-concept code exploiting an end-of-life software, the Microsoft Internet Information Services 6.0 was released. At this point of time – 4 days after the well publicized release of the PoC, the internet still has 607,134 publicly facing web servers! Of these, 286,068 servers are located in the United States. The March Netcraft web server statistics, state that 185 million sites are still running on Windows Server 2003 computers!
A Little Background:
Let’s first understand what PROPFIND method is. The PROPFIND Web Distributed Authoring and Versioning (WebDAV) method retrieves properties defined on the resource identified by the Request-URI. An example request:
PROPFIND /filename HTTP/1.1 Content-type: application/xml; charset="utf-8" Content-Length: XXX Depth: 0 ... <?xml version="1.0?> <a:propfind xmlns:a="DAV:"> <a:prop><a:getcontenttype/></a:prop>& <a:prop><a:getcontentlength/></a:prop>& </a:propfind>
It’s corresponding response:
<?xml version="1.0"?>
<a:multistatus
xmlns:b="urn:uuid:c2f41010-65b3-11d1-a29f-00aa00c14882/"
xmlns:a="DAV:">
<a:response>
<a:href>http://servername/filename</a:href>
<a:propstat>
<a:status>HTTP/1.1 200 OK</a:status>
<a:prop>
<a:getcontenttype>text/plain</a:getcontenttype>
<a:getcontentlength b:dt="int">1000</a:getcontentlength>
</a:prop>
</a:propstat>
</a:response>
</a:multistatus>
Vulnerability Analysis:
A combination of Microsoft Windows Server 2003 R2 with WebDAV and the HTTP PROPFIND Method enabled makes systems vulnerable to remote code execution. The only saving grace is that WebDav is not enabled by default on Windows 2003 systems.
The exploit formulated by Zhiniang Peng and Chen Wu transmits an overly long header beginning with incorrect Content-Length and “If: <http://localhost” headers to execute calc.exe on the targeted server. The If header defines a filter with a series of state lists. If a matching state list is found, only then the request succeeds, else it fails with a “412 Precondition Failed” client error response code. It also contains a Not directive. When submitted with a request, it performs a boolean operation of matching a state token. In this case, this If header requires that all operand resources must not be locked with locktoken:write1.
Pictographically, this is how it looks:
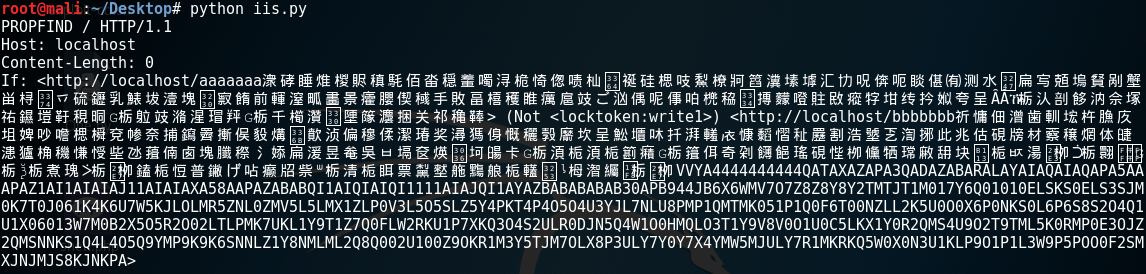
This in reality is a long string of Chinese characters to trigger the overflow, followed by the shellcode that executes calc.exe. Just imagine if this was a reverse TCP connect back shell code!
An example of a typical syntax of a valid IF header:
If: <http://domain/resource> () ([“ETag”]) <http://domain/random>([“ETag”])
The overflow occurs when the buffer from If request is copied into another buffer for the Not which isn’t large enough, creating an exception at the following location:
httpext!ScStoragePathFromUrl+0x360:
A successful exploit shows the following on the remote machine:
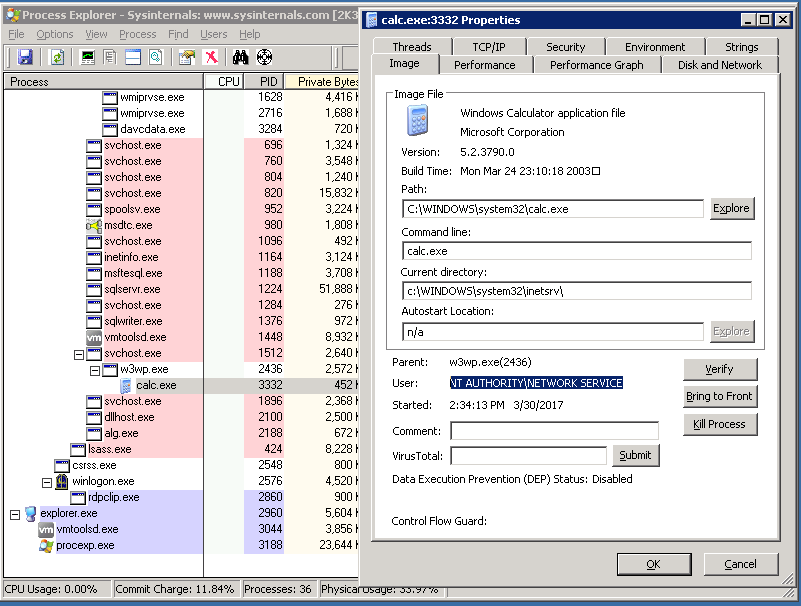
Non vulnerable systems respond with a “501 Not Implemented”, “403 Forbidden”, or “400 Bad Request”.
Conclusion:
The latest Apache Struts vulnerability S2-045/S2-046 were trojanized in a matter of days to run malware. With the number of systems online and the trivially available exploit code, it is suggested that you disable the PROPFIND method. Infact, you should really upgrade to the latest versions of Microsoft IIS.
It would be really interesting to see if Microsoft will make an exception this time and issue a patch for this vulnerability.
Qualys QID 87284 checks for vulnerable Microsoft IIS 6.0 versions – both via authenticated and unauthenticated checks.