A “ransomware” called “WannaCrypt” has locked thousands of computers in more than 150 countries. We have released a blog about this ransom ware last week. Here is a quick blog about a way to make your system immune to this ransom ware if you can’t install the patch for some reason.
Mutex And Indicator of Compromise
A lot of ransomwares implement an indicator internally to tell itself that if this system is already hacked or not. Same here, before doing everything else, “WannaCrypt” creates a mutex called “MsWinZonesCacheCounterMutexA0” on the system. As you can see below:
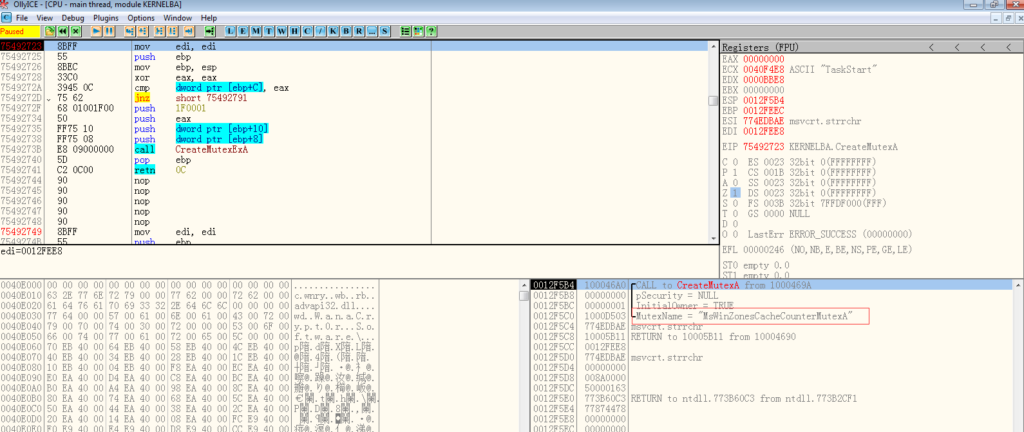
“MutexName” is “MsWinZonesCacheCounterMutexA” in my sample. The ransom ware checks the return value to see if the mutex is created or already exists.
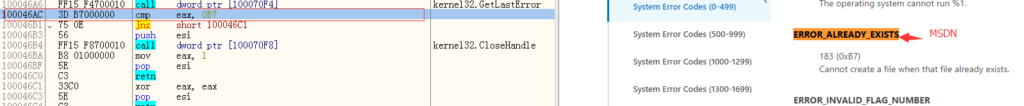
WannaCrypt compares the return value of “GetLastError” with 0xB7. If the mutex already exists then just won’t do anything.
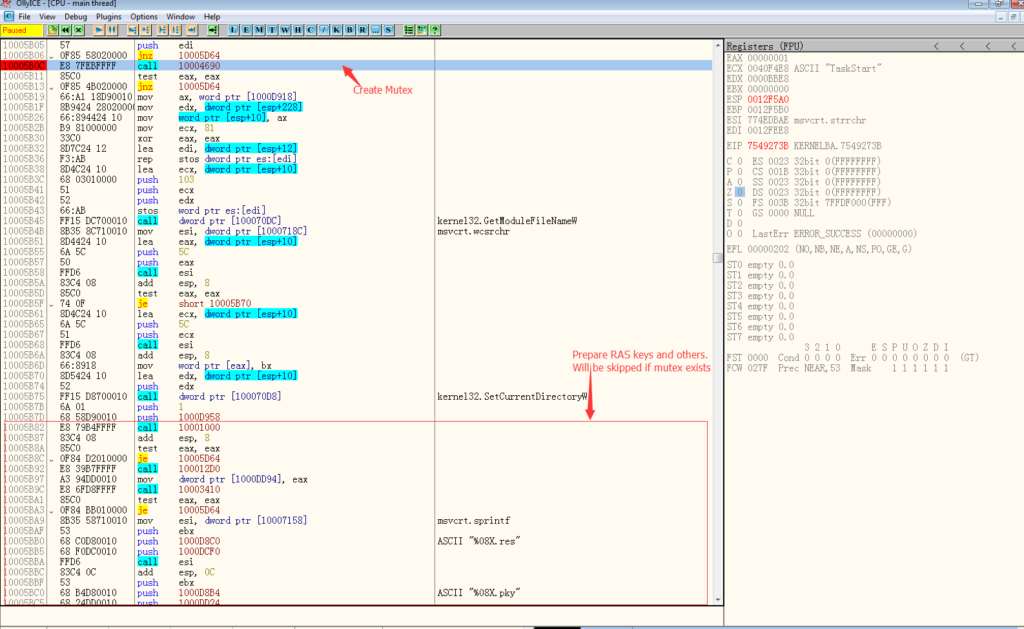
This mutex is also used again after the creation as many other researcher pointed out:
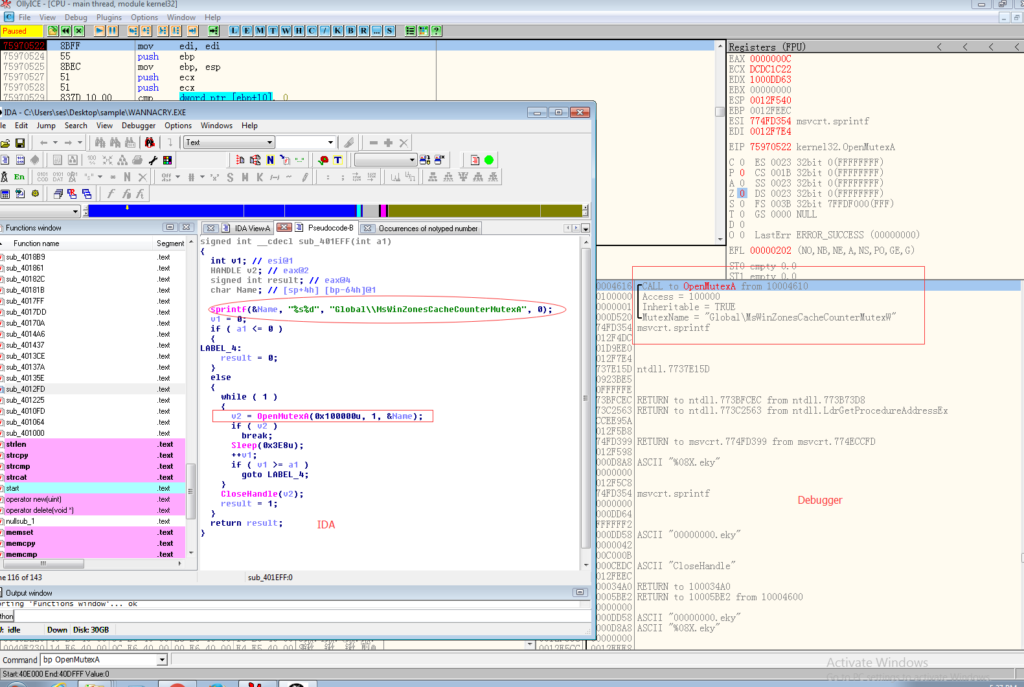
So creating mutex “MsWinZonesCacheCounterMutexA” will save you from being attack by WannaCrypt if you haven’t installed the patch.
How to do this?
There is a way to create a mutex on powershell. So all you need to do is start a command line on Windows. Then input “power shell” to get into powershell. Run the following command:
$createdNew = $False;
$mutex = New-Object -TypeName System.Threading.Mutex($true, "MsWinZonesCacheCounterMutexA", [ref]$createdNew);
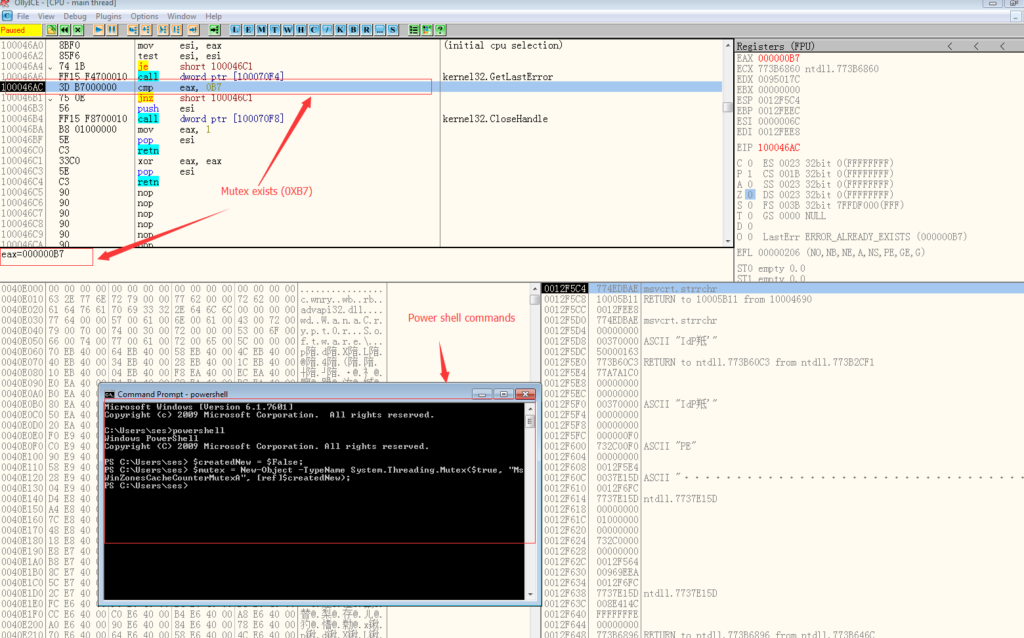
As you can see, after running these commands (Create the Mutex) on powershell. The ransom ware checks if the mutex is already there, if so it thinks that an instance of the ransomware is already running on the system. So it just quits. One thing to remember, you need to keep this command windows open to keep the mutex continually exists on your system.
Conclusion
This ransom ware is still wild spreading and attacking other Windows systems randomly. We have released the following QIDs to detect the vulnerabilities, backdoor and this ransom ware:
- QID 91345 to detect a missing MS17-010 patch.
- QID 1029 to detect WannaDecrypt0r ransomware artifacts.
- QID 91360 for detecting ETERNALBLUE.
- QID 70077 for detecting DOUBLEPULSAR backdoors.
For those who can’t apply the patch and workaround. Please use the method in this blog to protect yourself. Please continue follow up on ThreatProtect for more information regarding this ransomware.
Update: 5/16/2017:
As research going on, below is an updated list of mutex detected in latest WannaCrypt:
MsWinZonesCacheCounterMutexA
Global\MsWinZonesCacheCounterMutexA
Global\\MsWinZonesCacheCounterMutexA0
Global\WINDOWS_TASKOSHT_MUTEX
Global\WINDOWS_TASKCST_MUTEX