A critical remote code execution vulnerability impacting Samba was issued on Wednesday. The vulnerability exists in “SMB” protocol which is similar to “WannaCry”. All versions of Samba from 3.5.0 onwards are affected. The vulnerability allows a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it.
Samba has released a patch to address this vulnerability. For unsupported version of the software, Samba team also published a workaround.
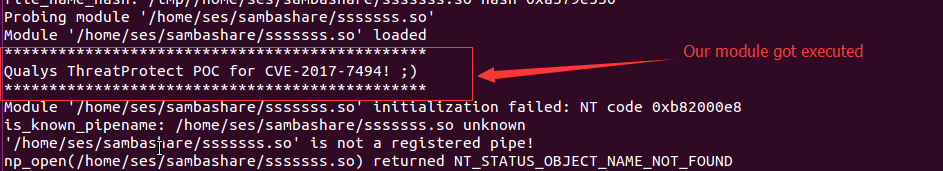
It’s fairly easy to exploit this vulnerability and there are already tons of exploiting tools available in the wild. So the risk of being exploited of this vulnerability is high. We strongly recommend customer to scan their network with following QIDs:
– 157456 Oracle Enterprise Linux Security Update for samba4 (ELSA-2017-1271)
– 157455 Oracle Enterprise Linux Security Update for samba (ELSA-2017-1270)
– 176040 Debian Security Update for samba (DSA 3860-1)
– 196791 Ubuntu Security Notification for Samba Vulnerability (USN-3296-1)
– 170004 SUSE Enterprise Linux Security Update for samba (SUSE-SU-2017:1393-1)
– 170003 SUSE Enterprise Linux Security Update for samba (SUSE-SU-2017:1392-1)
– 170002 SUSE Enterprise Linux Security Update for samba (SUSE-SU-2017:1391-1)
– 38671 Samba Writable Share Remote Code Execution Vulnerability
– 236361 Red Hat Update for samba3x (RHSA-2017-1272)
– 236360 Red Hat Update for samba4 (RHSA-2017-1271)
– 236359 Red Hat Update for samba (RHSA-2017-1270)
Reference:
https://www.samba.org/samba/security/CVE-2017-7494.html
https://github.com/hdm/metasploit-framework/blob/0520d7cf76f8e5e654cb60f157772200c1b9e230/modules/exploits/linux/samba/is_known_pipename.rb
https://www.exploit-db.com/exploits/42060/
https://github.com/omri9741/cve-2017-7494