The Orpheus’ lyre is a critical vulnerability in the implementation of the Kerberos protocol. The name has its roots in the Greek mythology where Orpheus plays his lyre to put Cerberus to sleep. Cerberus is the three headed dog the guards the entrance to the Underworld. Kerberos is named after Cerberus. Kerberos is heavily used by MS Active Directory for cryptographic authentication service. The vulnerability was found in Kerberos V5 (RFC4120) implementation, it is a client side vulnerability that allows that allows attackers to steal credentials remotely and can lead to remote privilege escalation. Point to note is that not all implementations of Kerberos are vulnerable. Currently two CVE’s have been issued for this bug: CVE-2017-8495, CVE-2017-11103. The vulnerability was discovered by Jeffrey Eric Altman (@jaltman),Nico Williams (@cryptonector),Viktor Dukhovni (@vdukhovni).
Kerberos Basics:
Kerberos is ticket-based authentication system. If a client wants to use a service it does not directly negotiate with it. Instead the client interacts with the Kerberos server to receive a ticket authenticating the client. Key Distribution Center (KDC) issues encrypted(symmetric) ticket. This contains name,expiration time, session key etc. The client creates an authenticator and sends it to the service. The service de-crypts the ticket to reveal the session key and decrypts the authenticator via using the session thereby validating the client.
Vulnerability:
As mentioned earlier the bug was found in version 5 of Kerberos. As with any authentication protocol the server and client exchange messages to exchange and negotiate authentication parameters. A section of the message is in plain-text. It is up to the implementer to make sure that data obtained from the message is checked for integrity and validity. The vulnerability lies in the KDC responses. The name of the client is present in both plain-text and in the encrypted section of a ticket, it contains the name,expire time, session key(provided by KDC). While parsing the ticket the code uses the name from the unencrypted part of the message instead. The expected behaviour is for the KDC-REP to extract the name from the encrypted section in the ticket.
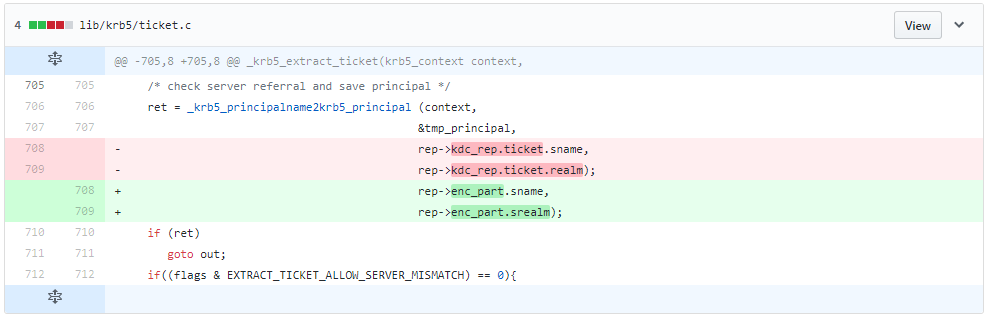
In the code snippet above we can see the name being extracted from the kdc_rep.ticket instead of enc_part. enc_part is the encrypted section of the ticket. To exploit this vulnerability the attacker needs to be in a position to launch an MITM attack posing as a service.
Mitigation:
As mentioned earlier it is a client side vulnerability, patching just the server is not enough. We request organizations to scan their networks with the following QIDS to detect vulnerable machines. The list of affected Microsoft Windows versions can be found here.
| QID | Description |
|---|---|
| 196847 | Ubuntu Security Notification for Heimdal Vulnerability (USN-3353-1) |
| 70079 | Samba Heimdal Kerberos Man-in-the-Middle Vulnerability |
| 91393 | Microsoft Windows Security Update July 2017 |
Please continue to follow ThreatProtect for more information on vulnerabilities.
Reference:
Orpheus’ Lyre
CVE-2017-8495 | Kerberos SNAME Security Feature Bypass Vulnerability
Fix KDC-REP service name validation
How the Kerberos Version 5 Authentication Protocol Works
CVE-2017-8495
CVE-2017-11103