Westermo provides a full range of industrial data communications (SCADA) solutions for demanding applications in the transport, water and energy markets among others. MRD devices provide resilient remote access and eliminate the need for costly site visits. With support for secure VPN communications, static and dynamic IP routing, NAT, port forwarding, OpenVPN (SSL VPN), and a stateful packet inspection firewall, the Westermo wireless mobile broadband routers provide secure, reliable communications.
I analyzed firmware for Westermo SCADA devices such as MRD-305-DIN, MRD-315, MRD-355 and MRD-455. The firmware’s file system compressed with LZMA and could be extracted.
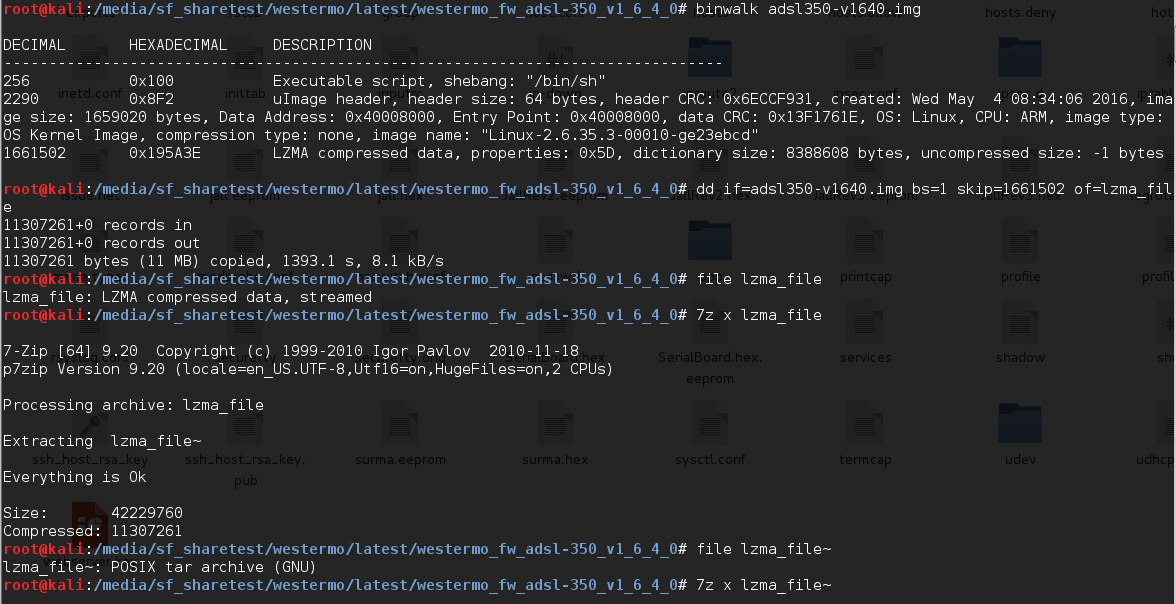
Affected Versions:
MRD-305-DIN, MRD-315, MRD-355 and MRD-455 versions older than 1.7.7.0
Hard-Coded Cryptographic Keys (CVE-2017-5816)
While analyzing firmware, I found hard coded SSH and HTTPS certificates and their private keys. Access to these certificates and private keys means that any attacker intercepting the traffic between the device and the users can decrypt the communication data. This may lead to the disclosure of admin credentials, which grants the attacker authenticated access to the device with administrative privileges.
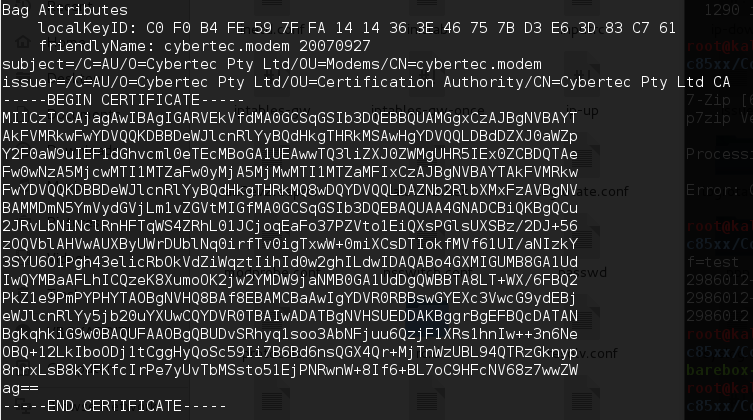
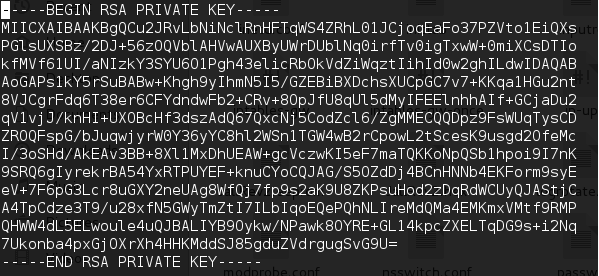
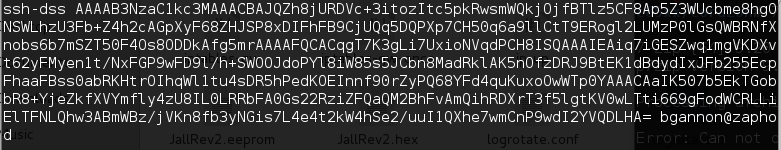
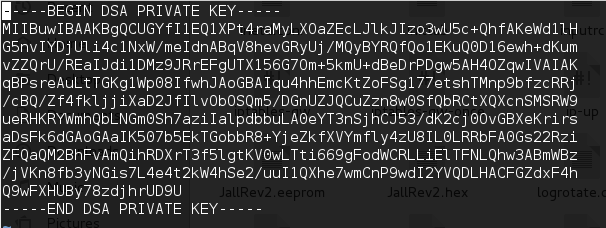
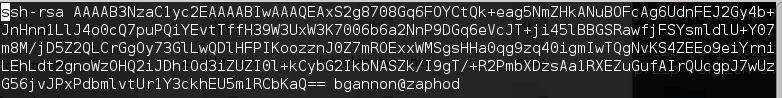
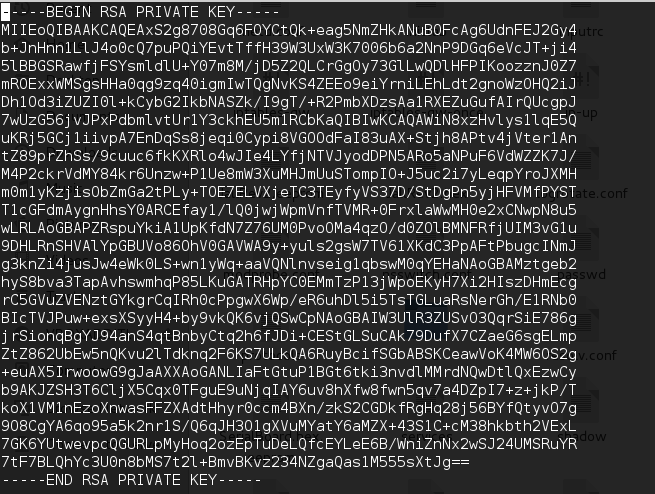
Use of Hard-Coded/Undocumented Credentials (CVE-2017-12709)
These firmwares also contain an undocumented “user” account, which could allow for unauthorized local low privileged access to the device. After cracking that hash, you will get a password “user“.
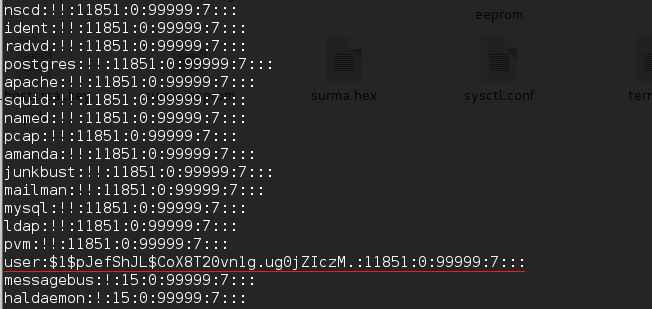
Cross-Site Request Forgery (CVE-2017-12703)
While working with vendor on above mentioned issues, vendor provided us with a testbed to test for potential vulnerabilities. I observed that firmware fails to implement any anti-csrf token on several pages. This may lead to unauthorized manipulation of the device if an authenticated user is accessing an infected web site concurrently to the device web management interface. Below HTML page will reboot the system.
<img alt="csrf image" src="https://x.x.x.x/config/reboot.asp?subm=Yes">
Conclusion:
As a best practice, allow only trusted users to have device access. In accordance with Qualys responsible disclosure policy, we notified the vendor and ICS-CERT. Please visit ICSA-17-236-01 and WEOS-15-08 for more information. QualysGuard detects Westermo MRD products with QID# 11858 and users are encouraged to keep their devices up to date.