Introduction:
A user after free (UAF) vulnerability in Apache HTTP causes the server to respond with a corrupted ALLOW header while replying to a HTTP OPTIONS request. The Apache httpd enables attackers to read data from process memory if Limit directive is set for user in .htaccess file or if the file contains mis-configurations. This vulnerability has been assigned CVE-2017-9798, it affects Apache HTTP Server through 2.2.34 and 2.4.x through 2.4.27. The vulnerability was disclosed by Hanno Böck.
Backgorund:
HTTP supports many headers apart from POST and GET and not all of them are always allowed. To know which headers are supported we can query the HTTP server using the OPTIONS header, to which the server responds with an ALLOW header which lists the headers the server supports or allows. A server admin can configure which headers to allowed using the Limit directive.
Vulnerablity:
A UAF occurs when a limit directive is set for an invalid HTTP method or a method that is not registered globally, in the .htaccess file. This mis-configuration causes the server to create a corrupted ALLOW header which includes memory chunks that may or may not contain confidential information. This vulnerability does not work with “*” OPTIONS target, you will need a specific path.
The vulnerability is not deterministic meaning the response is not always same, which is a good thing as the same attack wont work on all servers. A Simple way to test if a server is vulnerable is to use a Curl.
for i in {1..100}; do curl -sI -X OPTIONS
https://www.google.com/|grep -i “allow:”; done
A python PoC by Hanno Böck is also available.
Fix:
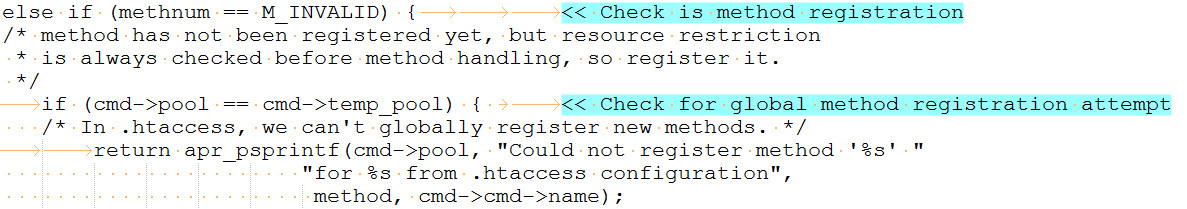
A fix was introduced in the function ap_limit_section() under httpd/httpd/branches/2.4.x/server/core.c. Methods are checked to see if they are registered and to the code disallows global registration of methods at run-time and allow methods registered at init time (httpd.conf).
Mitigation:
Patches for version 2.2.x and 2.4.x are available. We request organizations to scan their network with QID 351098 to detect vulnerable Amazon Linux distributions. Qualys will continue to add detections for other affected distributions.
Please continue to follow us on ThreatProtect for more information on this vulnerability.
References:
Optionsbleed – HTTP OPTIONS method can leak Apache’s server memory