Dynamic Data Exchange (DDE) is a protocol for exchanging messages between applications that refer shared data. The data can be exchanged on a one-time basis or as a continuous stream. DDE is not limited to just data exchange, it also allows applications to executed other external application within their process space. This feature has been exploited by attackers to gain command execution on target machines. The current attack scenario is email based. A user is receives an email attachment, usually an MS Word document with DDE field embedded within it. When the user open the document the underlying code in the DDE downloads additional malware on to the target machine and executes it.
Attack
This attack vector is not new and DDE support has been around since 2007. One of the earliest mentions of the attack were from 2016 which shows how the formula option in MS Excel can be used to achieve command execution. Following this research a similar approach was devised by Sensepost to achieve command execution using an MS Word document. This issue was disclosed to Microsoft who responded that “…. it is a feature and no further action will be taken, and will be considered for a next-version candidate bug”. Therefore there is no CVE associated with this issue.
The Biggest advantage for DDE attacks is the fact that macros need not be enabled. So it bypasses mail filters or policies that look for macro enabled attachments or documents. Fortunately this attack methodology is not straight forward. When a user opens DDE document they are presented with not one but 2 prompts before the DDE code can be evaluated and executed.
The first prompt is for requesting permission to update the document using the link mentioned on the DDE field.
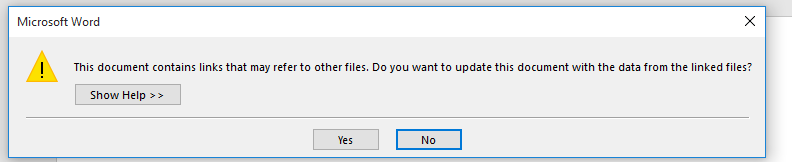
The second prompt is for permission to execute external application.
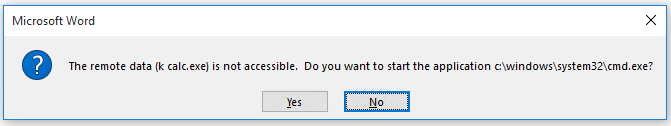
When user clicks ok calc.exe is executed.
Incidents
APT28 also known Fancy Bear is using DDE attacks to download malware on to the target machine, this attack was disclosed by McAfee. The user is receives an email attachment with embedded DDE. It invokes powershell to download base64 encoded script. The decoded the script downloads Seduploader, this is an information gathering malware. Seduploader downloads either X-Agent or Sedreco.
The DDE attack is being used to distribute Locky ransomware. The Malspam is spread via the Necurs botnet. Similar to APT28 attack chain upon opening the document cmd.exe is used to invoke PowerShell, it downloads a base64 encoded script that calls back to a remote server to download Locky ransomware.
Mitigation
To address this Microsoft has introduced “Windows Defender Exploit Guard” as part of Windows 10 Fall Creators Update (1709). Which provides a feature called Attack Surface Reduction (ASR) which is designed to block behaviors exhibited by malicious documents. By blocking such behaviors ASR claims to protect against zero-day attacks similar to CVE-2017-11292, CVE-2017-8759 and attacks that utilize DDE. ASR can:-
- Block Office apps from creating executable content
- Block Office apps from launching child process
- Block Office apps from injecting into process
- Block Win32 imports from macro code in Office
- Block obfuscated macro code
- Block malicious JavaScript, VBScript, and PowerShell codes that have been obfuscated
- Block JavaScript and VBScript from executing payload downloaded from internet
To configure ASR please refer here. As mentioned earlier current DDE attacks use cmd.exe to launch PowerShell, all of these execute as child processes and therefore will be blocked by ASR as it blocks Office apps from launching child process. For non-1709 operating systems Microsoft recommends disabling the DDE feature either by the user interface or modifying registry keys. Please refer the Microsoft Security Advisory for more details on how to disable DDE. Please not that improper use of registry editor may have serious implication on the machine.
Qualys Detection
Please scan your network with QID 110307. To detect vulnerable targets on your network. The QID checks registry keys under “HKEY_CURRENT_USER\Software\Microsoft\Office” (HKCU) to check if DDE is enabled. If the registry is set then DDE is disabled. Setting this registry key will prevent automatic update of links via DDE, OLE.
| Registry | Office Version <version> | Key | Value | Office Product |
| HKCU\Software\Microsoft\Office\<version>\Excel\Security | 12.0,14.0,15.0,16.0 | WorkbookLinkWarnings | 2 | MS Excel |
| HKCU\Software\Microsoft\Office\<version>\Word\Options\WordMail | 14.0,15.0,16.0 | DontUpdateLinks | 1 | MS Outlook |
| HKCU\Software\Microsoft\Office\<version>\Word\Options\vpref | 12.0 | fNoCalclinksOnopen_90_1 | 1 | |
| HKCU\Software\Microsoft\Office\<version>\Word\Options | 14.0,15.0,16.0 | DontUpdateLinks | 1 | MS Word |
| HKCU\Software\Microsoft\Office\<version>\Word\Options\vpref | 12.0 | fNoCalclinksOnopen_90_1 | 1 |
Microsoft Publisher documents with embedded word documents are protected if DDE is disabled for MS Word.
If the target machine OS is Windows 10 1709 it checks registry entry “HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Windows Defender Exploit Guard\ASR” for key “ExploitGuard_ASR_Rules=1” which shows that ASR is enabled it checks under “HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Windows Defender Exploit Guard\ASR\Rules” if the rule required to block DDE are enabled. Each ASR rule has unique GUID the QID checks if they are present.
| Rule | GUID |
| Block Office applications from creating child processes | D4F940AB-401B-4EFC-AADC-AD5F3C50688A |
| Block Office applications from creating executable content | 3B576869-A4EC-4529-8536-B80A7769E899 |
| Block Office applications from injecting code into other processes | 75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84 |
| Block Win32 API calls from Office macro | 92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B |
| Block execution of potentially obfuscated scripts | 5BEB7EFE-FD9A-4556-801D-275E5FFC04CC |
Please continue to follow Qualys Threat Feed for information on DDE attacks.
References
Macro-less Code Exec in MSWord
Microsoft Security Advisory 4053440
US-CERT:Microsoft Releases Security Advisory on Dynamic Data Exchange (DDE)
Windows Defender Exploit Guard: Reduce the attack surface against next-generation malware
Enable ASR
Using Dynamic Data Exchange