In the month of August a buffer overflow vulnerability was discovered in the in the “Microsoft Equation Editor”, the vulnerability has been assigned CVE-2017-11882. As the name suggests it is used for inserting and editing equations MS Office documents. The component in question was compiled without SafeSEH,NX,DEP,ASLR,CFG. All of which protect the machine from a wide variety of overflow based vulnerabilities, ROP attacks etc. An attacker can exploit this vulnerability to gain arbitrary code execution in the context of the current user. Since its disclosure Microsoft has addressed this issue during the patches released in the month of November 2017. The vulnerability was disclosed by Embedi.
Vulnerability
As mentioned in the earlier section the vulnerability is a type of buffer overflow, more precisely a stack overflow. An equation in an Office documents is an OLE object and therefore contains data streams that represent the data of the OLE object. The equation is also represented as streams. It starts with a header to describe the type of the subsequent data , in this case it is MTEF data which contains an MTEF header followed by records which represent various aspects of the equation.
There are many types of records we are interested in font name record, as the name suggests it contains the name of the font to be used. The record consists of 4 fields tag, typeface number,style,font name. The font name is represented as a null terminated string. And this data will be parsed by the document viewer to render the equation OLE object. The is the target for exploitation. Microsoft Equation Editor(EQNEDT32.EXE) copies this data in to an internal buffer, but it fails to check the size of the buffer before copying.
Exploitation
The attacker can craft a custom document such that the font name overflows the buffer assigned to hold it. We overflow the buffer to overwrite the return address saved in the current stack frame and point it to an attacker specific location. The target function here is 0x004164fa which calls 0x00416352, this function returns a single character from the string containing the “font name”. The received character is stored in a buffer addressed in ECX.
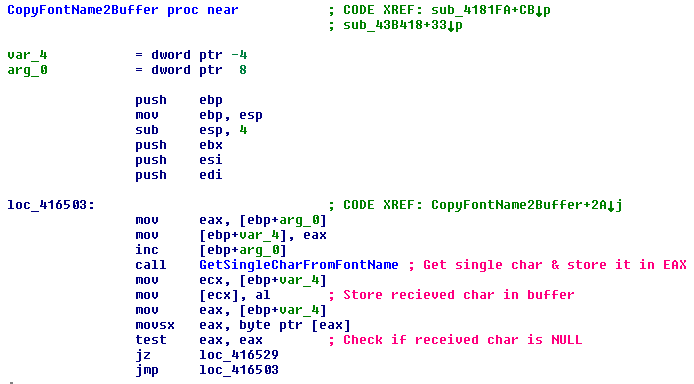
EQNEDT32.EXE uses WinExec() to execute commands, So it is convenient for us to point the return address to this address. By tracing the execution flow we find the string that allegedly represents the font name. In the image below we can see the string that will overflow the buffer.
0:000> db 0029036a
0029036a 63 6d 64 2e 65 78 65 20-2f 63 20 63 61 6c 63 2e cmd.exe /c calc.
0029037a 65 78 65 20 41 41 41 41-41 41 41 41 41 41 41 41 exe AAAAAAAAAAAA
0029038a 41 41 41 41 41 41 41 41-41 41 41 41 12 0c 43 00 AAAAAAAAAAAA..C.
The last four bytes of the string will overwrite the EIP value stored on the stack frame.
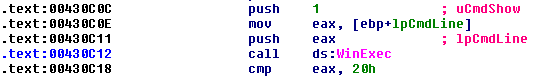
This string is referred by many functions, we are interested in the function at offset 0x1160f. This function calculates the length of the received string and copies it in to a local char array without checking for bounds condition, in doing so it overwrites the stored EIP on the stack. In the image below we can see the original EIP overwritten to 0x00430C12.
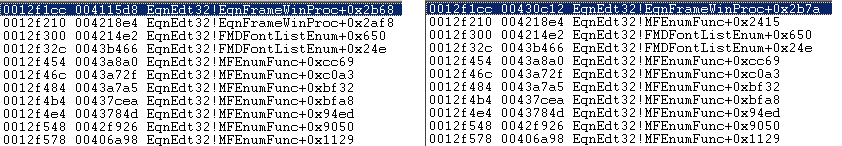
The overflowed buffer stores the arguments for WinExec on the stack frame . When function returns the EIP will point to WinExec().
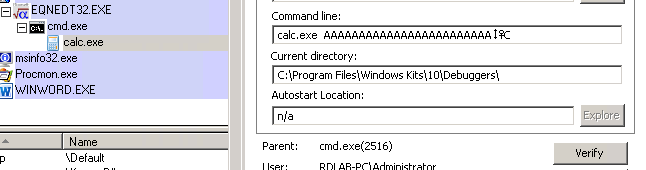
In the image above we can see that EQNEDT32.EXE executes as a separate process not under the context of the MS Office. This means that the protection mechanisms for MS Office may not be able to prevent exploits targeting this vulnerability.
There are reports that this vulnerability is being exploited in the wild via malicious .rtf document attachments. When the target machine opens the malicious document they can
- Execute commands via cmd.exe
- Use mshta.exe
- Use cscript.exe to execute scripts
- Use regsvr32.exe to register or unregister DLLs
Fix
The vulnerable function EQNEDT32.EXE+0x164FA now requires the buffer length to be passed as a function argument. The loop to copy the string terminates if null is encountered or the loop counter reaches the end of the buffer.
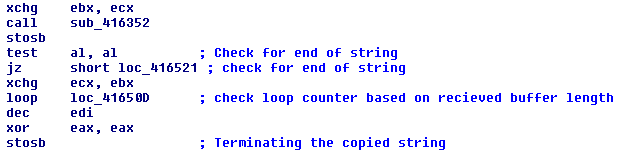
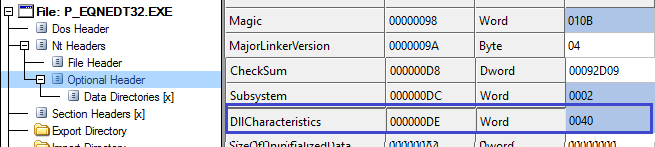
The updated EQNEDT32.EXE has ASLR enabled. This makes it difficult for the exploit to call WinExec() using hard-coded address.
Mitigation
Please install the latest patches provided by Microsoft to address this issue. Scan your network using QID 110308 to detect vulnerable machines. The QID checks if the respective patch has been installed or not, it obtains this information from the registry. If patch cannot be applied then please try to disable Equation editor.
Please continue to follow Qualys Threat Protection for more information on this vulnerability
References
Skeleton in the closet. MS Office vulnerability you didn’t know about
Microsoft Office Memory Corruption Vulnerability
CVE-2017-11882