A flaw in Out-of-Order execution mechanism allows user level programs to leak addresses of kernel and process memory space. This vulnerability can be exploited to bypass KASLR as well as CPU security features like SMAP,SMEP,NX and PXN. It can be exploited to bypass OS process isolation. The issue affects processors from Intel, AMD ,ARM, Samsung and Qualcomm processors. AMD has mentioned that their processors are not completely affected by this flaw (especially CVE-2017-5754 )as they do not allow speculative references. Intel plans to officially disclose the vulnerability next week. Three CVE’s have been assigned to track this vulnerability –
| CVE | Description |
| CVE-2017-5715 | Systems with microprocessors utilizing speculative execution and indirect branch prediction may allow unauthorized disclosure of information to an attacker with local user access via a side-channel analysis.[branch target injection] |
| CVE-2017-5753 | Systems with microprocessors utilizing speculative execution and branch prediction may allow unauthorized disclosure of information to an attacker with local user access via a side-channel analysis.[bounds check bypass] |
| CVE-2017-5754 | Systems with microprocessors utilizing speculative execution and indirect branch prediction may allow unauthorized disclosure of information to an attacker with local user access via a side-channel analysis of the data cache.[rogue data cache load] |
Background
– Context Switching & Address space isolation: Under normal execution the OS kernel intervenes to carry out certain operation required by a user level process. This is achieved by context switching, the control flow of the program is transferred to the kernel and back to the user level process after the operation is complete. To achieve this efficiently the kernel is mapped in to all processes on the system. This kernel portion of the process spaces must remain invisible and inaccessible to the user level process. So an exception is raised when a user-level program tries to access a kernel memory address.
– Out-of-Order execution: It is performance optimization mechanism that tries to reduce latency in situations where the processor is waiting for a result to be available to continue execution. Instead of waiting/stalling the processor looks at the instructions ahead, makes a prediction (by Branch predictor) about which execution path will be taken and executes any instructions that do not have any dependencies or unresolved conditions/branches, this is called speculative execution. The results from these executions are not committed to architecture as in program reachable registers, instead they are cached and committed only when the appropriate conditions are resolved, if the prediction is wrong then they are rolled back.
– Memory Hierarchy: When the processor needs data from memory, it first checks if the L1 cache if data is found in the cache it is cache hit else cache miss Intel processors have 3 caches. Each core having L1 and L2 and L3 shared among all cores.
Vulnerability
The vulnerability is described as side effect of speculative execution, the processor uses branch prediction to predict which direction the execution flow will take before a branch or condition can be evaluated. Based on this prediction it speculatively executes instructions on this path that have no unresolved branches and no instruction based dependencies. The results from these executions are cached. If the prediction is correct then the results are committed to the architecture. But if the prediction is wrong then these results are rolled back by clearing the cache.
The cache that holds the interim results is vulnerable to side-channel attacks. An attacker can use cache attacks like Flush+Reload to detect changes in cache due to out-of-order memory lookups. This is achieved using high resolution timers, to measure the time differences in cache operations.
Exploitation
Meltdown and Spectre are the names given to the exploits that target these vulnerabilities. Spectre targets CVE-2017-5753 and CVE-2017-5715, Meltdown targets CVE-2017-5754. Both exploits use side-channel attacks to achieve their goal.
Meltdown is a CPU vulnerability, therefore is it OS independent. It is capable of accessing arbitrary system memory from a user-land process, if successful an attacker can read the entire kernel memory which could and mostly likely will include confidential data. Meltdown effectively bypasses the address space isolation between process and kernel, as it is able to locate the kernel memory it bypasses KASLR as well.
The gist of the attack is a user-land process tries to access a kernel memory address, under normal conditions an exception is raised and the process may be terminated. But if this “access instruction” is executed speculatively then its result is in the cache till the exception/branch condition is resolved. As mentioned earlier the cache that holds this interim results is vulnerable to side-channel attacks. An attacker can leverage Flush+Reload cache attacks.
Spectre targets other processes and arbitrarily reads its memory space, it bypasses OS process isolation,containerization,just-in-time (JIT) compilation and protection measure for cache timing/side-channel attacks. Spectre causes a target process to speculatively execute instructions that do not execute under normal circumstances, it needs the processor’s branch predictor to choose the wrong execution path. Spectre trains (actually mis-trains) the processors branch predictor to choose an execution path of the attackers choice . There 3 different approaches to attack using Spectre.
- Trick the target process in to speculatively executing instructions that leak the information from within the target process memory space.
- Trick the target process in to speculatively executing instructions that are part of a ROP chain that can read the entire target process memory space.
- Bypass browser sandboxing. Upon successful exploitation, attacker can read data from browser memory space.
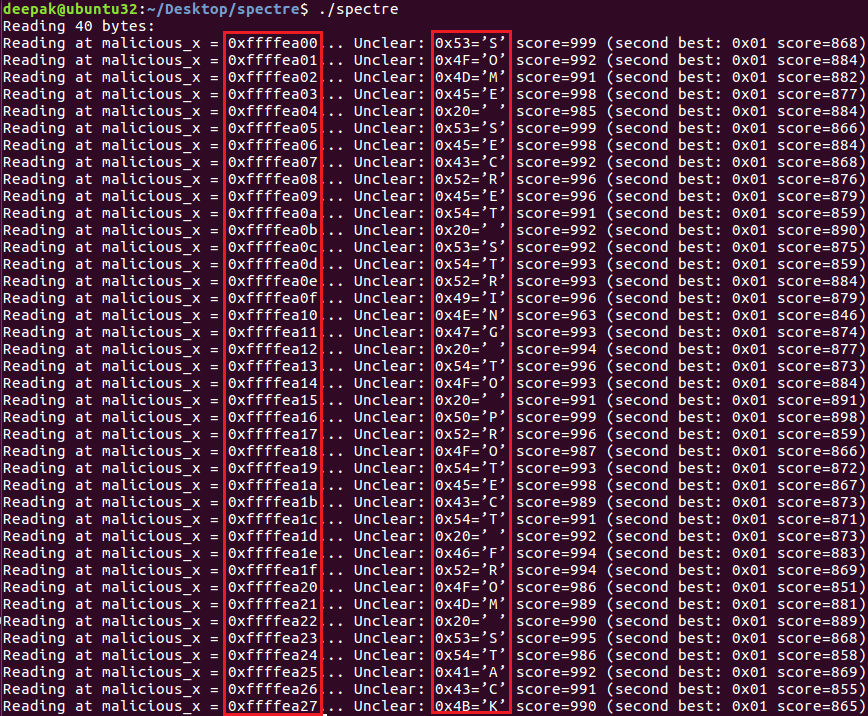
The image shows the Spectre PoC reading memory. The exploit contains a target function victim_function() which accepts a size parameter and checks its validity against size of array1 via an if statement, if the value is true it stores the value of array1[x] * 512 in to array2.
Then it calls readMemoryByte() to train the branch predictor by calling victim_function() with valid argument and then calls the target function with an invalid size value. It calculates the time difference for CACHE_HIT_THRESHOLD.
Mitigation
Currently this issue is addressed at OS level. As per the Linux patch update Kernel Page Table Isolation has been implemented to address this issue, this has been implemented for 64-bit ARM Linux as well. The idea is to isolate the kernel and the process completely by mapping them to different address spaces. Context switching in this scenario is costly and may slow down the machine. This technique was initially introduced as a counter measure for attacks where KASLR is bypassed.
Qualys Detection
Please scan your network using the QIDs listed below. Qualys will continue to add more detections as vendors release their patches to address Meltdown and Spectre.
| CVE(s) | QID | Description |
| CVE-2017-5753, CVE-2017-5715, CVE-2017-5754 | 236596 | Red Hat Update for kernel (RHSA-2018:0017)(Spectre/Meltdown) |
| 236595 | Red Hat Update for kernel (RHSA-2018:0011)(Spectre/Meltdown) | |
| 236594 | Red Hat Update for kernel (RHSA-2018:0010)(Spectre/Meltdown) | |
| 236593 | Red Hat Update for kernel (RHSA-2018:0009)(Spectre/Meltdown) | |
| 236592 | Red Hat Update for kernel (RHSA-2018:0008)(Spectre/Meltdown) | |
| 236591 | Red Hat Update for kernel (RHSA-2018:0007)(Spectre/Meltdown) | |
| 157615 | Oracle Enterprise Linux Security Update for Oracle Linux 7 kernel (ELSA-2018-0007)(Spectre/Meltdown) | |
| 157616 | Oracle Enterprise Linux Security Update for Oracle Linux 6 kernel (ELSA-2018-0008)(Spectre/Meltdown) | |
| 91424 | Microsoft Security Update for SQL Server (Meltdown and Spectre) | |
| 91423 | Microsoft Windows Security Update (Meltdown and Spectre) | |
| 91425 | Microsoft Edge Security Update for January 2018 (ADV180002) (Spectre/Meltdown) | |
| 100326 | Microsoft Internet Explorer Security Update for January 2018 (ADV180002) (Spectre/Meltdown) | |
| 100326 | Microsoft Internet Explorer Security Update for January 2018 (ADV180002) (Spectre/Meltdown) | |
| 197006 | Ubuntu Security Notification for Firefox Vulnerabilities (USN-3516-1) | |
| 256346 | CentOS Security Update for kernel (CESA-2018:0008) (Spectre/Meltdown) | |
| 256345 | CentOS Security Update for kernel (CESA-2018:0007) (Spectre/Meltdown) | |
| 170629 | SUSE Enterprise Linux Security Update for the Linux Kernel (SUSE-SU-2018:0011-1) (Spectre/Meltdown) | |
| 170630 | SUSE Enterprise Linux Security Update for the Linux Kernel (SUSE-SU-2018:0012-1) (Spectre/Meltdown) | |
| 170628 | SUSE Enterprise Linux Security Update for the Linux Kernel (SUSE-SU-2018:0010-1) (Spectre/Meltdown) | |
| CVE-2017-5753, CVE-2017-5715 | 216142 | VMware ESXi 6.5 Patch Release ESXi650-201712103-SG,ESXi650-201712101-SG Missing (KB 2151102)(Spectre) |
| 216138 | VMware ESXi 6.0 Patch Release ESXi600-201711101-SG, ESXi600-201711103-SG, Missing (KB 2151126)(Spectre) | |
| 370662 | VMware Workstation and Fusion Multiple Vulnerabilities (VMSA-2017-0018,VMSA-2017-0021,VMSA-2018-0002) | |
| 370712 | Mozilla Firefox Spectre Vulnerability (mfsa2018-01)(Spectre) | |
| CVE-2017-5715 | 236590 | Red Hat Update for microcode_ctl (RHSA-2018:0013)(Spectre) |
| 236589 | Red Hat Update for microcode_ctl (RHSA-2018:0012)(Spectre) | |
| 236588 | Red Hat Update for linux-firmware (RHSA-2018:0015)(Spectre) | |
| 236587 | Red Hat Update for linux-firmware (RHSA-2018:0014)(Spectre) | |
| 236608 | Red Hat Update for qemu-kvm (RHSA-2018:0023)(Spectre) | |
| 236607 | Red Hat Update for qemu-kvm (RHSA-2018:0024)(Spectre) | |
| 236606 | Red Hat Update for qemu-kvm (RHSA-2018:0026)(Spectre) | |
| 236605 | Red Hat Update for qemu-kvm (RHSA-2018:0027)(Spectre) | |
| 236604 | Red Hat Update for libvirt (RHSA-2018:0030)(Spectre) | |
| 236603 | Red Hat Update for libvirt (RHSA-2018:0031)(Spectre) | |
| 236602 | Red Hat Update for libvirt (RHSA-2018:0032)(Spectre) | |
| 236601 | Red Hat Update for microcode_ctl (RHSA-2018:0034)(Spectre) | |
| 236600 | Red Hat Update for microcode_ctl (RHSA-2018:0035)(Spectre) | |
| 236599 | Red Hat Update for microcode_ctl (RHSA-2018:0036)(Spectre) | |
| 236598 | Red Hat Update for libvirt (RHSA-2018:0029)(Spectre) | |
| 236597 | Red Hat Update for kernel (RHSA-2018:0037)(Spectre) | |
| 170626 | SUSE Enterprise Linux Security Update for kernel-firmware (SUSE-SU-2018:0008-1) (Spectre) | |
| 170625 | SUSE Enterprise Linux Security Update for qemu (SUSE-SU-2018:0007-1) (Spectre) | |
| 170624 | SUSE Enterprise Linux Security Update for ucode-intel (SUSE-SU-2018:0006-1) (Spectre) | |
| 170635 | SUSE Enterprise Linux Security Update for kvm (SUSE-SU-2018:0019-1) | |
| 216139 | VMware ESXi 5.5 Patch Release ESXi550-201709101-SG, ESXi550-201709102-SG Missing (KB 2150882)(Spectre) | |
| 157617 | Oracle Enterprise Linux Security Update for Oracle Linux 7 microcode_ctl (ELSA-2018-0012)(Spectre) | |
| 157618 | Oracle Enterprise Linux Security Update for Oracle Linux 6 microcode_ctl (ELSA-2018-0013)(Spectre) | |
| 170627 | SUSE Enterprise Linux Security Update for microcode_ctl (SUSE-SU-2018:0009-1) (Spectre) | |
| CVE-2017-5754 | 351154 | Amazon Linux Security Advisory for kernel: ALAS-2018-939 (Meltdown) |
| 91426 | Microsoft Windows Security Update for Windows Server (ADV180002) (Spectre/Meltdown) | |
| 176245 | Debian Security Update for Linux (DSA 4078-1) (Meltdown) | |
| 370710 | Apple macOS High Sierra 10.13.2 Not Installed (Meltdown) | |
| 176245 | Debian Security Update for Linux (DSA 4078-1) (Meltdown) |
Please continue to follow Qualys Threat Protection for more information on this vulnerability.
References
Reading privileged memory with a side-channel
Intel Responds to Security Research Findings
CERT
Kernel Page Table Isolation – Linux patch
arm64: Unmap the kernel whilst running in userspace (KAISER)
KASLR is Dead: Long Live KASLR