On 21 March 2018 Drupal released a statement that a major vulnerability was reported. They have rated this vulnerability as critical. As per their statement “exploits might be developed within hours or days”, Due to the severity of the issue Drupal is releasing patches for unsupported version as well. CVE-2018-7600 has been assigned to track this issue. Drupal security advisory SA-CORE-2018-002 will be released (on March 28th 2018 between 18:00 – 19:30 UTC) to address this vulnerability. The patch will address issues in Drupal 7.x, 8.3.x, 8.4.x, and 8.5.x.
Vulnerability
A remote code execution attack due to improper user request validation/sanitization. Upon exploiting CVE-2018-7600 an attacker can take over the complete website. The user only needs to visit the page and does not require any privilege.The bug is in Drupal subsystems in Drupal/Core/DrupalKernel.php. To address this issue a new class is defined in Drupal/Core/Security/RequestSanitizer.php in Drupal 7.x ‘/includes/request-sanitizer.inc’. This class calls sanitize() to remove invalid keys from:
– Get query string
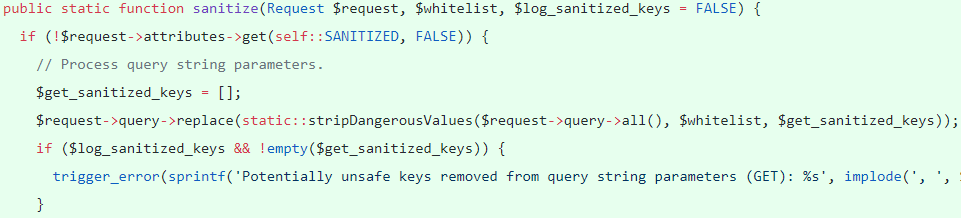 – Request body
– Request body
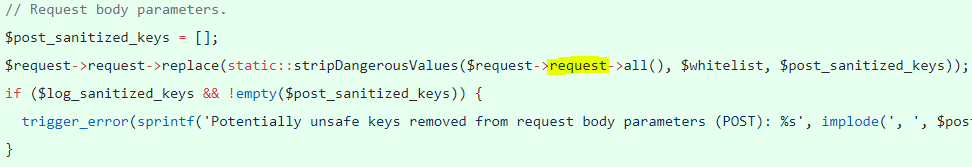 – Cookie
– Cookie
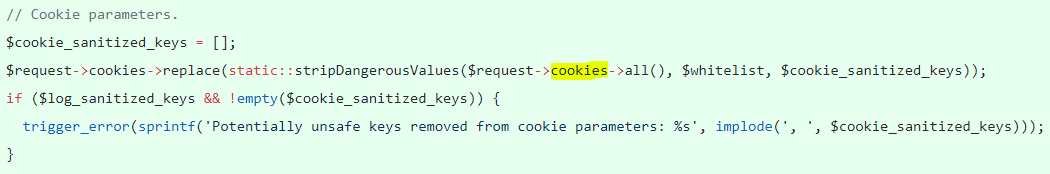
The keys are sanitized based on a white-list, sanitize() calls stripDangerousValues() to unset invalid keys that are not present in the whitelist and creates an array of unset keys for logging if required.
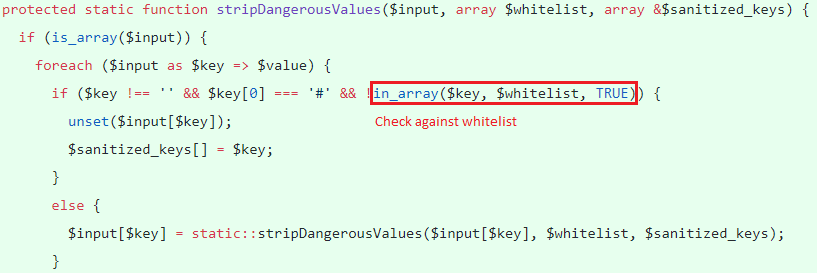
The function unsets the key in question if it is not empty, does not start with ‘#’ and not present in the pre-defined whitelist.
Mitigation
We request our customers to apply the latest patches as provided by Drupal. Qualys has released QID:11942 to detect vulnerable machines. The QID uses BlindElephant engine to detect Drupal version. The QID will not flag if only code changes were applied and base version remains the same.
Updates
– An exploit is publicly available
Please continue to follow Qualys Threat Protection for more coverage on this vulnerability.
Reference
CVE-2018-7600
Drupal 7 and 8 core highly critical release on March 28th, 2018 PSA-2018-001
Drupal core – Highly critical – Remote Code Execution – SA-CORE-2018-002
Uncovering Drupalgeddon 2
WAS and Newly Discovered Drupal Vulnerability